Possíveis alertas durante a instalação ou atualização do TWS
A plataforma Trader Workstation (TWS) da IBKR é um sistema global de negociações que oferece aos clientes um pacote de ferramentas de negociação on-line. O TWS pode ser instalado nos sistemas operacionais Windows, Mac OS X e Linux, e requer a instalação de um Java Runtime Environment (JRE). Portanto, ao instalar o TWS, o programa também faz download dos arquivos Java necessários para execução com o Java Virtual Machine (JVM).
Às vezes, durante o processo de instalação ou atualização do TWS, alguns tipos de software, como aplicativos de antivírus, podem exibir um alerta e impedir a conclusão do processo. Nesses casos, você pode ignorar com segurança os avisos e outras mensagens para concluir a instalação da plataforma de negociações.
Índice
Download do instalador e de patches de atualização do TWS
Os instaladores do TWS disponíveis nas áreas de download do site ibkr.com ou dos sites regionais da IBKR são bloqueados e assinados digitalmente usando todos os procedimentos de segurança exigidos pelos padrões do setor e não contêm códigos ou processos maliciosos. As mesmas práticas padrão do setor são usadas para os patches de atualização do TWS, que são baixados e instalados automaticamente ao iniciar o TWS (somente se houver uma atualização disponível). Mesmo assim, caso você receba um alerta, recomendamos que você tenha cuidado. Caso pretenda manter o arquivo de instalação do TWS na sua máquina para usá-lo futuramente, as mesmas medidas de precaução para proteger os dados contra vírus e malware devem ser aplicadas.
Por que recebo um aviso quando instalo o TWS ou quando a atualização automática do TWS é executada?
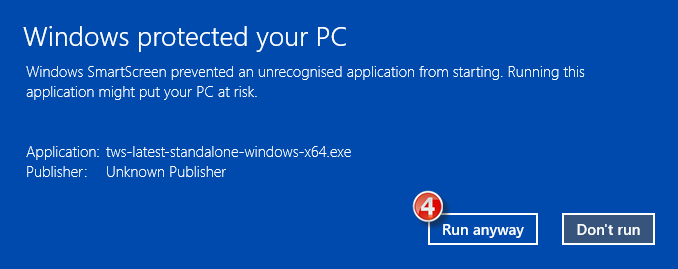
É possível que você veja um alerta (semelhante à Figura 1) e seu sistema de segurança espere você tomar uma decisão sobre como processar o arquivo suspeito. Geralmente, existem as opções de colocar o arquivo em quarentena, exclui-lo, ignorá-lo ou criar uma exceção permanente para ele.
Observe que seu antivírus pode, de maneira autônoma, colocar o arquivo do instalador do TWS em quarentena ou excluir esse arquivo ou algum de seus componentes sem pedir sua confirmação e sem exibir avisos. No entanto, isso acontece somente se você predefinir seu antivírus para reagir especificamente dessa maneira.
Figura 1.
O que devo fazer ao receber um aviso?
Caso receba um aviso durante a instalação ou atualização do TWS, recomendamos as seguintes etapas:
1. Exclua o instalador do TWS e faça download dele novamente no site principal ou regional da IBKR
a) Exclua o arquivo do instalador do TWS já presente no seu computador e exclua-o também da sua Lixeira (esvazie a sua Lixeira).
b) Na tabela a seguir, clique na área de download do TWS correspondente à sua localização.
| Localização | Área de download do TWS |
| EUA | https://www.ibkr.com |
| Ásia/Oceania | https://www.interactivebrokers.com.hk |
| Índia | https://www.interactivebrokers.co.in |
| Europa | https://www.interactivebrokers.co.uk https://www.interactivebrokers.eu |
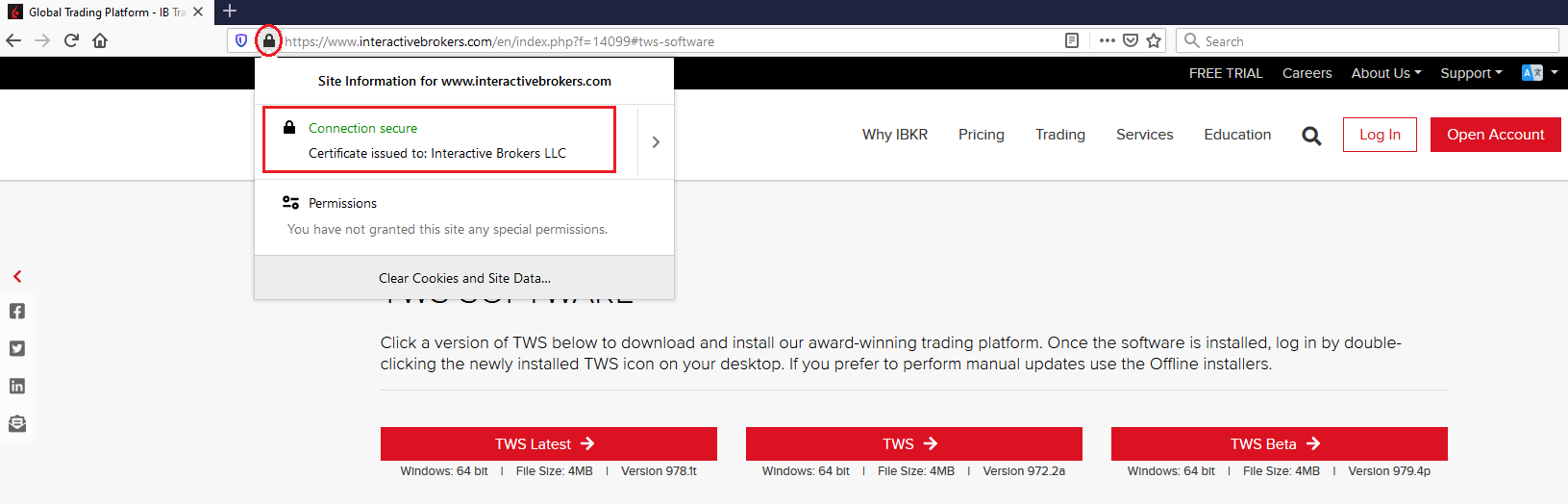
c) Confira o certificado do site. A maioria dos navegadores de Internet enviarão um alerta imediatamente caso o certificado do site seja inválido, esteja comprometido ou vencido. No entanto, se quiser verificar manualmente a validade do certificado do site, clique no cadeado próximo ao endereço (URL) e confira se a Conexão está avaliada como segura e se não há avisos de segurança (veja a Figura 2 a seguir).
Figura 2.
d) Clique no botão com a versão do TWS que você deseja usar e faça download novamente do instalador do TWS.
