Mogelijke waarschuwingen tijdens de installatie of update van TWS
IBKR's Trader Workstation (TWS) is een globaal handelssysteem dat klanten een reeks online handelstools biedt. TWS kan worden geïnstalleerd op Windows, Mac OS X en Linux en heeft een Java Runtime Environment (Java-runtime-omgeving - JRE) nodig. Wanneer u TWS installeert, worden daarom ook Java-bestanden gedownload die nodig zijn om een Java Virtual Machine (Java virtuele machine - JVM) te gebruiken.
Tijdens het installatie-of updateproces van TWS kan bepaalde software, zoals antivirustoepassingen bijvoorbeeld, soms een waarschuwing geven en voorkomen dat het proces wordt voltooid. U kunt deze waarschuwingen en andere berichten in dit geval gerust negeren en de installatie van het handelsplatform voltooien.
Inhoudsopgave
Het downloaden van het TWS-installatieprogramma en de updates
De TWS installatieprogramma's zijn beschikbaar in de downloadsecties van ibkr.com of de regionale websites van IBKR en hebben een digitale handtekening en zijn verzegeld volgens alle veiligheidsprocedures die vereist zijn door de industriestandaarden en bevatten geen schadelijke codes of processen. Dezelfde industriestandaarden worden gebruikt voor de TWS updates, die automatisch worden gedownload en geïnstalleerd bij het opstarten van TWS (alleen indien er een update beschikbaar is). Desalniettemin, raden wij u aan voorzichtig te zijn als u een waarschuwing heeft ontvangen. Als u van plan bent het TWS-installatiebestand op uw machine te bewaren voor eventueel toekomstig gebruik, moet u ervoor zorgen dat dezelfde voorzorgsmaatregelen voor de bescherming van gegevens tegen virussen en malware erop worden toegepast.
Waarom krijg ik een waarschuwing wanneer ik TWS installeer of wanneer de automatische TWS-update wordt uitgevoerd?
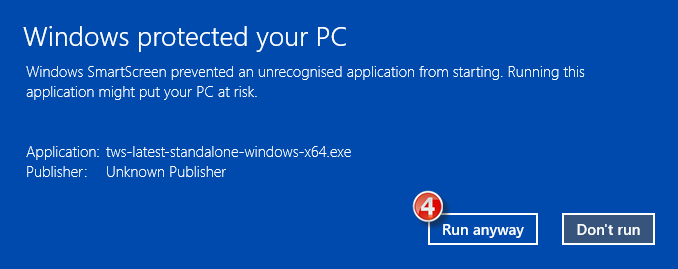
U krijgt mogelijk een waarschuwing te zien (zoals Afbeelding 1, dit is echter ter illustratie) waarna uw beveiligingssysteem wacht op uw input over hoe het verdachte bestand moet worden verwerkt. U heeft meestal de mogelijkheid om het bestand in quarantaine te plaatsen, te verwijderen, eenmalig te negeren of er een permanente uitzondering voor te maken.
Houd er rekening mee dat uw antivirusprogramma het TWS-installatiebestand of sommige van zijn componenten automatisch in quarantaine kan plaatsen of verwijderen zonder u om bevestiging te vragen en zonder u een waarschuwing te geven. Dit zou echter alleen mogen gebeuren als uw antivirus is ingesteld om specifiek op deze manier te reageren.
Afbeelding 1.
Wat moet ik doen wanneer ik een waarschuwing ontvang?
Indien u een waarschuwing ontvangt tijdens de installatie of update van TWS, raden wij u de volgende stappen aan:
1. Verwijder het TWS-installatieprogramma en download het opnieuw van de algemene of regionale website van IBKR
a) Verwijder het TWS-installatiebestand dat al op uw computer staat en verwijder het vervolgens ook uit uw prullenbak (maak uw prullenbak leeg)
b)Klik in de onderstaande tabel op de TWS-downloadlocatie die overeenkomt met uw locatie
| Locatie | TWS-downloadlocatie |
| VS | https://www.ibkr.com |
| Azië / Oceanië | https://www.interactivebrokers.com.hk |
| Indië | https://www.interactivebrokers.co.in |
| Europa | https://www.interactivebrokers.co.uk https://www.interactivebrokers.eu |
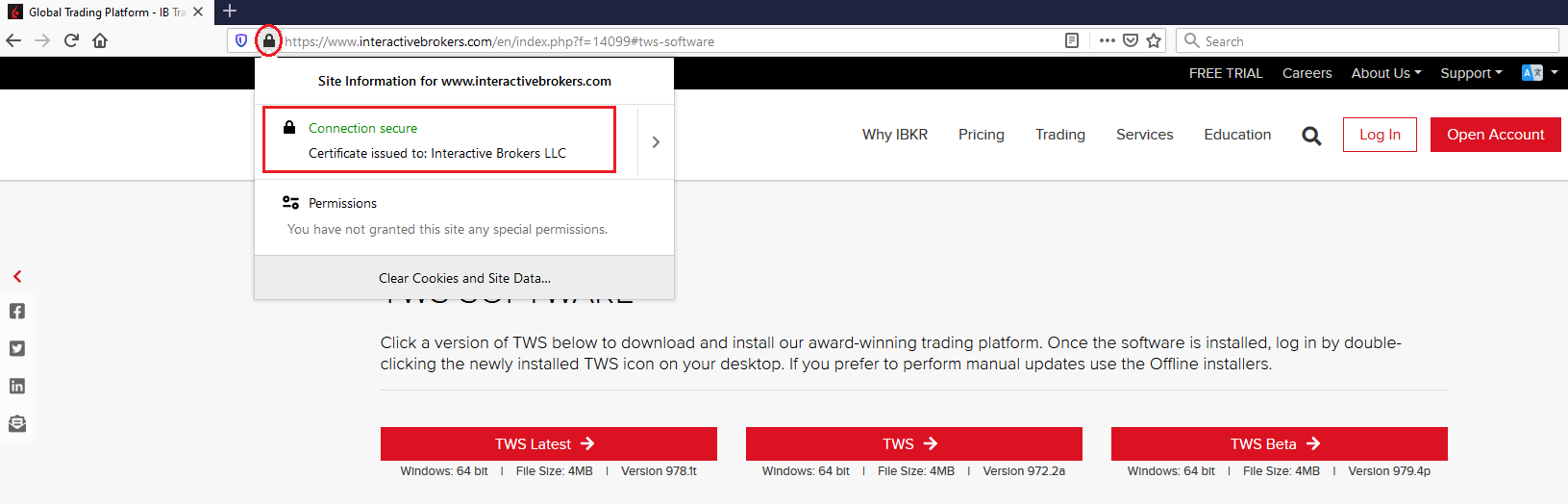
c) Controleer het certificaat van de website. De meeste internetbrowsers zullen u onmiddellijk waarschuwen als het websitecertificaat ongeldig, gecompromitteerd of verlopen is. Als u toch handmatig de geldigheid van het websitecertificaat wilt controleren, klik dan op het hangslotje naast het adres (URL) en controleer of de verbinding veilig is en er geen beveiligingswaarschuwing is (zie Afbeelding 2 hieronder).
