Possible Alerts during the TWS installation or update
IBKR's Trader Workstation (TWS) is a global trading system enabling clients to use a suite of online trading tools. The TWS can be installed on Windows, Mac OS X and Linux, and it requires the presence of a Java Runtime Environment (JRE). Therefore, when you install the TWS, it also downloads the necessary Java files in order to run using a Java Virtual Machine (JVM).
Sometimes, during the installation or update process of the TWS, software such as Antivirus applications will show an alert and prevent the process to complete. The warning and other messages in this case can safely be ignored, and you can complete the installation of the trading platform.
Table of content
Downloading the TWS installer and update patches
The TWS installers available in the download areas of ibkr.com or IBKR regional web sites are sealed and digitally signed using all the safety procedures required by the industry standards and do not contain any malicious code or process. The same industry standard practices have been used for the TWS update patches, which are automatically downloaded and installed when launching the TWS (if and only if there is an update available). Nevertheless, if you have received an alert, we recommend you to be cautious. Should you intend to keep the TWS installation file on your machine for future use, you should make sure that the same precautions for the protection of data from viruses and malware are applied to it.
Why do I receive a warning when I install the TWS or when the TWS automatic update runs?
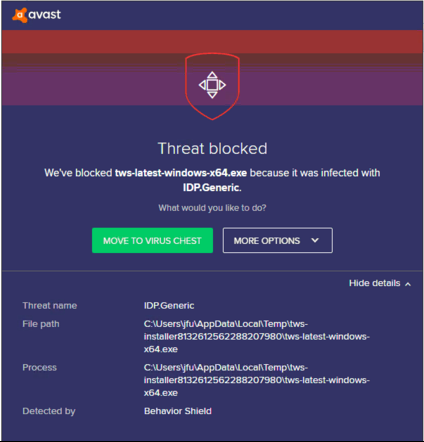
You might see an alert (similar to Figure 1 but not limited to) and your security system would wait for your input on how to process the suspicious file. You usually have the option to quarantine the file, delete it, ignore it once or create a permanent exception for it.
Please note that your antivirus might autonomously quarantine or delete the TWS installer file or some of his components without asking for your confirmation and without showing you any warning. Nevertheless, this should only happen if you have preset your antivirus to specifically react in this way.
Figure 1.
What should I do when I receive a warning?
In case you receive a warning during the TWS installation or update, we recommend the following steps:
1. Delete the TWS installer and download it again from the IBKR main or regional web site
a) Delete the TWS installer file already present on your computer and then delete it as well from your Trash (empty your Trash)
b) From the table below, click on the TWS download area correspondent to your location
| Location | TWS download area |
| US | https://www.ibkr.com |
| Asia / Oceania | https://www.interactivebrokers.com.hk |
| India | https://www.interactivebrokers.co.in |
| Europe | https://www.interactivebrokers.co.uk https://www.interactivebrokers.eu |
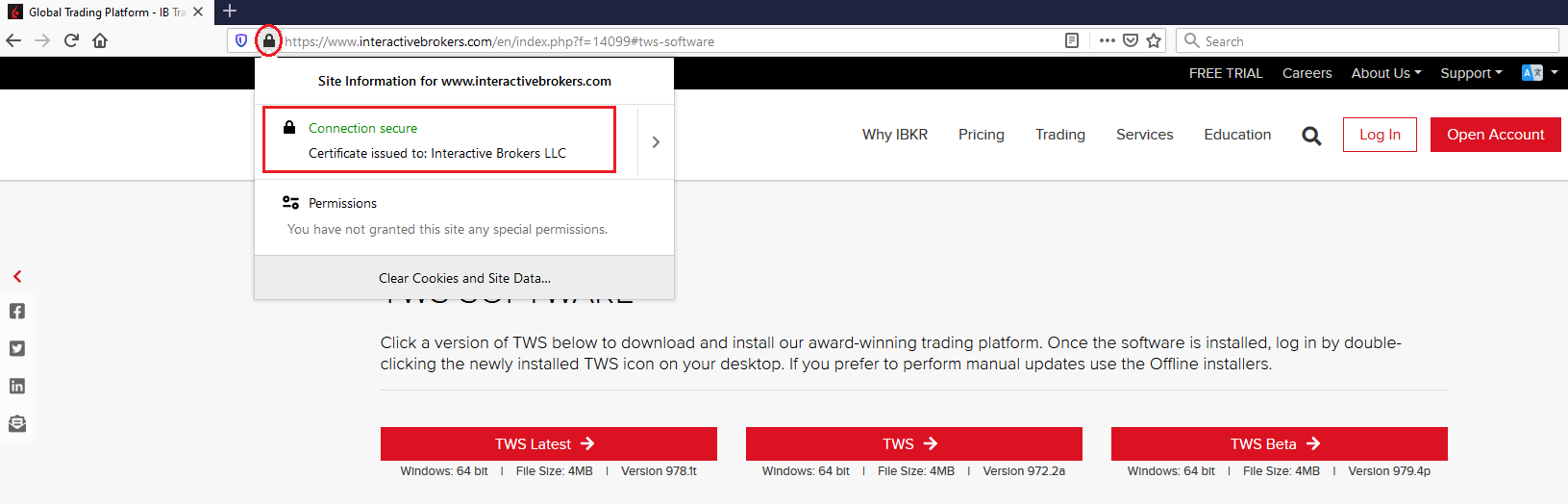
c) Check the website certificate. Most Internet browsers will immediately alert you in case the site certificate is invalid, compromised or expired. Nevertheless, if you want to check manually the validity of the site certificate, click on the padlock close to the address (URL) and make sure the Connection is reported as secure and no security warning are present (see Figure 2 below).