2. Confira a assinatura digital do arquivo do instalador do TWS que você baixou
Normalmente, você receberá imediatamente um aviso de segurança caso a assinatura digital de um arquivo esteja comprometida. No entanto, caso deseje realizar uma verificação manual, prossiga da seguinte maneira, de acordo com seu sistema operacional:
Para Windows
a) No Windows file explorer, acesse sua pasta de Downloads ou a pasta em que você colocou o instalador do TWS.
b) Clique com o botão direito do mouse no arquivo do instalador do TWS, selecione Propriedades e, em seguida, clique na guia "Assinaturas digitais".
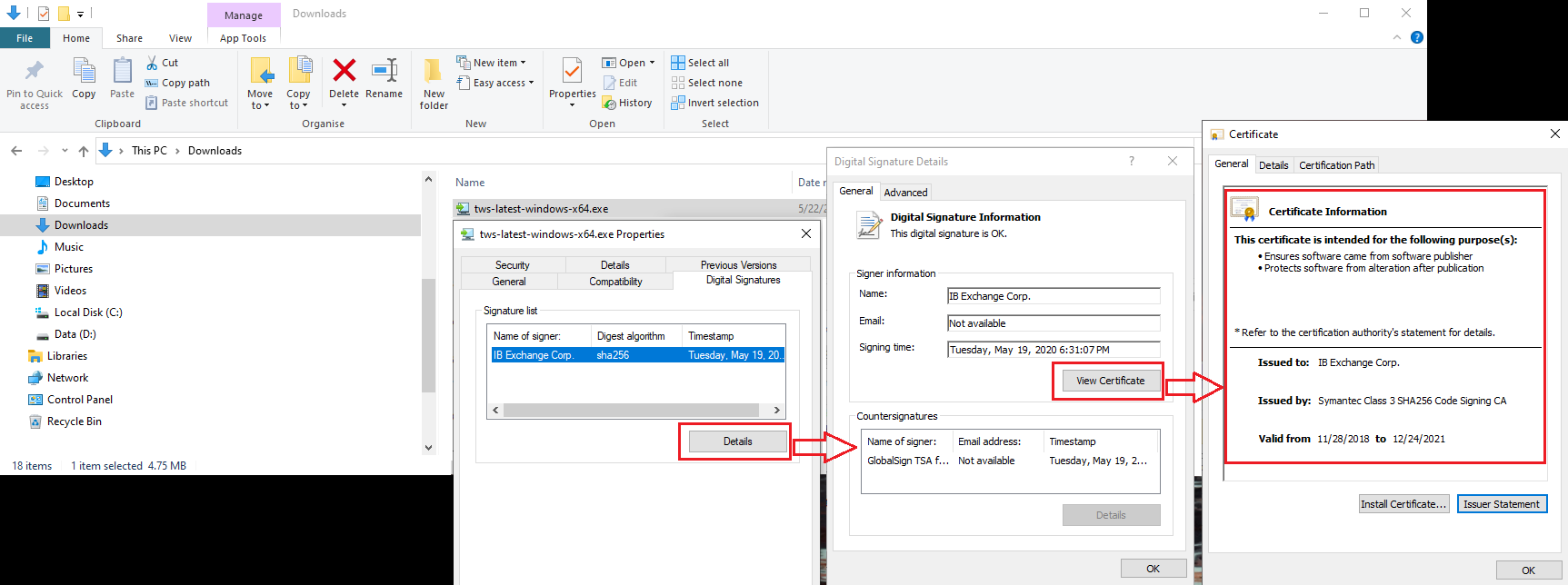
c) Clique em "Detalhes" e em "Exibir Certificado" para verificar o status do certificado e o signatário. O signatário legítimo é "IB Exchange Corp." (Veja a Figura 3 abaixo).
Figura 3.
Para Mac OS X
a) Clique na lupa (Pesquisa Spotlight) no canto superior direito da tela e digite Terminal. A partir dos resultados da pesquisa, inicie o aplicativo Terminal.
b) Digite cd Downloads e pressione Enter.
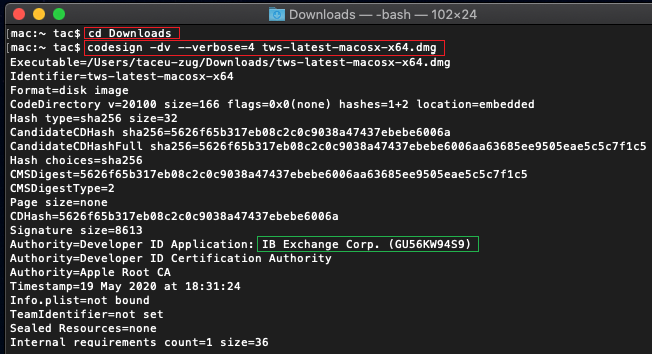
c) Digite codesign -dv --verbose=4 tws-latest-macosx-x64.dmg e pressione Enter. Observe que o nome do arquivo (tws-latest-macosx-x64.dmg) pode ser diferente de acordo com a versão do TWS que você decidiu baixar. Se necessário, substitua o nome do arquivo no comando pelo nome apropriado.
d) Verifique o resultado do comando e confira se o "Developer ID Application" é "IB Exchange Corp." (veja a Figura 4 abaixo).
Figura 4.
3. Execute o arquivo do instalador do TWS que você baixou
Depois de fazer download novamente do instalador do TWS e depois de confirmar que o arquivo é original (pontos 1. e 2. acima), você pode prosseguir com a instalação. Caso você ainda receba um aviso do seu antivírus, considere-o um falso-positivo e ignore-o. Caso precise de ajuda nesta etapa, continue na próxima seção.
Como eu posso identificar um alerta como falso-positivo?
Todos os sistemas de segurança modernos permitem a criação de exceções para tratar de casos de falsos-positivos. Uma exceção é uma regra que força o mecanismo de antivírus a não fazer a varredura de um arquivo ou processo específico. Esse arquivo ou processo específico será considerado seguro e nenhum outro alerta será lançado para ele.
O procedimento para criar uma exceção pode variar de acordo com o tipo de software de segurança que você estiver usando. Talvez seja possível criar uma exceção temporária ou permanente diretamente no pop-up de alerta ou talvez seja necessário criar uma exceção manualmente em uma seção específica no painel de configuração principal.
Caso não tenha certeza sobre o procedimento, recomendamos que você consulte a documentação do seu antivírus.
Depois de configurar uma exceção para o arquivo de instalação do TWS ou para o processo do atualizador do TWS, esses arquivos serão desbloqueados e será possível concluir as respectivas tarefas.
O que mais posso fazer em caso de dúvidas ou se o meu sistema apresentar comportamento anormal?
Caso tenha motivos para acreditar que sua máquina esteja comprometida ou infectada, recomendamos que você realize uma varredura completa do sistema. Geralmente, basta clicar com o botão direito do mouse no ícone do antivírus presente na barra de ferramentas na parte inferior da tela (para Windows) ou na barra do menu superior (para MacOS) e você encontrará a opção para iniciar uma varredura completa do sistema. Também é possível iniciar a tarefa na janela principal do antivírus. Caso não tenha certeza sobre o procedimento, recomendamos que você consulte a documentação do seu antivírus.
Referência técnica
Como meu sistema de segurança faz a varredura dos arquivos que eu baixo da Internet?
Mecanismos modernos de antivírus e antimalware reconhecem as ameaças com base nas seguintes opções:
Varredura com base em assinatura: o sistema de varredura do antivírus busca um padrão específico de bytes catalogado anteriormente como malicioso ou suspeito. O antivírus pode verificar também as assinaturas de arquivos (chamadas hash) em um banco de dados de ameaças conhecidas (chamado definições de vírus).
Análise de comportamento: o mecanismo de antivírus detecta operações específicas que individualmente podem não representar uma ameaça, mas que, quando correlacionadas, assemelham-se à atividade habitual de um software malicioso (por exemplo, a capacidade de um código de se replicar ou de se ocultar, fazer download de arquivos adicionais na Internet, entrar em contato com hosts externos na Internet, modificar o registro do sistema operacional etc.). Esse tipo de varredura foi desenvolvido para detectar ameaças aos computadores anteriormente desconhecidas.
Detecção heurística: o sistema de varredura descompila o código ou executa-o em um ambiente virtual restrito. Em seguida, ele classifica e pondera as operações executadas pelo código diante de um conjunto de regras predefinido com base em comportamento.
Proteção com base em nuvem e aprendizado de máquina: essas são técnicas relativamente novas. O arquivo que precisa ser analisado é enviado para a nuvem do fornecedor do antivírus/sistema de segurança, onde algoritmos sofisticados realizam uma análise aprofundada da autenticidade e do comportamento do código.
Esses métodos são infalíveis?
Ameaças modernas são muito sofisticadas e, como vírus biológicos, podem fazer com que o código e as assinaturas sofram mutações. Além disso, novos tipos de malware e exploits são criados todos os dias e se espalham rapidamente pela Internet. Portanto, os métodos de reconhecimento de ameaças mencionados acima não são infalíveis, mas podem garantir uma alta porcentagem de reconhecimento de malware quando combinados.
Enquanto as técnicas com base em assinatura são excelentes para reconhecer ameaças conhecidas e menos propensas a falsos-positivos, elas não são tão eficientes para identificar malware desconhecido ou mutações de tipos existentes de malware. Nessa área, os métodos comportamentais e heurísticos têm um desempenho muito melhor, ainda que tenham maior propensão a falsos-positivos, pois o processo de detecção desses métodos não tem como base um código vazio correspondente, mas um certo grau de interpretação e, portanto, de incerteza.
O termo "falso-positivo" é usado quando um sistema de segurança classifica como malware um arquivo ou processo inócuo.
Referências:
Please Upgrade TraderWorkstation (TWS)
On December 9, 2021, a critical security vulnerability in Apache's Log4j software library was disclosed, (now commonly referred to as “Log4Shell”). Log4j is very broadly used in a wide variety of consumer and enterprise services, websites, applications, and devices to log security and performance information. The vulnerability allows an unauthenticated remote actor to take control of an affected system and execute arbitrary code on it. The ubiquitous nature of Log4j and the ease of exploitation of the vulnerability makes this threat not only critical but also nearly universal.
WHAT IS IBKR DOING TO PROTECT ITS CLIENTS?
We are actively working, with high priority, to mitigate the threat on several levels:
- We have patched all our servers accessible externally (from the Internet) with a version of Log4j that is not susceptible to this vulnerability.
- We have upgraded our Trader Workstation (TWS) software and our TWS installers with a version of Log4j that is not susceptible to this vulnerability.
- We have updated our security infrastructure (including network firewalls, application firewalls, intrusion detection tools, etc.) with the latest protection measures that help detect and block cyber-attacks that attempt to exploit the Log4j vulnerability.
- We continue our ongoing efforts to fully identify and patch any impacted internal systems (those that are not accessible from the Internet).
- We continue monitoring the evolving industry threats and adopt additional mitigation measures as needed.
ACTION REQUIRED
We are committed to providing a secure environment for your assets and trading activities. To that end, we request that our clients give priority to the use of the LATEST TWS version, which will auto-update. Should you have the STABLE or any OFFLINE version, which does not auto-update, please ensure that you take the necessary steps to keep your TWS in line with the latest security fixes.
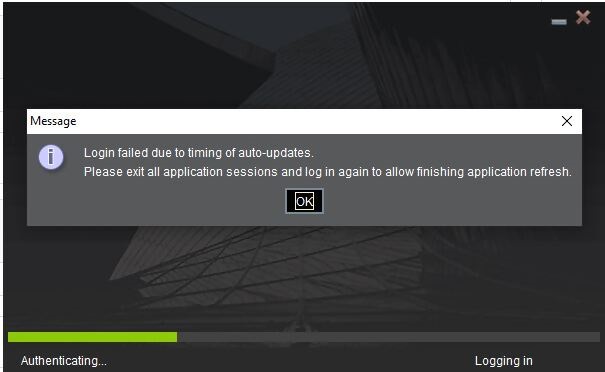
How to solve "Login failed due to timing of auto-updates."
When you use certain versions of the Trader Workstation (TWS), you may receive the error message "Login failed due to timing of auto-updates." When this occurs, the platform will not start up and will not display the login window.
In this article we will outline the possible causes of this error along with the resolution steps.
We provide two TWS installation types: the TWS and the Offline TWS
-
The TWS automatically updates itself each time a new platform release is available.
-
The Offline TWS does not update itself automatically. Should you want to update the offline TWS, you would have to download and run the newly released Offline TWS installer from our website.
What can cause this error?
A. Another TWS session is running on your computer
B. A program is blocking the platform auto-update process
C. Your firewall is blocking the platform auto-update process
D. You have not launched the TWS for an extended period of time
A. Another TWS session is running on your computer
If another TWS session is running on your computer (either visibly or in the background), the updater process will not be able to update the application core files since they are in use. In this case, please follow the steps below:
If you are able to locate the TWS window on your Desktop or on the tray bar, bring it to the foreground and use the TWS top menu File -> Exit to close it. Then launch the TWS again and wait for the automatic update to complete. You should then see the TWS login window where you can enter your credentials.
If you are unable to locate the TWS window, please consider that the TWS process may still be running. This usually happens when the TWS was not properly closed or unresponsive. In this case you can use the task manager to terminate the process. According to your operating system, please follow the steps below:
Windows
1. Press CTRL+ALT+DEL on your keyboard and select Task Manager
2. Under the tab "Processes", please check if there is a process named TWS.exe or update.exe running. If you find any, click on it to highlight it and click on the button "End task" or "Force Quit" on the bottom right corner of the Task Manager window
3. If for some reason, you are unable to terminate the process through the Task Manager, restart your computer
Mac
1. Press CMD+OPT+ESC on your keyboard
2. Select the "Trader Workstation" process and click on "Force Quit"
3. If for some reason, you are unable to terminate the process, restart your computer
B. A program is blocking the platform auto-update process
A program on your computer, such as an antivirus, may erroneously interpret the behavior of the TWS updater process as suspicious or threatening and prevent it from running or from connecting to the TWS repository server. If this occurs please refer to IBKB 3424 for further recommendations and steps.
C. Your firewall is blocking the platform auto-update process
Your firewall may be set to block the network communication between the TWS updater process and the TWS repository server.
If this occurs, you may modify your firewall configuration for allowing outgoing network connections towards the following hosts on port TCP 443:
download2.interactivebrokers.com
download.interactivebrokers.com
For more details on the Hosts and Ports used by the TWS please refer to the section "DESKTOP TWS " of IBKB 2816.
D. You have not launched the TWS for an extended period of time
In this case, the auto-update process may be unable to bridge the gap between the TWS generation that you are running and the current one. If this occurs, please download and run the current TWS installer for the same TWS channel you are using:
- If you use TWS Stable -> Download and run the TWS installer
- If you use TWS Latest -> Download and run the TWS Latest installer
Once you have performed the installation, double-click on the shortcut "Trader Workstation" already on your Desktop to launch the platform.
Possible Alerts during the TWS installation or update
IBKR's Trader Workstation (TWS) is a global trading system enabling clients to use a suite of online trading tools. The TWS can be installed on Windows, Mac OS X and Linux, and it requires the presence of a Java Runtime Environment (JRE). Therefore, when you install the TWS, it also downloads the necessary Java files in order to run using a Java Virtual Machine (JVM).
Sometimes, during the installation or update process of the TWS, software such as Antivirus applications will show an alert and prevent the process to complete. The warning and other messages in this case can safely be ignored, and you can complete the installation of the trading platform.
Table of content
Downloading the TWS installer and update patches
The TWS installers available in the download areas of ibkr.com or IBKR regional web sites are sealed and digitally signed using all the safety procedures required by the industry standards and do not contain any malicious code or process. The same industry standard practices have been used for the TWS update patches, which are automatically downloaded and installed when launching the TWS (if and only if there is an update available). Nevertheless, if you have received an alert, we recommend you to be cautious. Should you intend to keep the TWS installation file on your machine for future use, you should make sure that the same precautions for the protection of data from viruses and malware are applied to it.
Why do I receive a warning when I install the TWS or when the TWS automatic update runs?
You might see an alert (similar to Figure 1 but not limited to) and your security system would wait for your input on how to process the suspicious file. You usually have the option to quarantine the file, delete it, ignore it once or create a permanent exception for it.
Please note that your antivirus might autonomously quarantine or delete the TWS installer file or some of his components without asking for your confirmation and without showing you any warning. Nevertheless, this should only happen if you have preset your antivirus to specifically react in this way.
Figure 1.

What should I do when I receive a warning?
In case you receive a warning during the TWS installation or update, we recommend the following steps:
1. Delete the TWS installer and download it again from the IBKR main or regional web site
a) Delete the TWS installer file already present on your computer and then delete it as well from your Trash (empty your Trash)
b) From the table below, click on the TWS download area correspondent to your location
| Location | TWS download area |
| US | https://www.ibkr.com |
| Asia / Oceania | https://www.interactivebrokers.com.hk |
| India | https://www.interactivebrokers.co.in |
| Europe | https://www.interactivebrokers.co.uk https://www.interactivebrokers.eu |
c) Check the website certificate. Most Internet browsers will immediately alert you in case the site certificate is invalid, compromised or expired. Nevertheless, if you want to check manually the validity of the site certificate, click on the padlock close to the address (URL) and make sure the Connection is reported as secure and no security warning are present (see Figure 2 below).
Figure 2.

d) Click on the button labeled with the TWS version you wish to use and download again the TWS installer
2. Check the digital signature of the TWS installer file you have downloaded
Normally you will immediately receive a security warning in case the digital signature of a file is compromised. Nevertheless, if you wish to perform a manual check, proceed as follows, according to your Operating System:
For Windows
a) From the Windows file explorer, access your Downloads folder or the folder where you placed the TWS installer
b) Right click on the TWS installer file, select Properties and then click on the tab "Digital Signatures"
c) Click on "Details" and on "View Certificate" to check the certificate status and signer. The legitimate signer is "IB Exchange Corp." (See Figure 3 below)
Figure 3.

For Mac OS X
a) Click on the magnifier glass (Spotlight Search) on the top right of your screen and type Terminal. From the search results, launch the Terminal app
b) Type cd Downloads and press Enter
c) Type codesign -dv --verbose=4 tws-latest-macosx-x64.dmg and press Enter. Please notice that the name of the file (tws-latest-macosx-x64.dmg) may differ according to the TWS version you decided to download. If needed, replace the file name in the command with the appropriate one
d) Check the command output and make sure the "Developer ID Application" is "IB Exchange Corp." (see Figure 4 below)
Figure 4.

3. Run the TWS installer file you have downloaded
Once you have downloaded again the TWS installer and after you made sure the file is original (points 1. and 2. above), you can proceed with the installation. Should you still receive a warning from your antivirus, you can reasonably consider it as a false positive and ignore it. Should you need guidance on this step, please proceed directly to the next section.
How can I signal an Alert as false positive?
All modern security systems allow the creation of exceptions, precisely in order to address false positive cases. An exception is a rule forcing the antivirus engine not to scan a specific file or process. That specific file or process will hence be deemed safe and no further alerts will be raised for it.
The procedure for creating an exception may vary, according to the security software you are using. You may be able to create a temporary or permanent exception directly from the alert pop-up or you may have to create one manually from a specific section in the main configuration panel.
If you are unsure of the procedure, we recommend you to consult your antivirus documentation.
Once you have set an exception for the TWS installer file or for the TWS updater process, those will be no longer blocked and will be able to complete their respective tasks successfully.
What else can I do if I have doubts or if my system behaves abnormally?
If you have reasons to believe your machine may be compromised or infected, we recommend performing a full system scan. Usually you can right click on the antivirus icon present on the bottom taskbar (for Windows) or on the upper menu bar (for MacOS) and you will find the option to launch a full system scan. Alternatively, you may start that task from the main antivirus window. If you are unsure of the procedure, we recommend you to consult your antivirus documentation.
Technical Background
How does my security system scan the files I download from the Internet?
Modern antivirus and anti-malware engines base their threats recognition on:
Signature-based scanning: the antivirus scanner searches for a specific pattern of bytes that was previously catalogued as malicious or at least suspicious. The antivirus may check as well file signatures (called hash) against a database of known threats (called virus definitions).
Analysis of behavior: the antivirus engine detects specific actions which individually may not represent a threat but, when correlated together, resemble the usual activity of a malicious software (e.g. the ability of a code to replicate or hide itself, download additional files from the Internet, contact external hosts over the Internet, modify the Operating System registry) This type of scan is designed to detect previously unknown computer threats.
Heuristic detection: the scanner de-compiles the code or runs it within a virtual, restricted environment. It then classifies and weights the actions performed by the code against a predefined, behavior based, rule set.
Cloud-based protection and machine learning: those are relatively new techniques. The file that needs to be analyzed is sent to the antivirus / security system vendor cloud where sophisticated algorithms perform a deep analysis of the code authenticity and behavior.
Are those scan methods infallible?
Modern threats are very sophisticated and, like biological viruses, can mutate their code and their signatures. Moreover, new malwares and exploits are created every day and spread rapidly over the Internet. The threat recognition methods mentioned above are therefore not infallible but can guarantee a high percentage of malware recognition when combined together.
While signature based techniques are very successful in recognizing known threats and less prone to false positives, they are not so efficient in recognizing unknown malware or mutations of existing ones. In this area, the behavioral and heuristic methods perform much better although they are more prone to false positives since their detection is not based on bare code matching but on a certain degree of interpretation and hence uncertainty.
The term "false positive" is used when a security system classifies an innocuous file or process as malware.
Reference:
How to download and install the IBKR Mobile app from alternative app stores
As a consequence of the US Government Huawei ban, the owners of Huawei smartphones will be no longer able to access the Google Play Store and download app from there. If you are affected by this constraint, you will still be able to download and install the IBKR Mobile app from an alternative app store.
Please proceed as follows:
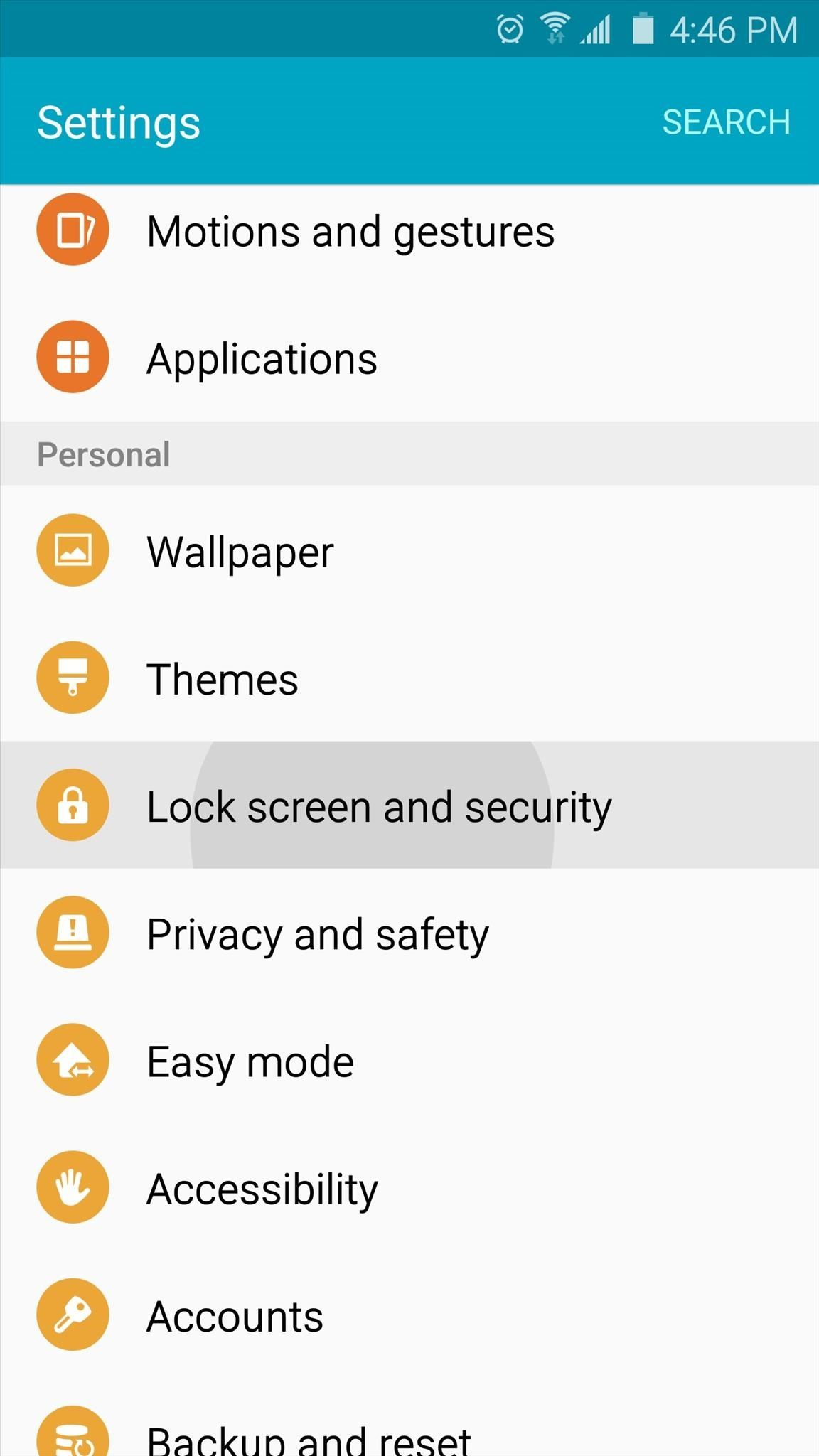
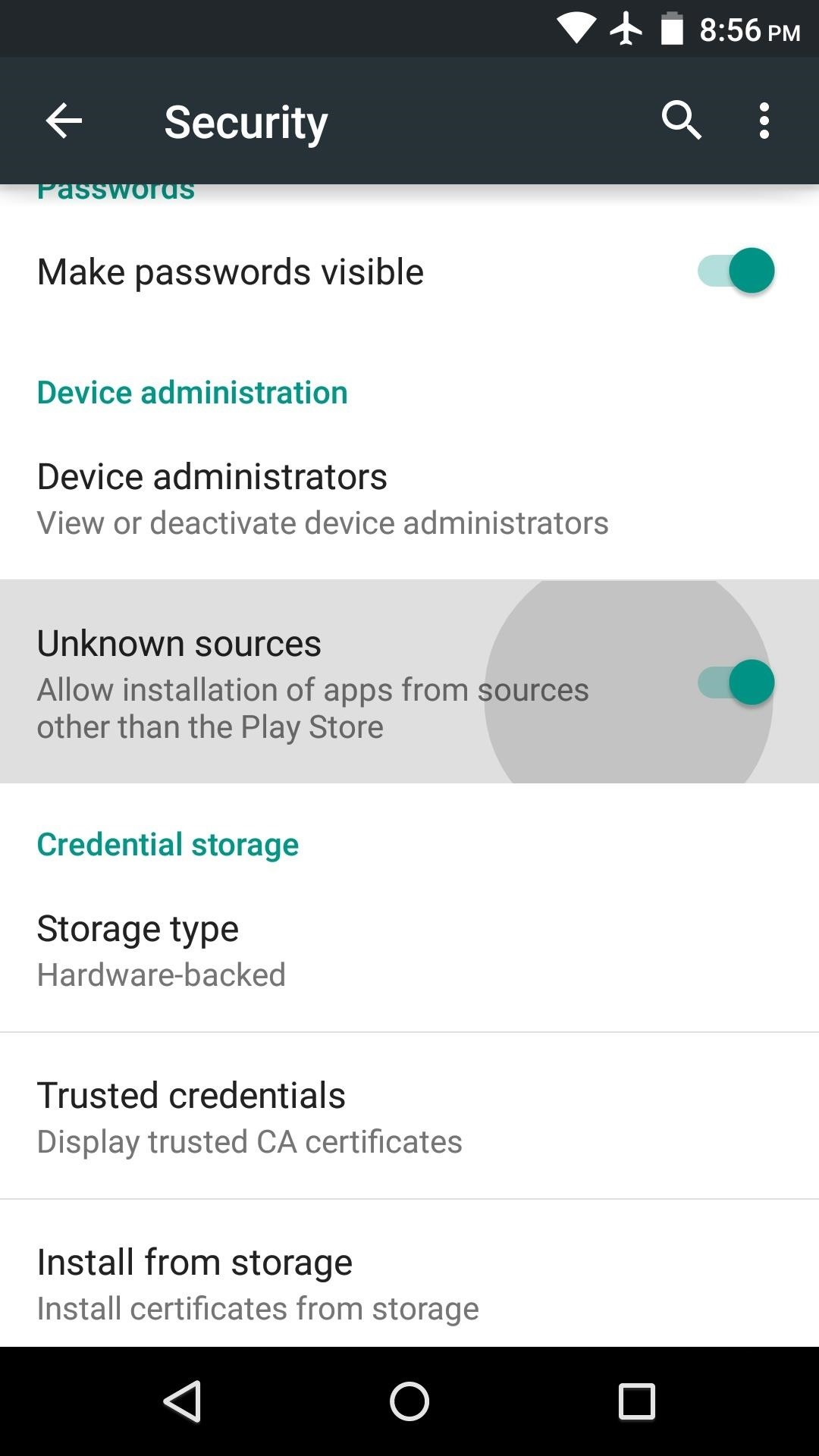
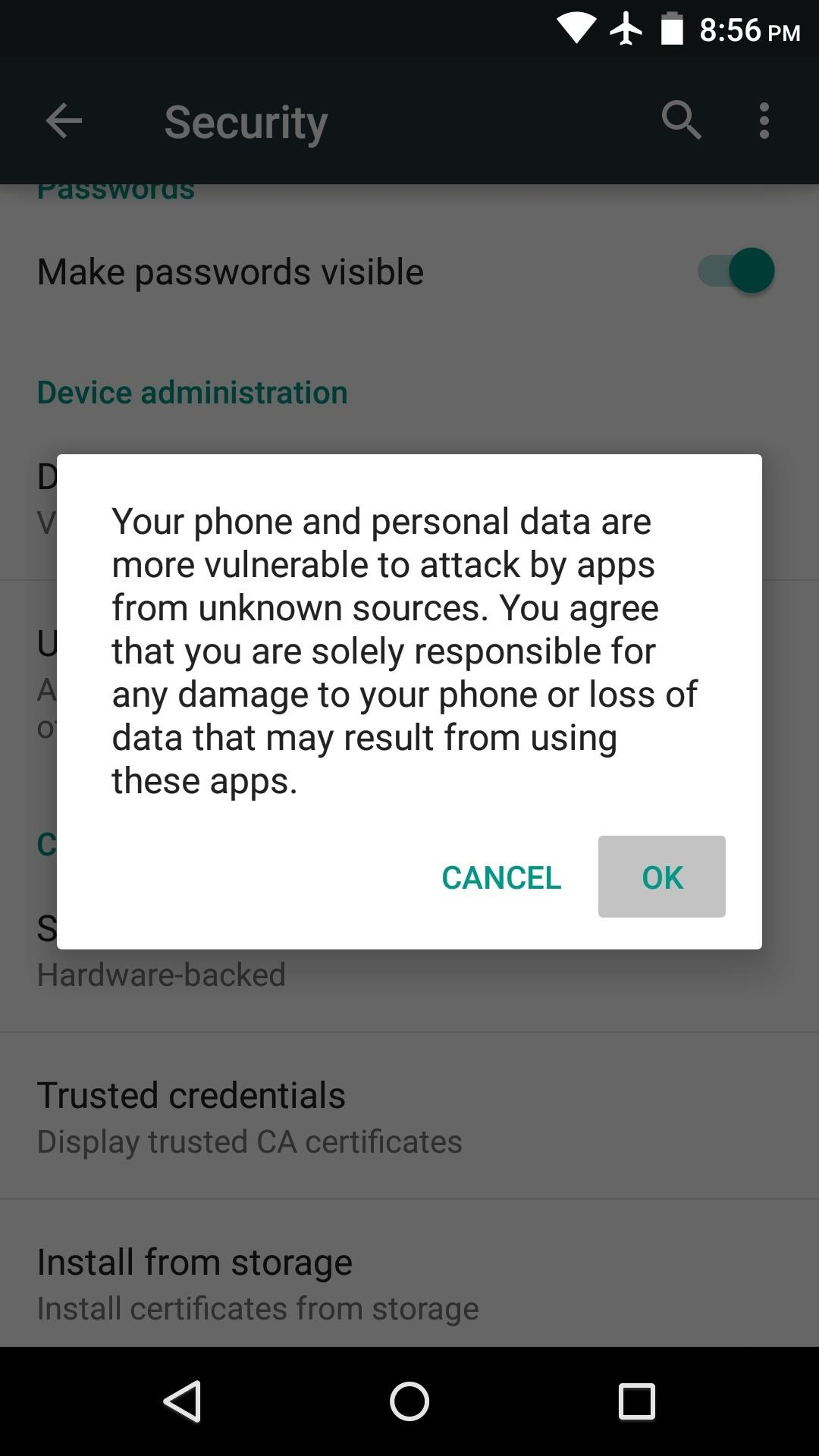
A) Allow your phone to install software from alternative app stores in this way:

2) Under the section System you will find the item Security (it can be called Lock Screen and Security). Click on it
B) You can now download the IBKR Mobile by clicking on one of the links below, according to the alternative store you want to use:
360.cn
.png)
Baidu
How to fix the "Cannot create ... file" error during TWS installation on MacOS
The filesystem permissions are controlled by your machines operating system. One of their functions is to secure your files, preventing unauthorized access or undesired modifications to the system and to your personal data.
Some software on your computer may modify or override the permissions assigned by the operating system. Under certain circumstances, this prevents the TWS installer from accessing the folder where the application core files have to be created (/users/youruser/home/Applications). In such cases, the TWS installation usually displays the error "Cannot create ... file. Shall I try again?"
Procedure:

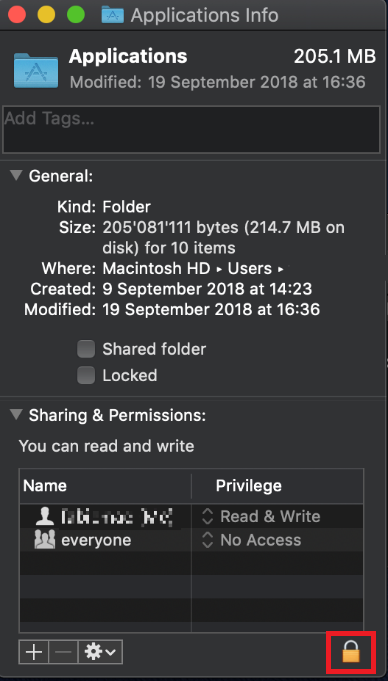
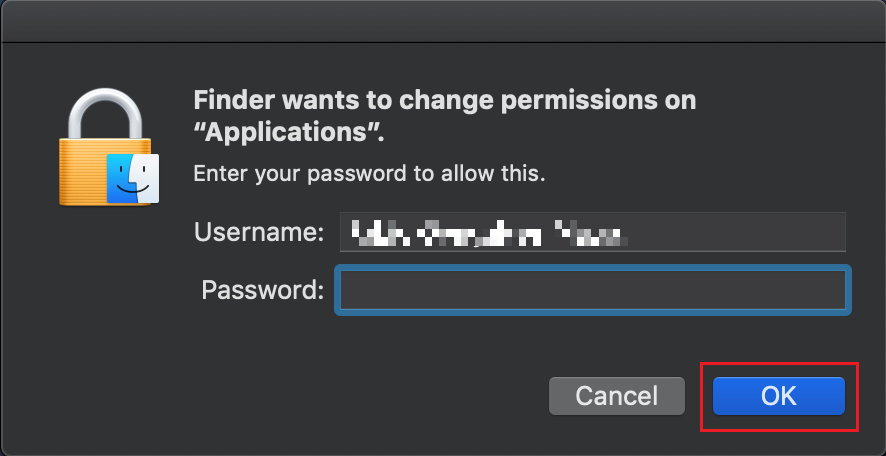
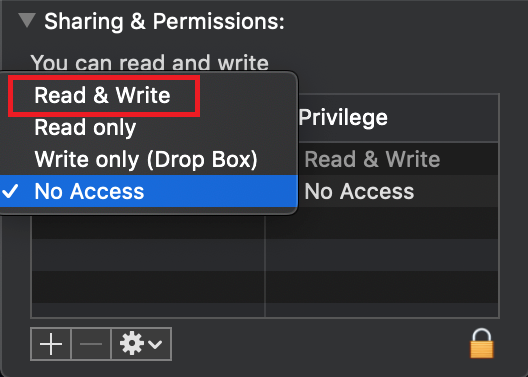
.png)
.png)
.png)
7. Once the installation has completed successfully, repeat the previous steps from 1. to 5. setting back the permissions of “everyone” to “Read Only” to revert your changes to the initial status
How to check and solve connectivity issues affecting the Trader Workstation (TWS)
The Trader Workstation (TWS) software needs to connect to our gateways and market data servers in order to work properly. Connectivity issues affecting your local network or your Internet Service Provider network may negatively affect the TWS functionality. In this article we will indicate how to test your connectivity using an automated connectivity test web page.
How to test the connectivity using the automated "IB Connectivity Test" web page?
2) Please wait until all the tests have been completed and results have been displayed. If you see "Success" as outcome for all tests, your connectivity to IB Servers is reliable at the present moment. No additional connectivity troubleshooting or configuration should be needed.
3) If you see "Fail" as outcome for one or more test/s, please click on the link "Fail" itself in order to display the "IB Network Troubleshooting Guide". That section will help you conduct some manual tests to identify the cause of the failure.
Note for Corporative environments and Proxy server users: the automated "Connectivity Test" page may return misleading results in case your machine is accessing the Internet through a Proxy server. This usually happens if you are connected to a company network. If this is your case, we kindly ask you to contact your Network Administrator or your IT Team and ask them to perform a manual connectivity tests towards the destination servers indicated in the table on the top of the IB automated "Connectivity Test" web page itself. The manual connectivity test should be conducted using destination TCP ports 4000 and 4001. Should they prefer to have the server list in another format or should they need to set up the firewall / IP Management rules, you can forward them this page.
IBKR Mobile Companion App for Apple Watch
Interactive Brokers takes our intuitive and ergonomic mobile trading platform to the next level by providing you a companion app for the Apple Watch.
The companion app is designed to display information when a user has logged in to the IBKR Mobile app on their iPhone. It will work in both the Live Trading and Read Only Modes but does not support active trading. This companion app is only available for informational purpose only.
Table of contents
What does the app do?
At 'glance view' the app will display the following information; Amount of FYI Notification, Account Number, Daily P&L, Net Liquidation Value, Number of Open Orders, Number of Trades Executed, Excess Liquidity and number of Positions you currently own. It will also display the time when it has fetched the information from your iPhone.
Example:
.jpg)
Requirements
- Must have iPhone 5s or greater, using iOS 11 or later.
- Must have the IBKR Mobile app installed on your iPhone (version 11 or greater)
- Must have your Apple Watch paired to your iPhone (refer to: Set up your Apple Watch for directions)
- Must have watchOS 5 running on your Apple Watch.
Important: The Apple Watch applications are only 'companion' apps. This means they are not installed directly on the watch itself, but rather are a function of an application already installed on your iPhone.
How is the app installed?
1. Install the latest version of the IBKR Mobile app on your iPhone.
2. Pair your Apple Watch to your phone.
3. Launch the Watch app on your phone.
4. Scroll down on the main screen until you see your list of apps, locate the IBKR Mobile app and Tap on it.
.jpg)
5. Enable Show App on Apple Watch by swiping the slider to the right (green).
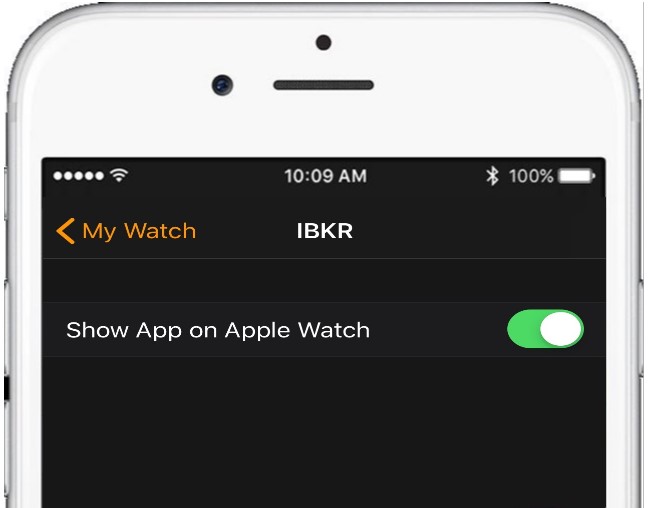
6. After the top slider is set to green, you will see a text informing you that the app is being installed. At this stage the phone is sending the application to your watch per Bluetooth. This might take a short moment (approximately 30-60 seconds.) Once completed the companion app has been installed.
Note: Once enabled it will take 24 hours before P&L shows up on the watch after activation.
.jpg)
How do I confirm the app is installed?
On your Apple Watch click on the crown to access your Home Screen, you should now see an icon for the IBKR Mobile App.

How to start multiple TWS sessions on a Mac
By default macOS does not allow the user to run multiple sessions of the same application. The following workaround can overcome this limitation in case you need to run the Trader Workstation for more than one user.
-
In case running different versions of the TWS is suitable to your needs, please follow the instructions on Procedure 1
-
In case you need multiple sessions of the same TWS version, please follow the instructions on Procedure 2
Procedure 1
1) Open the web page ibkr.com
2) Navigate to the menu Technology > TWS Software.
3) First download and install one of the auto-updating TWS versions (TWS LATEST or TWS according to your preference).
4) Once you have completed the installation, download and install one of the offline versions (OFFLINE TWS LATEST or OFFLINE TWS according to your preference).
5) You will then see on your Desktop two different Trader Workstation icons. You can use the first shortcut to start the first TWS session and the second one to start the additional one (see Figure 1.). Note: the link containing the version number in the name is the OFFLINE version. This will be a version that needs periodical manual updates.
Figure 1.
Procedure 2
1) Launch the first session of the Trader Workstation using the TWS icon present on your Desktop. If you still do not have any Trader Workstation icon, please go to the web page ibkr.com and click on the menu Technology > TWS Software. Then download and install one of the TWS versions displayed.
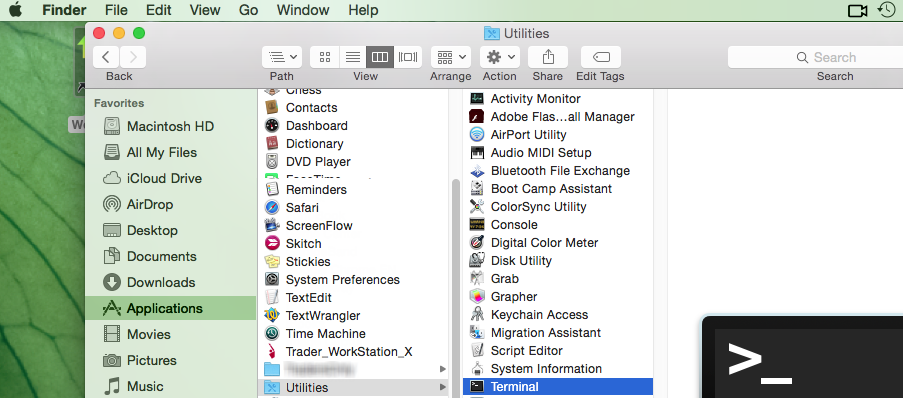
2) Open the Finder and click on Applications on the left side menu. Then select Utilities and then launch Terminal (see Figure 2.).
Figure 2.
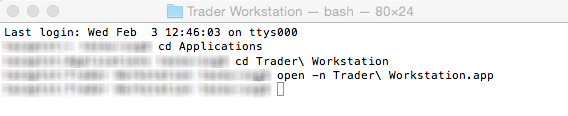
3) The Terminal will appear on the screen and will point to the home folder of your current macOS user. Then enter the commands listed below (see Figure 3.) on your Terminal. After each one, press ENTER on your keyboard.
cd Applications
cd Trader\ Workstation
open -n Trader\ Workstation.app
Figure 3.
4) The login window for your second TWS session will then appear on your Desktop. You can now close the Terminal.
Note: the procedure above presumes that the TWS executable is located in the following path: users/yourusername/home/Applications/Trader Workstation/Trader Workstation.app
If at the time you installed the TWS, you selected to install it for all the users of your system, then the TWS executable will be located here:
/Applications/Trader Workstation/Trader Workstation.app
and therefore you would need to issue the following commands in the Terminal:
cd /Applications
open -n Trader\ Workstation.app
How to overcome the warning message "The signature of the file is corrupt or invalid"
This article describes how to overcome the warning message which you might receive when you download the Trader Workstation or IB Gateway installation packages.
Since a Microsoft update has modified the signature validation mechanisms, the Trader Workstation and IB Gateway installation packages might be reported as having an invalid or corrupt signature, although their signature is indeed intact and absolutely valid.
If you are using Microsoft Edge as browser please follow all the steps below. If you are using any other browser start directly from point 3.
1. As soon as the installation package has been completely downloaded, you will notice on the bar at the bottom of your browser frame the warning message "The signature of the file tws-... is corrupt or invalid". Please click on the button View Downloads to open the DOWNLOADS panel. ![]()
2. Right click on the filename and select Run anyway.
.png)
3. Once the installer has been launched, the SmartScreen filter will display an additional warning message. Click on the link More Info.
(1).png)
4. Now click the button Run Anyway to allow the file execution. The installation will then start.