Afbeelding 2.
d) Klik op de knop met de TWS-versie die u wilt gebruiken en download het TWS-installatieprogramma opnieuw
2. Controleer de digitale handtekening van het TWS-installatiebestand dat u heeft gedownload
Normaal gesproken krijgt u onmiddellijk een beveiligingswaarschuwing als de digitale handtekening van een bestand gecompromitteerd is. Als u echter een handmatige controle wilt uitvoeren, gaat u als volgt te werk, afhankelijk van uw besturingssysteem:
Windows
a) Open vanuit Windows Verkenner uw Downloads-map of de map waar u het TWS-installatieprogramma heeft bewaard.
b) ) Klik met de rechtermuisknop op het TWS-installatiebestand, selecteer Eigenschappen en klik dan op het tabblad "Digitale handtekeningen"
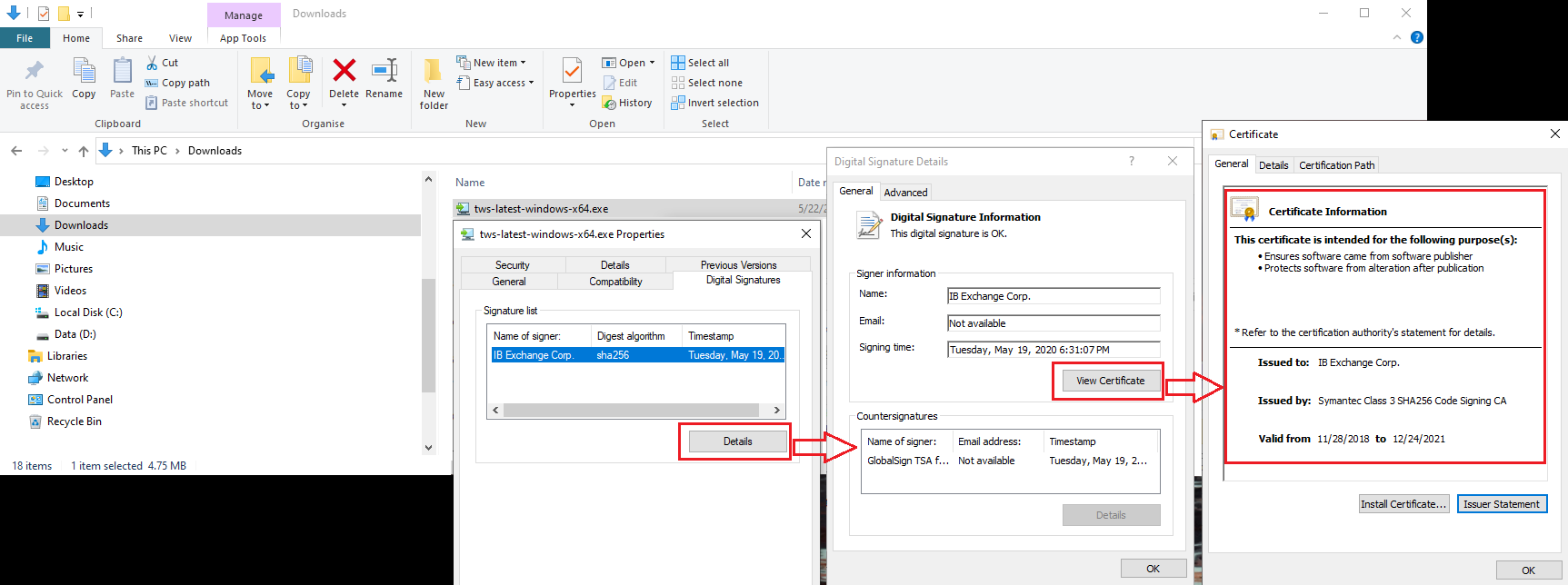
c) Klik op "Details" en op "Certificaat bekijken"om de status van het certificaat en de ondertekenaar te controleren. De legitieme ondertekenaar is "IB Exchange Corp." (Zie Afbeelding 3 hieronder)
Afbeelding 3.
Mac OS X
a) ) Klik op het vergrootglas (Spotlight) rechtsboven in uw scherm en typ Terminal. In de zoekresultaten selecteert u Terminal app
b) Typ cd Downloads en druk op Enter
c) Typ codesign -dv --verbose=4 tws-latest-macosx-x64.dmg en druk op Enter. Let op: de naam van het bestand (tws-latest-macosx-x64.dmg) kan verschillen naargelang de TWS-versie die u heeft gedownload. Vervang indien nodig de bestandsnaam in het commando door de juiste naam.
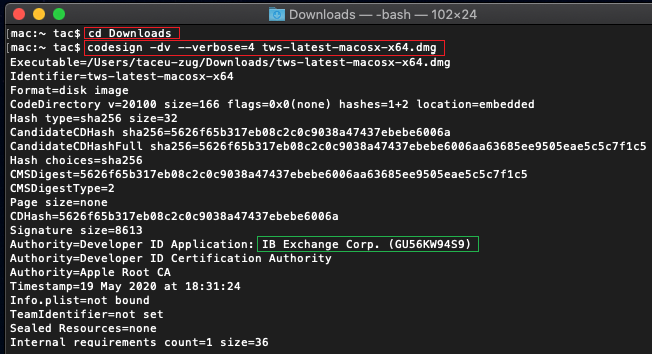
d)Controleer de uitvoer van het commando en zorg ervoor dat de "Developer ID Application" "IB Exchange Corp." is (zie Afbeelding 4 hieronder)
Afbeelding 4.
3. Start het TWS-installatiebestand dat u heeft gedownload.
Nadat u het TWS-installatiebestand opnieuw heeft gedownload en u er zeker van bent dat het bestand authentiek is (punten 1. en 2. hierboven), kunt u doorgaan met de installatie. Mocht u nog steeds een waarschuwing van uw antivirus ontvangen, dan kunt u deze gerust als vals positief beschouwen en negeren. Mocht u hulp nodig hebben bij deze stap, ga dan direct door naar de volgende paragraaf.
Hoe kan ik aangeven dat een waarschuwing vals-positief is?
Alle moderne beveiligingssystemen hebben de mogelijkheid om uitzonderingen in te stellen, om zo vals-positieve meldingen aan te pakken. Een uitzondering is een regel die de antivirusengine dwingt een specifiek bestand of proces niet te scannen. Dat specifieke bestand of proces wordt dan als veilig beschouwd en er worden geen verdere waarschuwingen voor verstuurd.
De procedure voor het maken van een uitzondering kan variëren, afhankelijk van de beveiligingssoftware die u gebruikt. kunt een tijdelijke of permanente uitzondering rechtstreeks vanuit de waarschuwingspop-up aanmaken of u moet er handmatig een aanmaken vanuit een specifieke sectie in het hoofdconfiguratiepaneel.
Als u niet zeker bent hoe dat moet, raden wij u aan uw antivirusdocumentatie te raadplegen.
Zodra u een uitzondering heeft ingesteld voor het TWS-installatiebestand of voor het TWS-updateproces, worden deze niet langer geblokkeerd en kunnen zij hun respectieve taken uitvoeren.
Wat kan ik nog meer doen als ik twijfels heb of als mijn systeem zich vreemd gedraagt?
Als u vermoedt dat uw computer gecompromitteerd of geïnfecteerd is, raden wij u aan een volledige systeemscan uit te voeren. Doorgaans kunt u rechts klikken op het antiviruspictogram op de onderste taakbalk (in Windows) of op de bovenste menubalk (in MacOS) waarna u de optie ziet om een volledige systeemscan te starten. U kunt deze taak ook starten vanuit het hoofdvenster van het antivirusprogramma. Als u niet zeker bent hoe dat moet, raden wij u aan uw antivirusdocumentatie te raadplegen.
Technische achtergrond
Hoe scant mijn beveiligingssysteem de bestanden die ik van het internet download?
Moderne antivirus- en anti-malwareprogramma's herkennen bedreigingen op de volgende manieren:
Scannen op basis van handtekening: de antivirusscanner zoekt naar een specifiek patroon van bytes dat eerder als kwaadaardig of op zijn minst verdacht is gecatalogiseerd. Het antivirusprogramma kan ook bestandshandtekeningen ('hash' genoemd) vergelijken met een database van bekende bedreigingen ('virusdefinities' genoemd).
Gedragsanalyse: het antivirusprogramma detecteert specifieke acties die afzonderlijk misschien geen bedreiging vormen, maar die, wanneer ze met elkaar in verband worden gebracht, vergelijkbaar zijn met de gebruikelijke activiteiten van kwaadaardige software (bv. het vermogen van een code om zichzelf te repliceren of te verbergen, extra bestanden van internet te downloaden, contact op te nemen met externe hosts via internet, het register van het besturingssysteem te wijzigen).
Heuristische detectie: de scanner de-compileert de code of voert deze uit binnen een virtuele, beperkte omgeving. Vervolgens worden de door de code uitgevoerde acties geclassificeerd en gewogen aan de hand van een vooraf gedefinieerde, op gedrag gebaseerde regelset.
Cloudgebaseerde bescherming en machine learning: dit zijn relatief nieuwe technieken. Het te analyseren bestand wordt naar de cloud van de antivirus/beveiligingssysteemleverancier gestuurd, waar geavanceerde algoritmen een diepgaande analyse maken van de authenticiteit en het gedrag van de code.
Zijn deze scanmethoden dan onfeilbaar?
Moderne bedreigingen zijn zeer geavanceerd en kunnen, net als biologische virussen, de code en handtekeningen muteren. Bovendien worden elke dag nieuwe malwares en exploits gecreëerd die zich snel over het internet verspreiden. De bovengenoemde methoden voor het herkennen van bedreigingen zijn daarom niet onfeilbaar, maar kunnen wel een hoog percentage herkenning van malware garanderen wanneer zij worden gecombineerd.
Terwijl op handtekeningen gebaseerde technieken zeer succesvol zijn in het herkennen van bekende bedreigingen en minder vatbaar zijn voor vals-positieven, zijn zij niet zo efficiënt in het herkennen van onbekende malware of mutaties van bestaande malware. Op dit gebied presteren de gedrags- en heuristische methoden veel beter, hoewel zij vatbaarder zijn voor vals-positieven omdat hun detectie niet gebaseerd is op het overeenkomen van de code, maar op een zekere mate van interpretatie en dus onzekerheid.
De term "vals-positief" wordt gebruikt wanneer een beveiligingssysteem een onschuldig bestand of proces als malware classificeert.
Referentie:
Please Upgrade TraderWorkstation (TWS)
On December 9, 2021, a critical security vulnerability in Apache's Log4j software library was disclosed, (now commonly referred to as “Log4Shell”). Log4j is very broadly used in a wide variety of consumer and enterprise services, websites, applications, and devices to log security and performance information. The vulnerability allows an unauthenticated remote actor to take control of an affected system and execute arbitrary code on it. The ubiquitous nature of Log4j and the ease of exploitation of the vulnerability makes this threat not only critical but also nearly universal.
WHAT IS IBKR DOING TO PROTECT ITS CLIENTS?
We are actively working, with high priority, to mitigate the threat on several levels:
- We have patched all our servers accessible externally (from the Internet) with a version of Log4j that is not susceptible to this vulnerability.
- We have upgraded our Trader Workstation (TWS) software and our TWS installers with a version of Log4j that is not susceptible to this vulnerability.
- We have updated our security infrastructure (including network firewalls, application firewalls, intrusion detection tools, etc.) with the latest protection measures that help detect and block cyber-attacks that attempt to exploit the Log4j vulnerability.
- We continue our ongoing efforts to fully identify and patch any impacted internal systems (those that are not accessible from the Internet).
- We continue monitoring the evolving industry threats and adopt additional mitigation measures as needed.
ACTION REQUIRED
We are committed to providing a secure environment for your assets and trading activities. To that end, we request that our clients give priority to the use of the LATEST TWS version, which will auto-update. Should you have the STABLE or any OFFLINE version, which does not auto-update, please ensure that you take the necessary steps to keep your TWS in line with the latest security fixes.
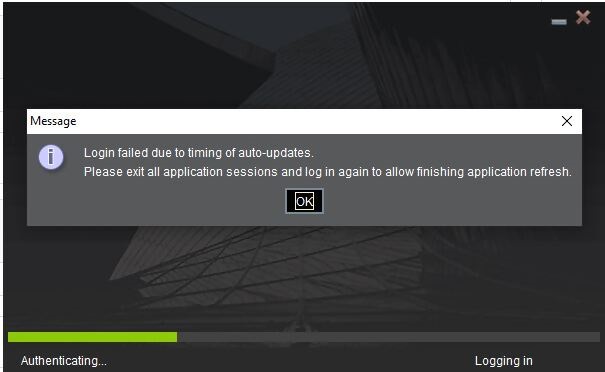
How to solve "Login failed due to timing of auto-updates."
When you use certain versions of the Trader Workstation (TWS), you may receive the error message "Login failed due to timing of auto-updates." When this occurs, the platform will not start up and will not display the login window.
In this article we will outline the possible causes of this error along with the resolution steps.
We provide two TWS installation types: the TWS and the Offline TWS
-
The TWS automatically updates itself each time a new platform release is available.
-
The Offline TWS does not update itself automatically. Should you want to update the offline TWS, you would have to download and run the newly released Offline TWS installer from our website.
What can cause this error?
A. Another TWS session is running on your computer
B. A program is blocking the platform auto-update process
C. Your firewall is blocking the platform auto-update process
D. You have not launched the TWS for an extended period of time
A. Another TWS session is running on your computer
If another TWS session is running on your computer (either visibly or in the background), the updater process will not be able to update the application core files since they are in use. In this case, please follow the steps below:
If you are able to locate the TWS window on your Desktop or on the tray bar, bring it to the foreground and use the TWS top menu File -> Exit to close it. Then launch the TWS again and wait for the automatic update to complete. You should then see the TWS login window where you can enter your credentials.
If you are unable to locate the TWS window, please consider that the TWS process may still be running. This usually happens when the TWS was not properly closed or unresponsive. In this case you can use the task manager to terminate the process. According to your operating system, please follow the steps below:
Windows
1. Press CTRL+ALT+DEL on your keyboard and select Task Manager
2. Under the tab "Processes", please check if there is a process named TWS.exe or update.exe running. If you find any, click on it to highlight it and click on the button "End task" or "Force Quit" on the bottom right corner of the Task Manager window
3. If for some reason, you are unable to terminate the process through the Task Manager, restart your computer
Mac
1. Press CMD+OPT+ESC on your keyboard
2. Select the "Trader Workstation" process and click on "Force Quit"
3. If for some reason, you are unable to terminate the process, restart your computer
B. A program is blocking the platform auto-update process
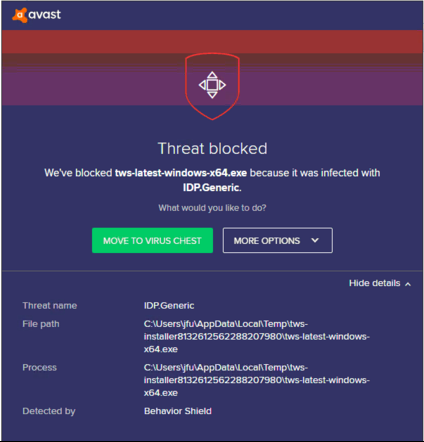
A program on your computer, such as an antivirus, may erroneously interpret the behavior of the TWS updater process as suspicious or threatening and prevent it from running or from connecting to the TWS repository server. If this occurs please refer to IBKB 3424 for further recommendations and steps.
C. Your firewall is blocking the platform auto-update process
Your firewall may be set to block the network communication between the TWS updater process and the TWS repository server.
If this occurs, you may modify your firewall configuration for allowing outgoing network connections towards the following hosts on port TCP 443:
download2.interactivebrokers.com
download.interactivebrokers.com
For more details on the Hosts and Ports used by the TWS please refer to the section "DESKTOP TWS " of IBKB 2816.
D. You have not launched the TWS for an extended period of time
In this case, the auto-update process may be unable to bridge the gap between the TWS generation that you are running and the current one. If this occurs, please download and run the current TWS installer for the same TWS channel you are using:
- If you use TWS Stable -> Download and run the TWS installer
- If you use TWS Latest -> Download and run the TWS Latest installer
Once you have performed the installation, double-click on the shortcut "Trader Workstation" already on your Desktop to launch the platform.
Possible Alerts during the TWS installation or update
IBKR's Trader Workstation (TWS) is a global trading system enabling clients to use a suite of online trading tools. The TWS can be installed on Windows, Mac OS X and Linux, and it requires the presence of a Java Runtime Environment (JRE). Therefore, when you install the TWS, it also downloads the necessary Java files in order to run using a Java Virtual Machine (JVM).
Sometimes, during the installation or update process of the TWS, software such as Antivirus applications will show an alert and prevent the process to complete. The warning and other messages in this case can safely be ignored, and you can complete the installation of the trading platform.
Table of content
Downloading the TWS installer and update patches
The TWS installers available in the download areas of ibkr.com or IBKR regional web sites are sealed and digitally signed using all the safety procedures required by the industry standards and do not contain any malicious code or process. The same industry standard practices have been used for the TWS update patches, which are automatically downloaded and installed when launching the TWS (if and only if there is an update available). Nevertheless, if you have received an alert, we recommend you to be cautious. Should you intend to keep the TWS installation file on your machine for future use, you should make sure that the same precautions for the protection of data from viruses and malware are applied to it.
Why do I receive a warning when I install the TWS or when the TWS automatic update runs?
You might see an alert (similar to Figure 1 but not limited to) and your security system would wait for your input on how to process the suspicious file. You usually have the option to quarantine the file, delete it, ignore it once or create a permanent exception for it.
Please note that your antivirus might autonomously quarantine or delete the TWS installer file or some of his components without asking for your confirmation and without showing you any warning. Nevertheless, this should only happen if you have preset your antivirus to specifically react in this way.
Figure 1.

What should I do when I receive a warning?
In case you receive a warning during the TWS installation or update, we recommend the following steps:
1. Delete the TWS installer and download it again from the IBKR main or regional web site
a) Delete the TWS installer file already present on your computer and then delete it as well from your Trash (empty your Trash)
b) From the table below, click on the TWS download area correspondent to your location
| Location | TWS download area |
| US | https://www.ibkr.com |
| Asia / Oceania | https://www.interactivebrokers.com.hk |
| India | https://www.interactivebrokers.co.in |
| Europe | https://www.interactivebrokers.co.uk https://www.interactivebrokers.eu |
c) Check the website certificate. Most Internet browsers will immediately alert you in case the site certificate is invalid, compromised or expired. Nevertheless, if you want to check manually the validity of the site certificate, click on the padlock close to the address (URL) and make sure the Connection is reported as secure and no security warning are present (see Figure 2 below).
Figure 2.

d) Click on the button labeled with the TWS version you wish to use and download again the TWS installer
2. Check the digital signature of the TWS installer file you have downloaded
Normally you will immediately receive a security warning in case the digital signature of a file is compromised. Nevertheless, if you wish to perform a manual check, proceed as follows, according to your Operating System:
For Windows
a) From the Windows file explorer, access your Downloads folder or the folder where you placed the TWS installer
b) Right click on the TWS installer file, select Properties and then click on the tab "Digital Signatures"
c) Click on "Details" and on "View Certificate" to check the certificate status and signer. The legitimate signer is "IB Exchange Corp." (See Figure 3 below)
Figure 3.

For Mac OS X
a) Click on the magnifier glass (Spotlight Search) on the top right of your screen and type Terminal. From the search results, launch the Terminal app
b) Type cd Downloads and press Enter
c) Type codesign -dv --verbose=4 tws-latest-macosx-x64.dmg and press Enter. Please notice that the name of the file (tws-latest-macosx-x64.dmg) may differ according to the TWS version you decided to download. If needed, replace the file name in the command with the appropriate one
d) Check the command output and make sure the "Developer ID Application" is "IB Exchange Corp." (see Figure 4 below)
Figure 4.

3. Run the TWS installer file you have downloaded
Once you have downloaded again the TWS installer and after you made sure the file is original (points 1. and 2. above), you can proceed with the installation. Should you still receive a warning from your antivirus, you can reasonably consider it as a false positive and ignore it. Should you need guidance on this step, please proceed directly to the next section.
How can I signal an Alert as false positive?
All modern security systems allow the creation of exceptions, precisely in order to address false positive cases. An exception is a rule forcing the antivirus engine not to scan a specific file or process. That specific file or process will hence be deemed safe and no further alerts will be raised for it.
The procedure for creating an exception may vary, according to the security software you are using. You may be able to create a temporary or permanent exception directly from the alert pop-up or you may have to create one manually from a specific section in the main configuration panel.
If you are unsure of the procedure, we recommend you to consult your antivirus documentation.
Once you have set an exception for the TWS installer file or for the TWS updater process, those will be no longer blocked and will be able to complete their respective tasks successfully.
What else can I do if I have doubts or if my system behaves abnormally?
If you have reasons to believe your machine may be compromised or infected, we recommend performing a full system scan. Usually you can right click on the antivirus icon present on the bottom taskbar (for Windows) or on the upper menu bar (for MacOS) and you will find the option to launch a full system scan. Alternatively, you may start that task from the main antivirus window. If you are unsure of the procedure, we recommend you to consult your antivirus documentation.
Technical Background
How does my security system scan the files I download from the Internet?
Modern antivirus and anti-malware engines base their threats recognition on:
Signature-based scanning: the antivirus scanner searches for a specific pattern of bytes that was previously catalogued as malicious or at least suspicious. The antivirus may check as well file signatures (called hash) against a database of known threats (called virus definitions).
Analysis of behavior: the antivirus engine detects specific actions which individually may not represent a threat but, when correlated together, resemble the usual activity of a malicious software (e.g. the ability of a code to replicate or hide itself, download additional files from the Internet, contact external hosts over the Internet, modify the Operating System registry) This type of scan is designed to detect previously unknown computer threats.
Heuristic detection: the scanner de-compiles the code or runs it within a virtual, restricted environment. It then classifies and weights the actions performed by the code against a predefined, behavior based, rule set.
Cloud-based protection and machine learning: those are relatively new techniques. The file that needs to be analyzed is sent to the antivirus / security system vendor cloud where sophisticated algorithms perform a deep analysis of the code authenticity and behavior.
Are those scan methods infallible?
Modern threats are very sophisticated and, like biological viruses, can mutate their code and their signatures. Moreover, new malwares and exploits are created every day and spread rapidly over the Internet. The threat recognition methods mentioned above are therefore not infallible but can guarantee a high percentage of malware recognition when combined together.
While signature based techniques are very successful in recognizing known threats and less prone to false positives, they are not so efficient in recognizing unknown malware or mutations of existing ones. In this area, the behavioral and heuristic methods perform much better although they are more prone to false positives since their detection is not based on bare code matching but on a certain degree of interpretation and hence uncertainty.
The term "false positive" is used when a security system classifies an innocuous file or process as malware.
Reference:
How to download and install the IBKR Mobile app from alternative app stores
As a consequence of the US Government Huawei ban, the owners of Huawei smartphones will be no longer able to access the Google Play Store and download app from there. If you are affected by this constraint, you will still be able to download and install the IBKR Mobile app from an alternative app store.
Please proceed as follows:
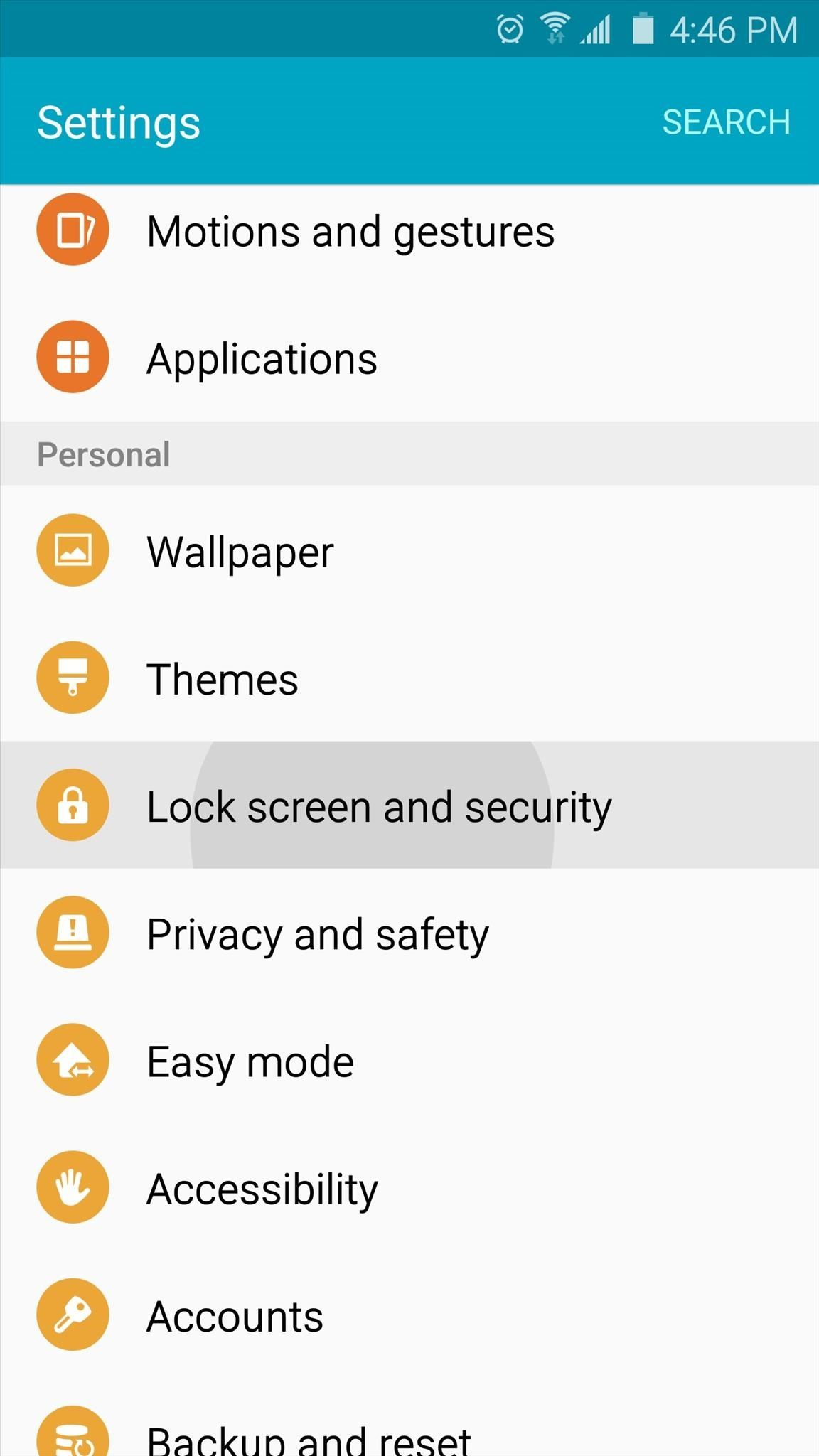
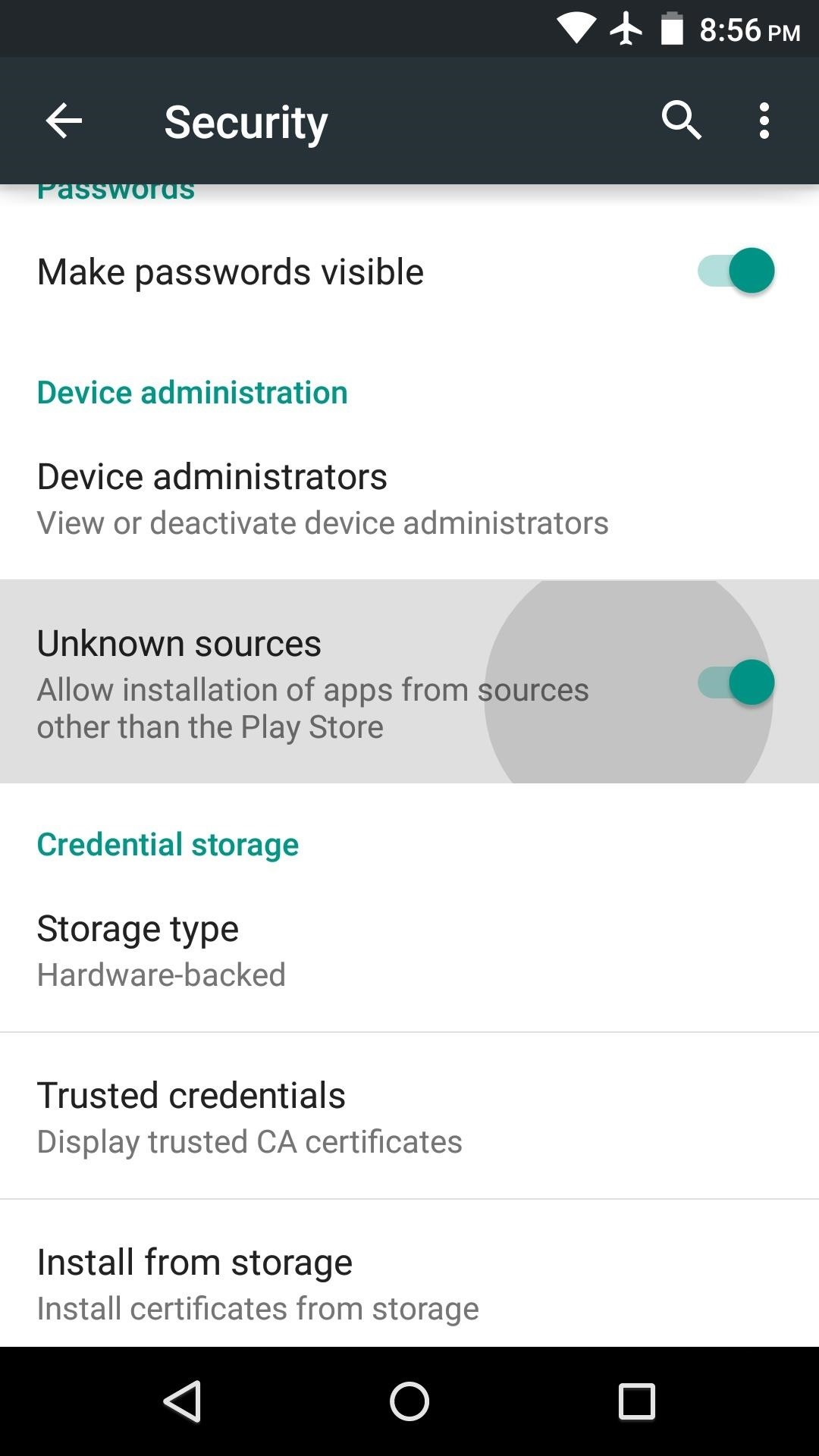
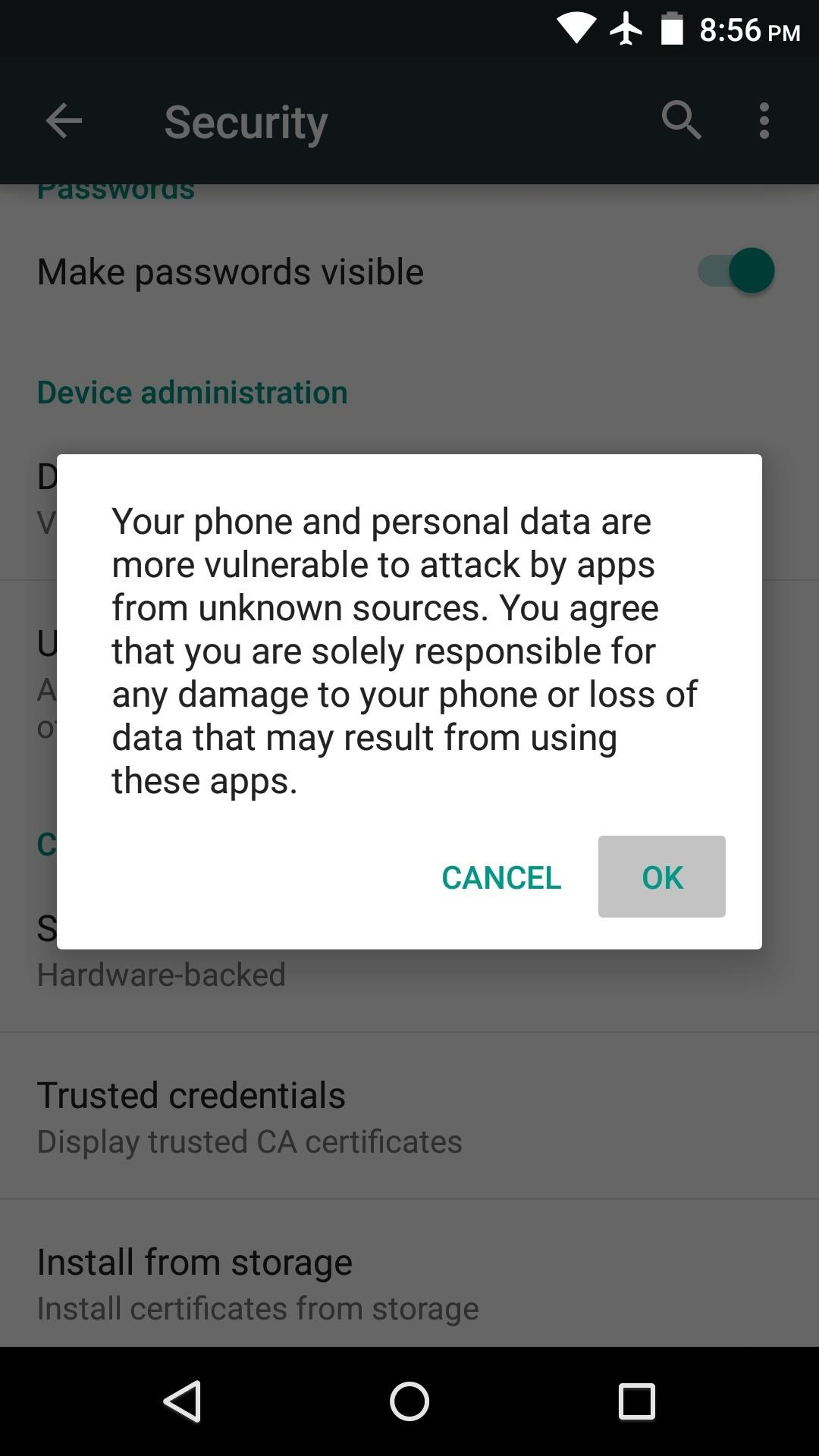
A) Allow your phone to install software from alternative app stores in this way:

2) Under the section System you will find the item Security (it can be called Lock Screen and Security). Click on it
B) You can now download the IBKR Mobile by clicking on one of the links below, according to the alternative store you want to use:
360.cn
.png)
Baidu
How to fix the "Cannot create ... file" error during TWS installation on MacOS
The filesystem permissions are controlled by your machines operating system. One of their functions is to secure your files, preventing unauthorized access or undesired modifications to the system and to your personal data.
Some software on your computer may modify or override the permissions assigned by the operating system. Under certain circumstances, this prevents the TWS installer from accessing the folder where the application core files have to be created (/users/youruser/home/Applications). In such cases, the TWS installation usually displays the error "Cannot create ... file. Shall I try again?"
Procedure:

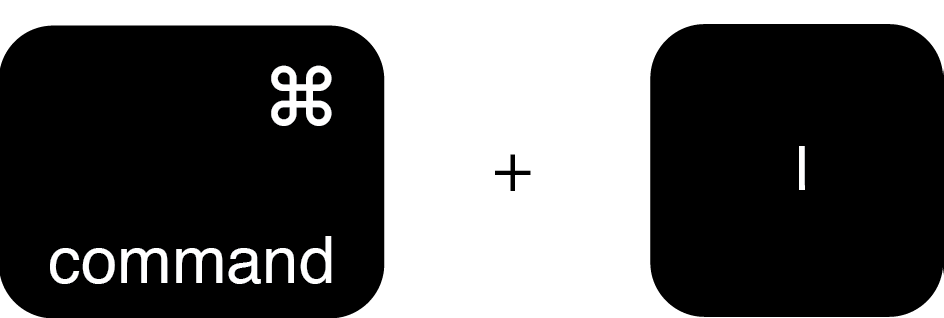
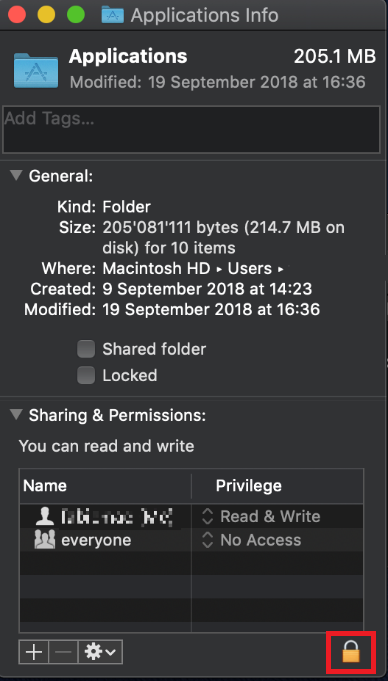
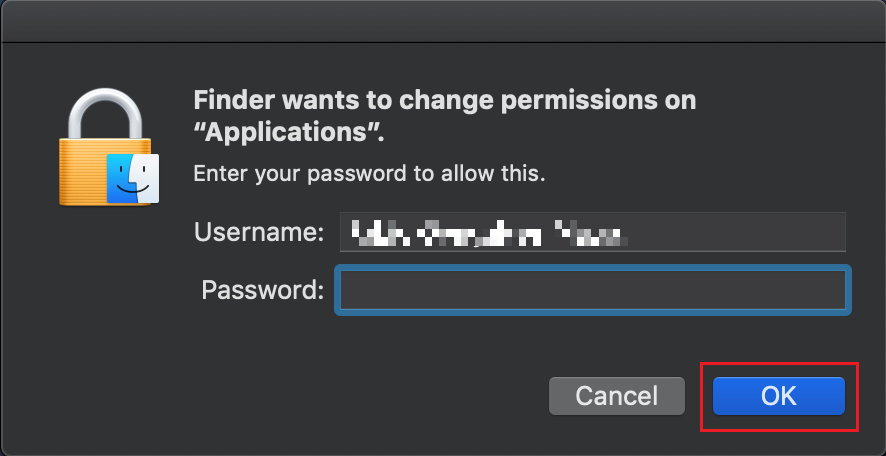
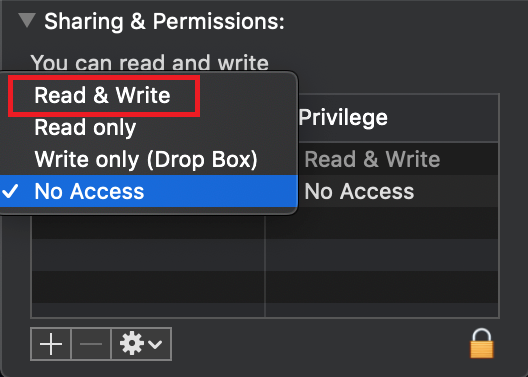
.png)
.png)
.png)
7. Once the installation has completed successfully, repeat the previous steps from 1. to 5. setting back the permissions of “everyone” to “Read Only” to revert your changes to the initial status
How to check and solve connectivity issues affecting the Trader Workstation (TWS)
The Trader Workstation (TWS) software needs to connect to our gateways and market data servers in order to work properly. Connectivity issues affecting your local network or your Internet Service Provider network may negatively affect the TWS functionality. In this article we will indicate how to test your connectivity using an automated connectivity test web page.
How to test the connectivity using the automated "IB Connectivity Test" web page?
2) Please wait until all the tests have been completed and results have been displayed. If you see "Success" as outcome for all tests, your connectivity to IB Servers is reliable at the present moment. No additional connectivity troubleshooting or configuration should be needed.
3) If you see "Fail" as outcome for one or more test/s, please click on the link "Fail" itself in order to display the "IB Network Troubleshooting Guide". That section will help you conduct some manual tests to identify the cause of the failure.
Note for Corporative environments and Proxy server users: the automated "Connectivity Test" page may return misleading results in case your machine is accessing the Internet through a Proxy server. This usually happens if you are connected to a company network. If this is your case, we kindly ask you to contact your Network Administrator or your IT Team and ask them to perform a manual connectivity tests towards the destination servers indicated in the table on the top of the IB automated "Connectivity Test" web page itself. The manual connectivity test should be conducted using destination TCP ports 4000 and 4001. Should they prefer to have the server list in another format or should they need to set up the firewall / IP Management rules, you can forward them this page.
IBKR Mobile Companion App for Apple Watch
Interactive Brokers takes our intuitive and ergonomic mobile trading platform to the next level by providing you a companion app for the Apple Watch.
The companion app is designed to display information when a user has logged in to the IBKR Mobile app on their iPhone. It will work in both the Live Trading and Read Only Modes but does not support active trading. This companion app is only available for informational purpose only.
Table of contents
What does the app do?
At 'glance view' the app will display the following information; Amount of FYI Notification, Account Number, Daily P&L, Net Liquidation Value, Number of Open Orders, Number of Trades Executed, Excess Liquidity and number of Positions you currently own. It will also display the time when it has fetched the information from your iPhone.
Example:
.jpg)
Requirements
- Must have iPhone 5s or greater, using iOS 11 or later.
- Must have the IBKR Mobile app installed on your iPhone (version 11 or greater)
- Must have your Apple Watch paired to your iPhone (refer to: Set up your Apple Watch for directions)
- Must have watchOS 5 running on your Apple Watch.
Important: The Apple Watch applications are only 'companion' apps. This means they are not installed directly on the watch itself, but rather are a function of an application already installed on your iPhone.
How is the app installed?
1. Install the latest version of the IBKR Mobile app on your iPhone.
2. Pair your Apple Watch to your phone.
3. Launch the Watch app on your phone.
4. Scroll down on the main screen until you see your list of apps, locate the IBKR Mobile app and Tap on it.
.jpg)
5. Enable Show App on Apple Watch by swiping the slider to the right (green).
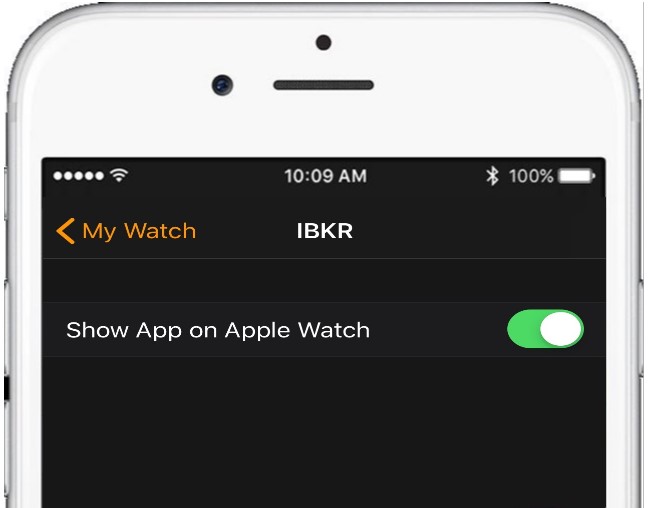
6. After the top slider is set to green, you will see a text informing you that the app is being installed. At this stage the phone is sending the application to your watch per Bluetooth. This might take a short moment (approximately 30-60 seconds.) Once completed the companion app has been installed.
Note: Once enabled it will take 24 hours before P&L shows up on the watch after activation.
.jpg)
How do I confirm the app is installed?
On your Apple Watch click on the crown to access your Home Screen, you should now see an icon for the IBKR Mobile App.

How to start multiple TWS sessions on a Mac
By default macOS does not allow the user to run multiple sessions of the same application. The following workaround can overcome this limitation in case you need to run the Trader Workstation for more than one user.
-
In case running different versions of the TWS is suitable to your needs, please follow the instructions on Procedure 1
-
In case you need multiple sessions of the same TWS version, please follow the instructions on Procedure 2
Procedure 1
1) Open the web page ibkr.com
2) Navigate to the menu Technology > TWS Software.
3) First download and install one of the auto-updating TWS versions (TWS LATEST or TWS according to your preference).
4) Once you have completed the installation, download and install one of the offline versions (OFFLINE TWS LATEST or OFFLINE TWS according to your preference).
5) You will then see on your Desktop two different Trader Workstation icons. You can use the first shortcut to start the first TWS session and the second one to start the additional one (see Figure 1.). Note: the link containing the version number in the name is the OFFLINE version. This will be a version that needs periodical manual updates.
Figure 1.
Procedure 2
1) Launch the first session of the Trader Workstation using the TWS icon present on your Desktop. If you still do not have any Trader Workstation icon, please go to the web page ibkr.com and click on the menu Technology > TWS Software. Then download and install one of the TWS versions displayed.
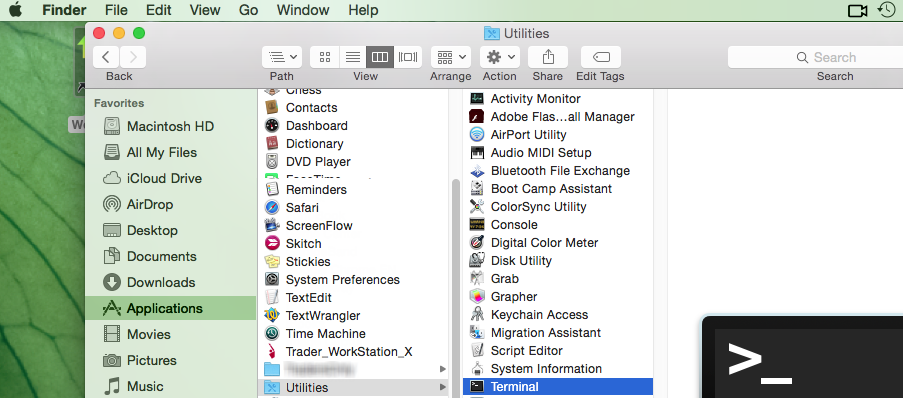
2) Open the Finder and click on Applications on the left side menu. Then select Utilities and then launch Terminal (see Figure 2.).
Figure 2.
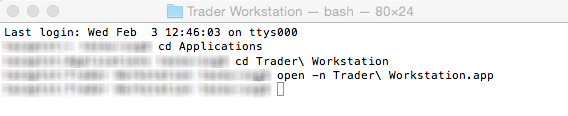
3) The Terminal will appear on the screen and will point to the home folder of your current macOS user. Then enter the commands listed below (see Figure 3.) on your Terminal. After each one, press ENTER on your keyboard.
cd Applications
cd Trader\ Workstation
open -n Trader\ Workstation.app
Figure 3.
4) The login window for your second TWS session will then appear on your Desktop. You can now close the Terminal.
Note: the procedure above presumes that the TWS executable is located in the following path: users/yourusername/home/Applications/Trader Workstation/Trader Workstation.app
If at the time you installed the TWS, you selected to install it for all the users of your system, then the TWS executable will be located here:
/Applications/Trader Workstation/Trader Workstation.app
and therefore you would need to issue the following commands in the Terminal:
cd /Applications
open -n Trader\ Workstation.app
How to overcome the warning message "The signature of the file is corrupt or invalid"
This article describes how to overcome the warning message which you might receive when you download the Trader Workstation or IB Gateway installation packages.
Since a Microsoft update has modified the signature validation mechanisms, the Trader Workstation and IB Gateway installation packages might be reported as having an invalid or corrupt signature, although their signature is indeed intact and absolutely valid.
If you are using Microsoft Edge as browser please follow all the steps below. If you are using any other browser start directly from point 3.
1. As soon as the installation package has been completely downloaded, you will notice on the bar at the bottom of your browser frame the warning message "The signature of the file tws-... is corrupt or invalid". Please click on the button View Downloads to open the DOWNLOADS panel. ![]()
2. Right click on the filename and select Run anyway.
.png)
3. Once the installer has been launched, the SmartScreen filter will display an additional warning message. Click on the link More Info.
(1).png)
4. Now click the button Run Anyway to allow the file execution. The installation will then start.