Figure 2.
d) Click on the button labeled with the TWS version you wish to use and download again the TWS installer
2. Check the digital signature of the TWS installer file you have downloaded
Normally you will immediately receive a security warning in case the digital signature of a file is compromised. Nevertheless, if you wish to perform a manual check, proceed as follows, according to your Operating System:
For Windows
a) From the Windows file explorer, access your Downloads folder or the folder where you placed the TWS installer
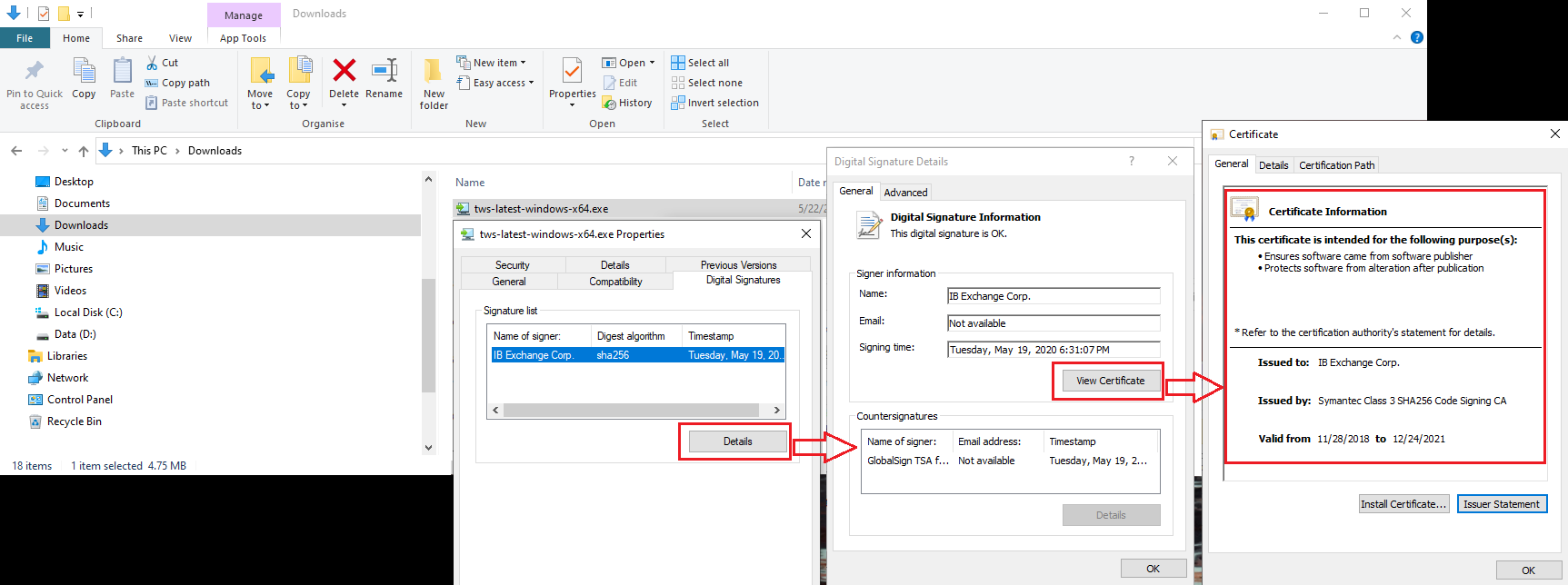
b) Right click on the TWS installer file, select Properties and then click on the tab "Digital Signatures"
c) Click on "Details" and on "View Certificate" to check the certificate status and signer. The legitimate signer is "IB Exchange Corp." (See Figure 3 below)
Figure 3.
For Mac OS X
a) Click on the magnifier glass (Spotlight Search) on the top right of your screen and type Terminal. From the search results, launch the Terminal app
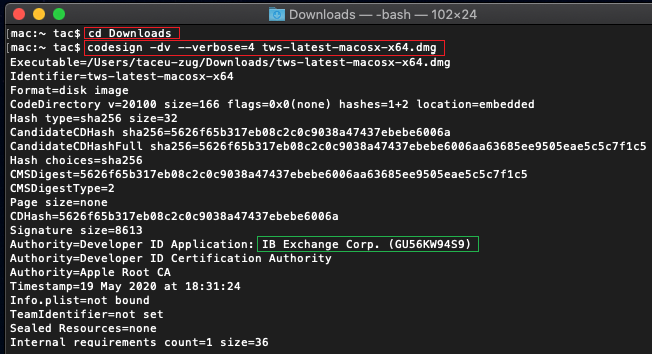
b) Type cd Downloads and press Enter
c) Type codesign -dv --verbose=4 tws-latest-macosx-x64.dmg and press Enter. Please notice that the name of the file (tws-latest-macosx-x64.dmg) may differ according to the TWS version you decided to download. If needed, replace the file name in the command with the appropriate one
d) Check the command output and make sure the "Developer ID Application" is "IB Exchange Corp." (see Figure 4 below)
Figure 4.
3. Run the TWS installer file you have downloaded
Once you have downloaded again the TWS installer and after you made sure the file is original (points 1. and 2. above), you can proceed with the installation. Should you still receive a warning from your antivirus, you can reasonably consider it as a false positive and ignore it. Should you need guidance on this step, please proceed directly to the next section.
How can I signal an Alert as false positive?
All modern security systems allow the creation of exceptions, precisely in order to address false positive cases. An exception is a rule forcing the antivirus engine not to scan a specific file or process. That specific file or process will hence be deemed safe and no further alerts will be raised for it.
The procedure for creating an exception may vary, according to the security software you are using. You may be able to create a temporary or permanent exception directly from the alert pop-up or you may have to create one manually from a specific section in the main configuration panel.
If you are unsure of the procedure, we recommend you to consult your antivirus documentation.
Once you have set an exception for the TWS installer file or for the TWS updater process, those will be no longer blocked and will be able to complete their respective tasks successfully.
What else can I do if I have doubts or if my system behaves abnormally?
If you have reasons to believe your machine may be compromised or infected, we recommend performing a full system scan. Usually you can right click on the antivirus icon present on the bottom taskbar (for Windows) or on the upper menu bar (for MacOS) and you will find the option to launch a full system scan. Alternatively, you may start that task from the main antivirus window. If you are unsure of the procedure, we recommend you to consult your antivirus documentation.
Technical Background
How does my security system scan the files I download from the Internet?
Modern antivirus and anti-malware engines base their threats recognition on:
Signature-based scanning: the antivirus scanner searches for a specific pattern of bytes that was previously catalogued as malicious or at least suspicious. The antivirus may check as well file signatures (called hash) against a database of known threats (called virus definitions).
Analysis of behavior: the antivirus engine detects specific actions which individually may not represent a threat but, when correlated together, resemble the usual activity of a malicious software (e.g. the ability of a code to replicate or hide itself, download additional files from the Internet, contact external hosts over the Internet, modify the Operating System registry) This type of scan is designed to detect previously unknown computer threats.
Heuristic detection: the scanner de-compiles the code or runs it within a virtual, restricted environment. It then classifies and weights the actions performed by the code against a predefined, behavior based, rule set.
Cloud-based protection and machine learning: those are relatively new techniques. The file that needs to be analyzed is sent to the antivirus / security system vendor cloud where sophisticated algorithms perform a deep analysis of the code authenticity and behavior.
Are those scan methods infallible?
Modern threats are very sophisticated and, like biological viruses, can mutate their code and their signatures. Moreover, new malwares and exploits are created every day and spread rapidly over the Internet. The threat recognition methods mentioned above are therefore not infallible but can guarantee a high percentage of malware recognition when combined together.
While signature based techniques are very successful in recognizing known threats and less prone to false positives, they are not so efficient in recognizing unknown malware or mutations of existing ones. In this area, the behavioral and heuristic methods perform much better although they are more prone to false positives since their detection is not based on bare code matching but on a certain degree of interpretation and hence uncertainty.
The term "false positive" is used when a security system classifies an innocuous file or process as malware.
Reference:
