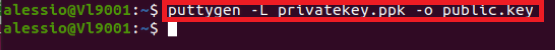
How to set up sFTP for using Certificate Authentication on Linux
These instructions apply to users who are receiving their statements via sFTP. If you elected to receive your statements via sFTP, you would first need to generate an RSA Key pair.
There are many Linux distributions and there are multiple methods to access the IBKR sFTP server. sFTP clients such as Filezilla can be used. In this article we explain how to realize the connection to the IBKR FTP server using Ubuntu Linux and Filezilla.
1. On your Linux machine, click on the Applications icon in the bottom left corner of you screen.
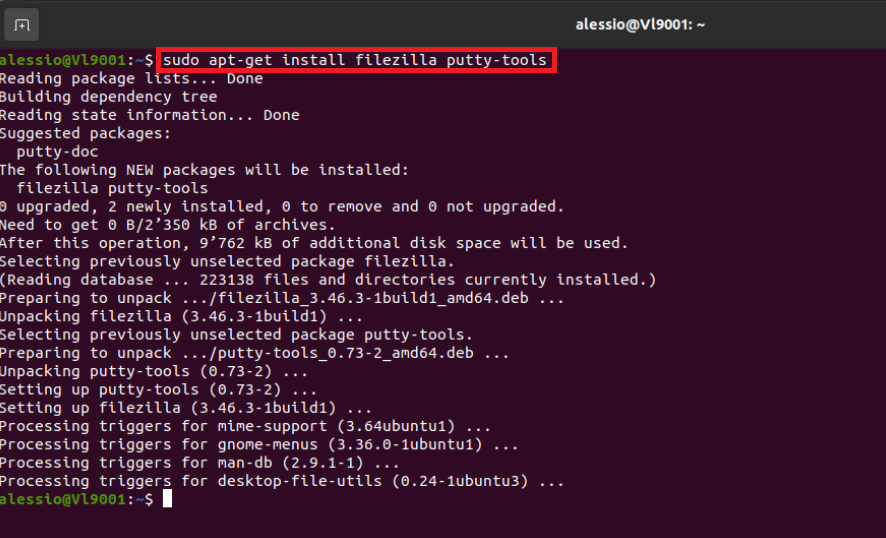
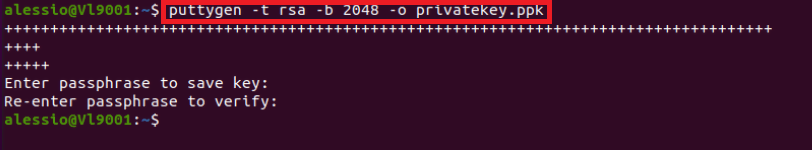
4. Once the software installation is complete, type puttygen -t rsa -b 2048 -o privatekey.ppk in order to generate the RSA Key pair.


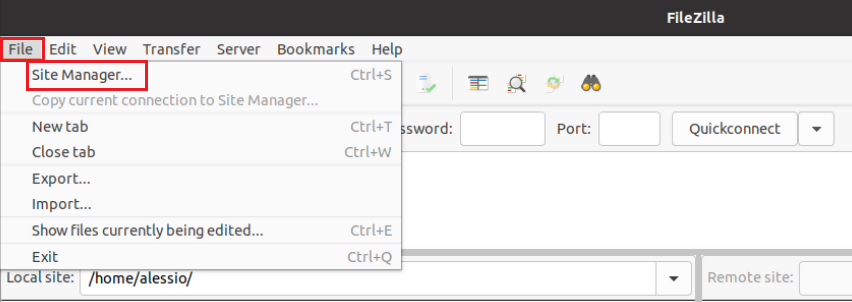
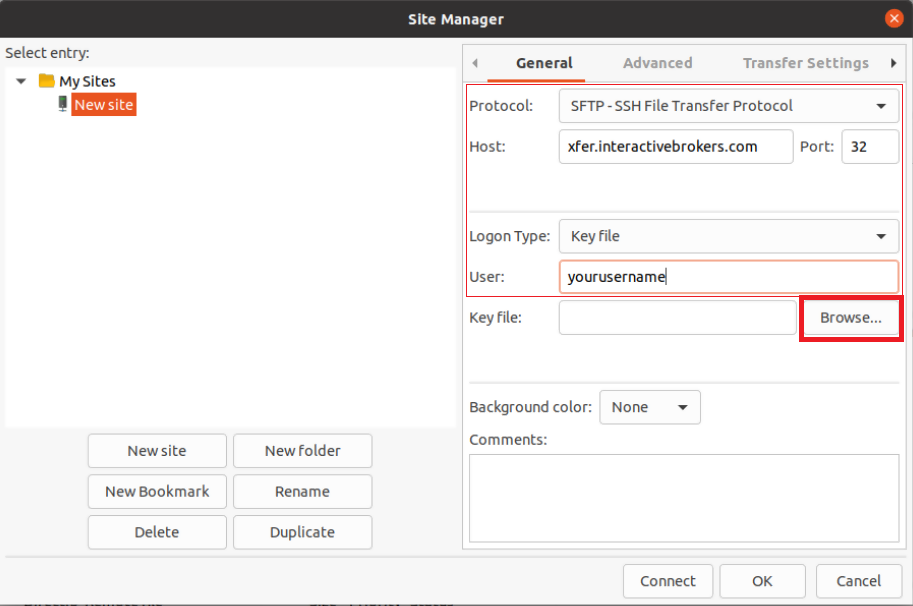
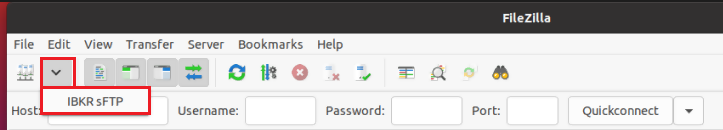
8. Click on the FileZilla top menu File -> Site Manager...
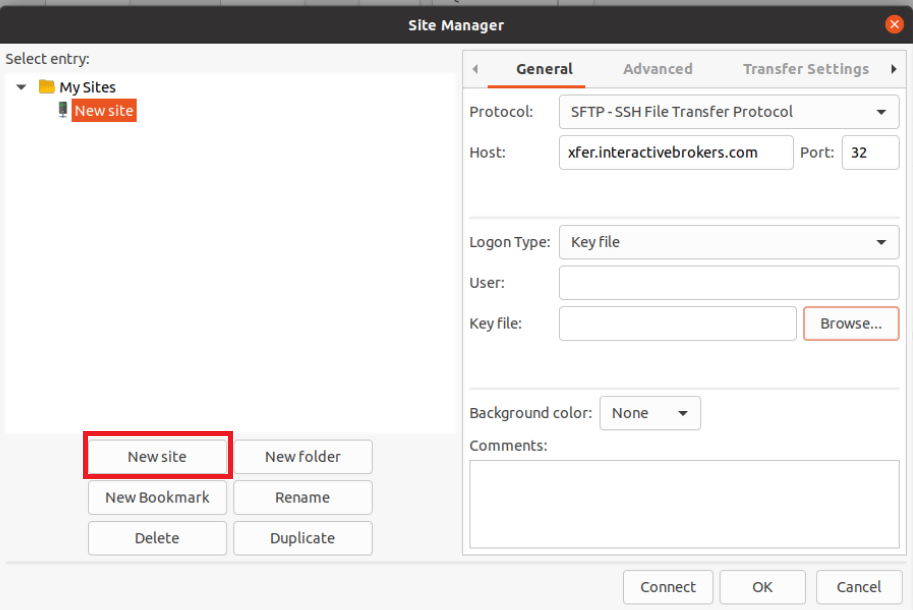
- Select SFTP - SSH File Transfer Protocol as Protocol
- Enter xfer.interactivebrokers.com in the Host field
- Enter 32 in the Port field
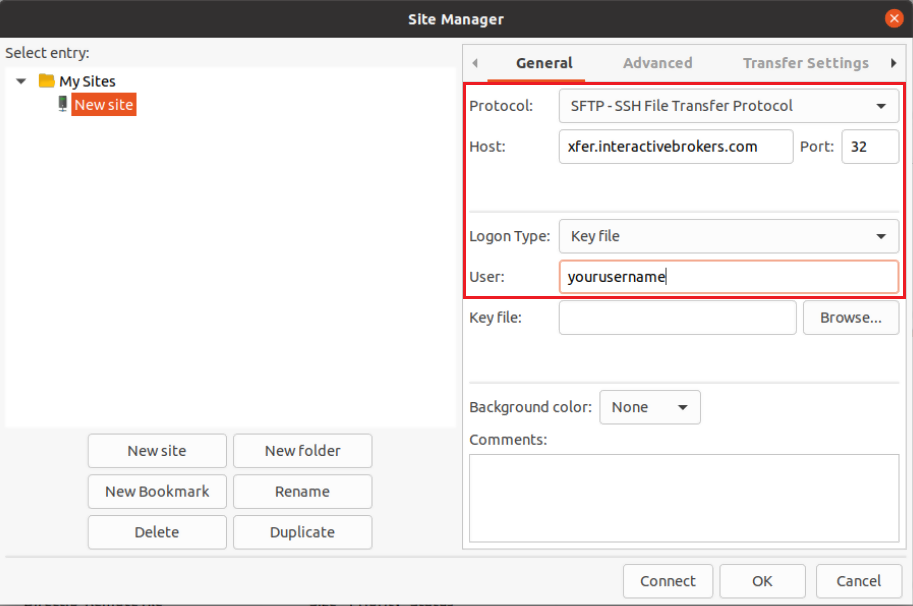
- Select Key file as Logon Type
- Enter the username provided to you by Interactive Brokers in the User field
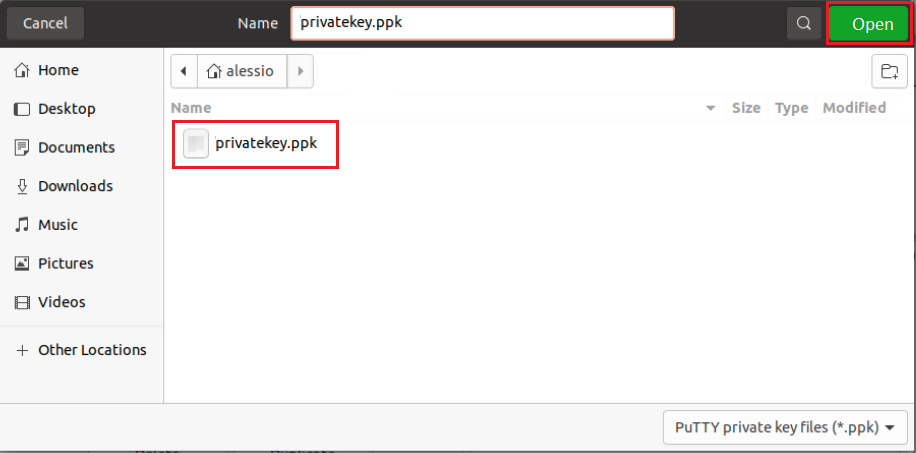
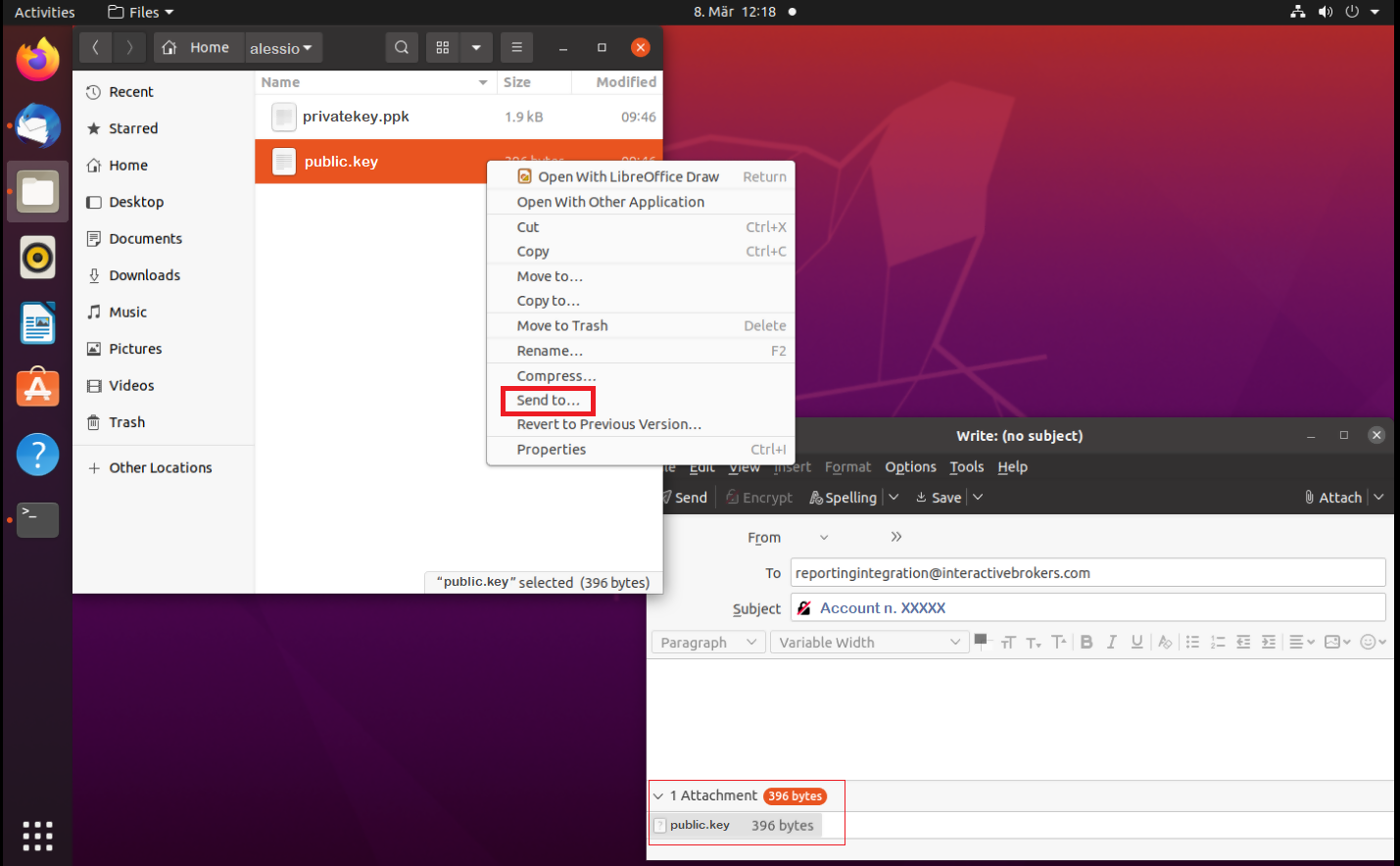
Important Note: do NOT send us your private key. Send us only your public one
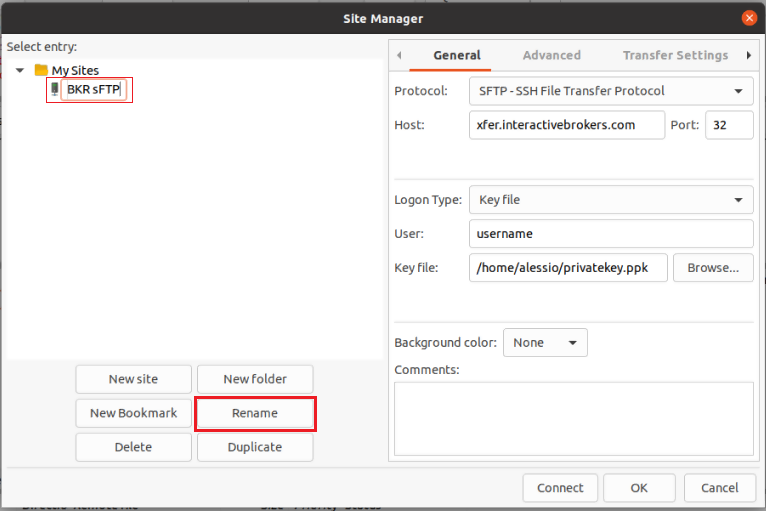
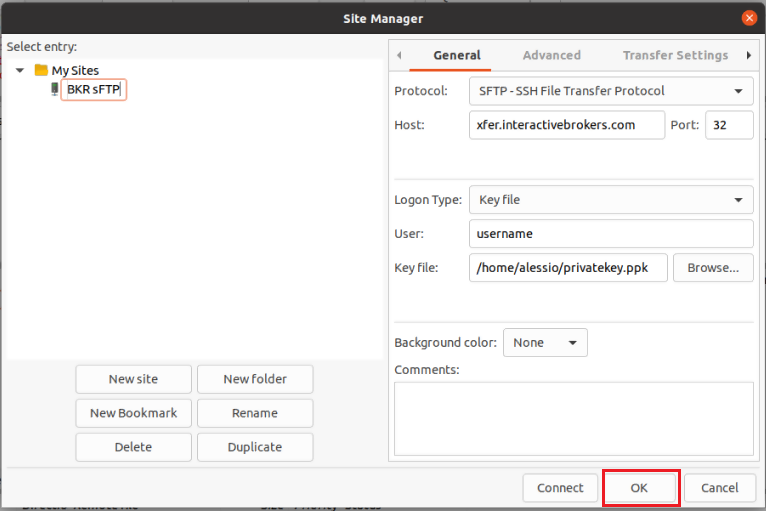
Once IBKR has configured the parameters for your connection on our servers, you will be notified. After that, you will be able to access your sFTP repository by using the Site connection you have created in FileZilla. In case you have not yet set up a Site connection, please follow the steps from 6. to 14. which are a prerequisite to the below steps:

Common issues and solutions
-
Ensure the correct login details are being used to connect to the sFTP server. The username and password you are entering should match the ones you have received from the Reporting Integration Team.
-
Confirm you have configured your sFTP Client to use the Private Key file for the logon authentication (see steps 9. and 10. of the above procedure.)
-
Try accessing the sFTP server using a different Client (CyberDuck, ect.)
-
Ensure the Private Key file being used to Authenticate the server login attempt is related to the Public Key you originally sent to the Reporting Integration Team.
-
Should the above checks be unable to resolve the issue, please generate a new RSA Public/Private Key pair and send only the Public part to the Reporting Integration Team, as per IBKB3842.
-
In case you have an antivirus or a security software installed on your machine, make sure it is not blocking the FTP connection attempt. Normally, security software allows to set up exceptions for specific connections in order to whitelist them.
-
Verify that the public IP Address of the machine running the sFTP client, is the same you have originally provided to the Reporting Integration Team for being whitelisted. You can discover your public IP Address by searching the Internet for “what is my IP”. If your current IP Address is not the same you provided to us, please send it to our Reporting Integration Team for being whitelisted.
-
Ask your network administrator/s to confirm that your firewall allows both incoming and outgoing traffic from/to xfer.interactivebrokers.com on port TCP 32.
-
Should the above steps be unable to resolve the issue, please generate a new RSA Public/Private Key pair and send only the new Public part to our Reporting Integration Team, as per IBKB3842.
KB3968 - Generate a key pair using GPG for Windows
KB4205 - Generate a key pair using GPG Suite on macOS
KB4108 - Decrypt your Reports using GPG for Windows
KB4210 - Decrypting Reports using your PGP Key pair on macOS
KB4407 - Generate RSA Key Pair on Windows
KB4410 - How to set up sFTP for using Certificate Authentication on macOS
KB4411 - How to backup your public/private Key pair
KB4323 - How to transfer your public/private key pair from one computer to another
Exchange name change
Overview:
Interactive Brokers is completing an effort to update and consolidate exchange names where appropriate. When this effort is complete, the following updates will be in effect:
- GLOBEX and CMECRYPTO will be consolidated to a single exchange, ‘CME’
- ECBOT will be updated to ‘CBOT’
- COMEX listed metals (previously reflected as NYMEX) will be updated to exchange ‘COMEX’
- NYMEX, no change
Given the breadth of products involved, we are migrating in four waves based on underlying products:
| Key | Effective Trade Date | Products |
| Wave 1 | October 30, 2022 | GLOBEX: ZAR, LB, DA, IXE |
| Wave 2 | November 6, 2022 | GLOBEX: EMD, BRE, CHF, SOFR3, E7, NKD CMECRYPTO: BTCEURRR, ETHEURRR, MET |
| Wave 3 | November 13, 2022 | GLOBEX: All remaining products CMECRYPTO: All remaining products ECBOT: ZO, ZR, 2YY, 30Y NYMEX: ALI, QI, QC |
| Wave 4 | December 4, 2022 | ECBOT: All remaining products NYMEX: All remaining "Metal" products |
I am trading via API, how does this impact me?
For API clients the only requirement would be to provide a new exchange name, for example: exchange=”CME”, for existing contracts for the affected exchanges.
Old exchanges names will no longer be available after the change.
More details can be found within our FAQs through the following link: Upcoming Exchange name Changes
Note: If you are using a third party software connected to TWS or IB Gateway and that software does not recognize the new contract definitions, please contact the third party vendor directly.
如何從IBKR平台上傳診斷包
某些支持相關的問題除了需要提供截圖外還需要上傳診斷文件與日志。這些信息可幫助我們調查幷解决您遇到的問題。
本文詳細說明了如何通各盈透證券交易平臺上傳診斷文件與日志。
請注意:IBKR不會實時監控診斷包信息庫。如果您在沒有盈透證券明確要求的情况下自行决定上傳診斷包,請通過諮詢單或電話通知我們的客戶服務人員,否則我們可能會注意不到您的錯誤報告。
請根據您使用的平臺點擊對應鏈接:
-
移動IBKR(Android版)
-
移動IBKR(iOS版)
- Windows和Linux操作系統:按Ctrl+Alt+Q
- Mac:按Cmd+Option+H
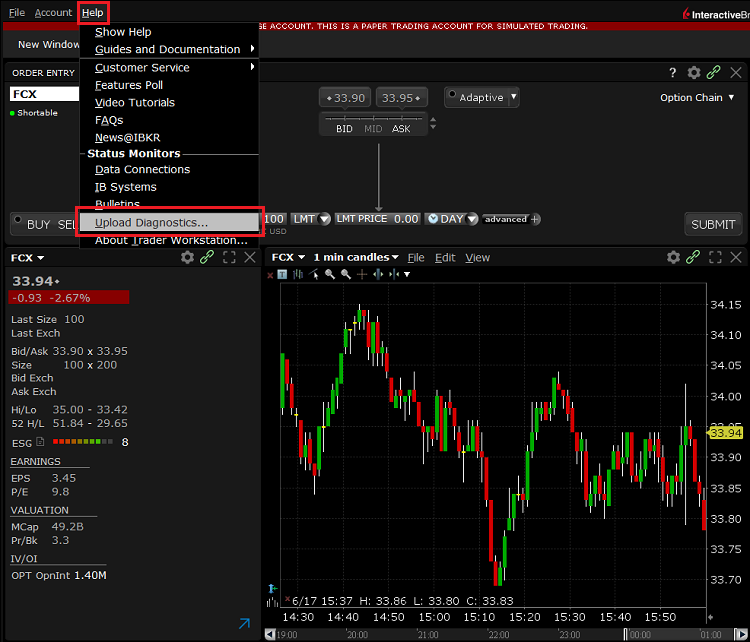
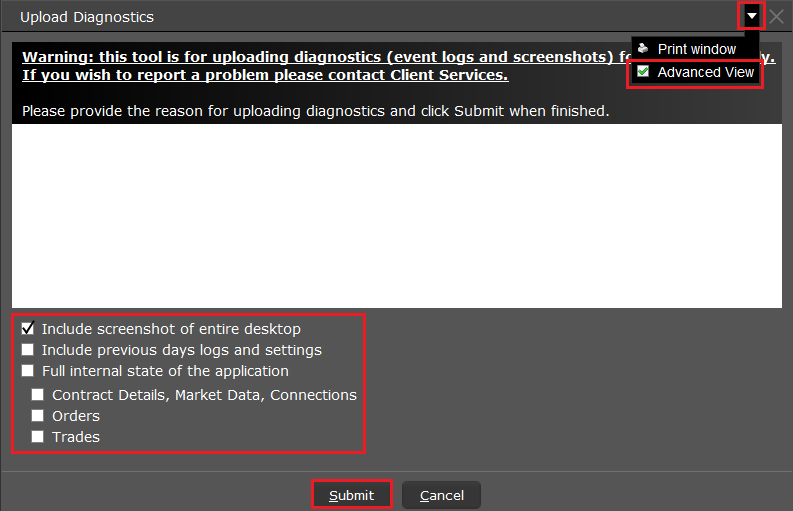
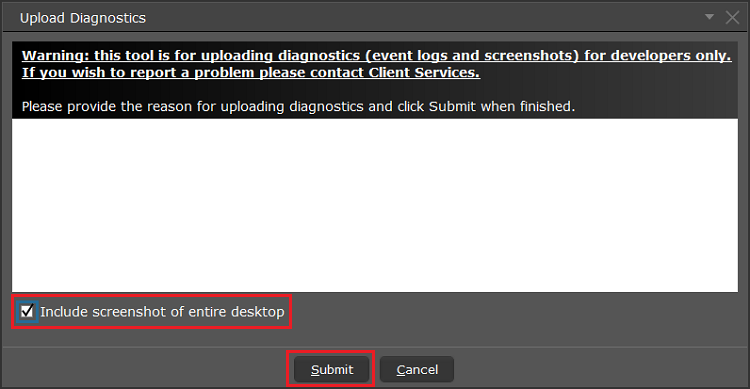
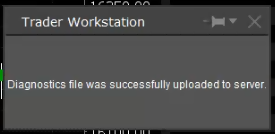
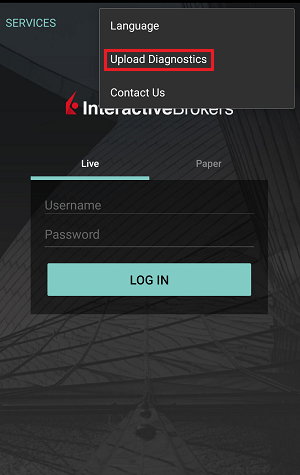
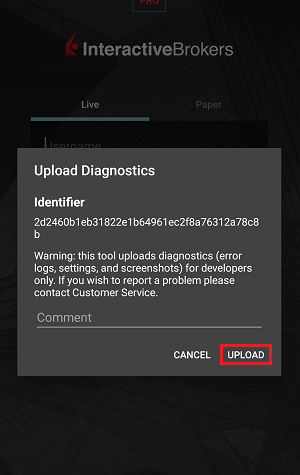
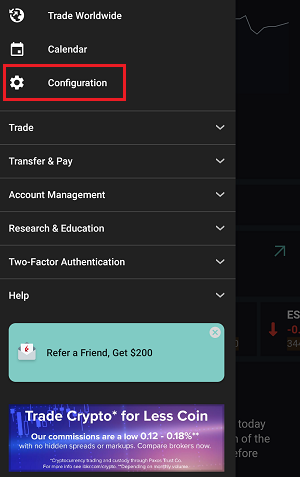
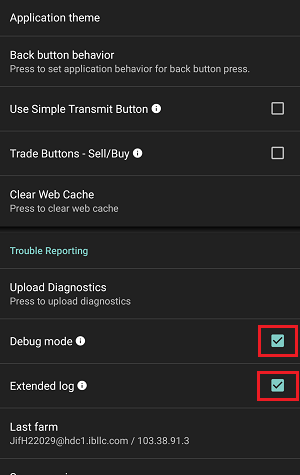
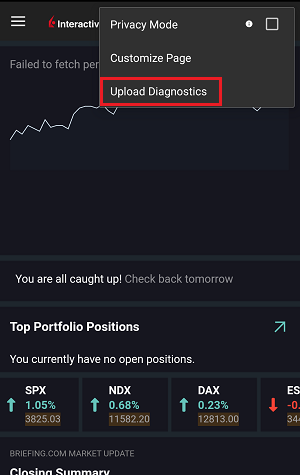
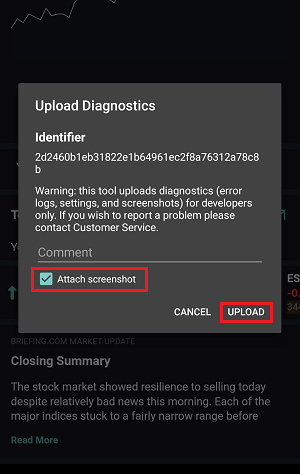

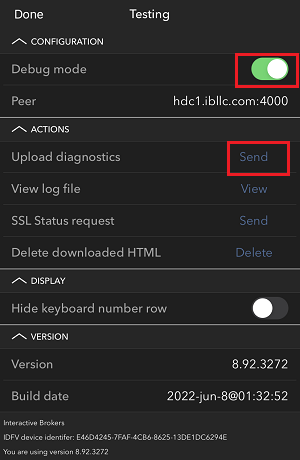
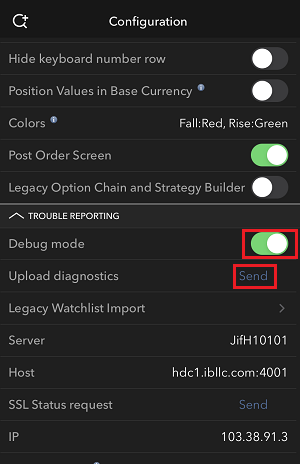
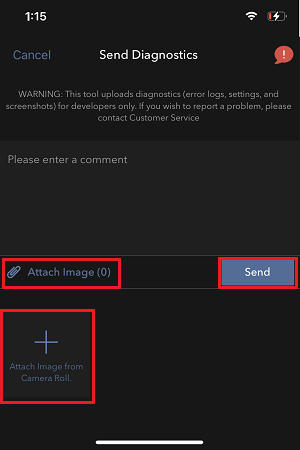
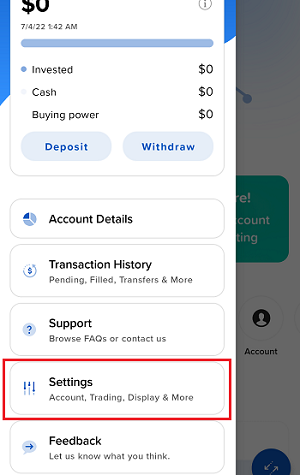
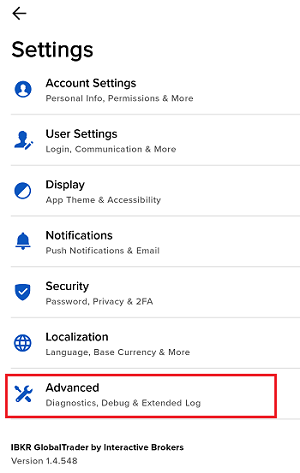
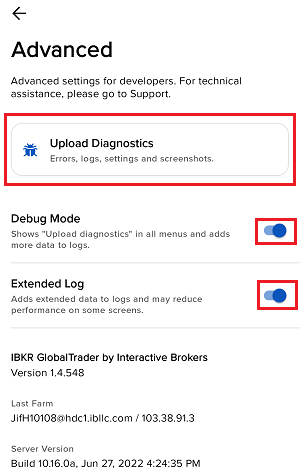
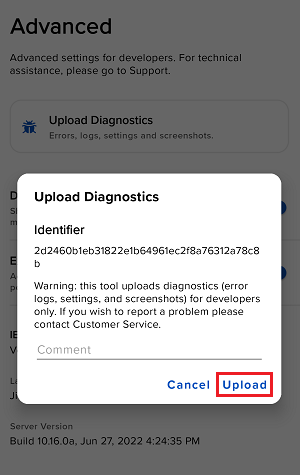
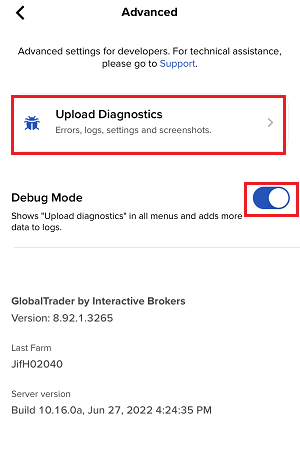
7. 輸入您的評論,點擊“附上圖片”按鈕附上您已保存到相册的問題頁面截圖
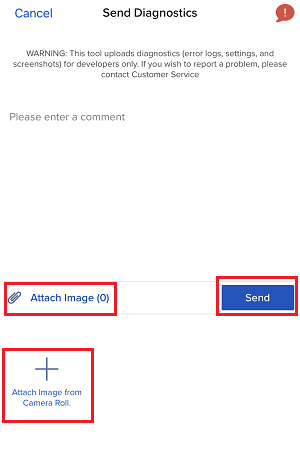
客戶端的診斷上傳請參見IBKB3512
How to Upload a Diagnostic Bundle from an IBKR Platform
Some support related issues require diagnostics files and logs to be uploaded along with screenshots. The information will help our team to investigate and resolve the issue that you are experiencing.
This article will help you with detailed steps on how to upload diagnostics files and logs from various Interactive Brokers’ trading platforms.
Note: IBKR does not monitor the diagnostic bundle repository throughout the day. Should you spontaneously decide to upload a diagnostic bundle, without being instructed by Interactive Brokers, please inform our Client Services via Message Center ticket or phone call otherwise your error report will go unnoticed.
Please click on one of the links below, according to the platform you are using:
-
IBKR Mobile (Android)
-
IBKR Mobile (iOS)
- For Windows and Linux Operating system: Press Ctrl+Alt+Q
- For Mac: Press Cmd+Option+H






















7. Enter your comments in the field and tap ‘Attach Image’ to attach the screenshot/s you previously saved in your camera roll

A diagnostic trace for Client Portal can be captured following the steps on IBKB3512
如何生成".har"文件
在解決重大的網站問題時,有時我們的客服團隊需要您提供有關您的瀏覽器的更多信息。我們可能會要求您錄製並提供.har文件。該文件包含有關您的瀏覽器發送及收到的網絡請求的更多信息。您的瀏覽器可在問題發生時記錄HTTP/HTPS請求和響應的內容、時間軸及狀態,從而生成此類文件。
我們將在本文中解釋如何生成.Har文件。請在下方點擊您正在使用的瀏覽器:
1. 打開Google Chrome並前往發生問題的頁面。
2. 點擊鍵盤上的 CRTL +SHIFT + I 。或者,點擊Chrome菜單圖標(瀏覽器窗口右上角的三個垂直點),然後選擇 “更多工具” > “開發者工具”
3. “開發者工具”會以停靠面板的形式在Chrome側面或底部打開。選擇 “網絡”選項卡(如圖1)
圖1
.png)
4. 在 “開發者工具” 工具欄左上角找到圓形的“錄製”按鈕並確保它是紅色的。如果它是灰色的,點擊一次開始錄製或點擊 CTRL+E (如圖2)
圖2
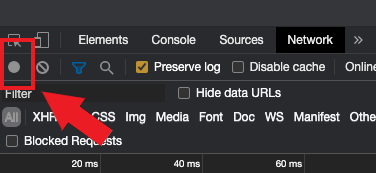
5. 激活 “保留日誌”選項框(如圖3)
圖3
.png)
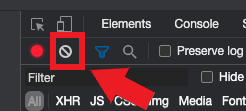
6. 點擊 “清除” 按鈕清除已有的日誌。“清除” 按鈕顯示為停止圖標,位於 “錄製” 按鈕的右側 (如圖4)
圖4
7. 再現您遇到的問題並錄製網絡請求。
8. 當您完成問題再現後,右擊已記錄的網絡請求列表上的任意地方,選擇 “以HAR格式保存所有內容”, 並將文件保存在您計算機上任意您想保存的位置(如桌面)。
9. 在IBKR客戶端中, 前往消息中心並創建 一個新的網絡諮詢單(或使用已有的諮詢單)
10. 在網絡諮詢單內,將之前生成的.har文件作為附件添加。 如果IBKR客服向您提供過諮詢單號或客服代表的名字,請在諮詢單中加上這些信息。
11. 提交網絡諮詢單
1. 打開Firefox並前往發生問題的頁面
2. 點擊鍵盤上發 F12 。或者,點擊Firefox菜單按鈕(瀏覽器窗口右上角的三條平行線),然後選擇 Web 開發者工具 > 網絡
3. 開發者網絡工具會以停靠面板的形式在Firefox底部打開。選擇 “網絡”選項卡(如圖5)
圖5
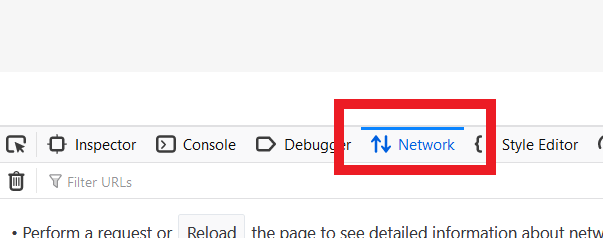
4. 激活 “保存日誌”選項框(圖6)
圖6
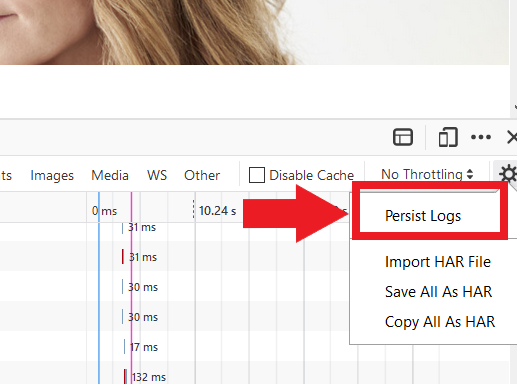
5. 再現您遇到的問題。系統會自動開始錄製網絡請求。
6. 再現問題後,右擊已錄製的請求列表並選擇“所有內容另存為HAR”
7. 將文件保存在計算機上的任意位置(如桌面)
8. 在IBKR客戶端中, 前往消息中心並創建 一個新的網絡諮詢單(或使用已有的諮詢單)
9. 在網絡諮詢單內,將之前生成的.har文件作為附件添加。 如果IBKR客服向您提供過諮詢單號或客服代表的名字,請在諮詢單中加上這些信息。
10. 提交網絡諮詢單
1. 打開Edge並前往發生問題的頁面。
2. 點擊鍵盤上發 F12 。或者點擊Edge菜單圖標(瀏覽器窗口右上角的三個平行點),然後選擇 “更多工具” > “開發者工具”
3. 點擊“網絡” 圖標 (如圖10)
圖10
.png)
4. 再現您遇到的問題並錄製網絡請求。
5. 完成後,點擊軟盤圖標(導出為HAR) 或按 CTRL+S (如圖11)
圖11
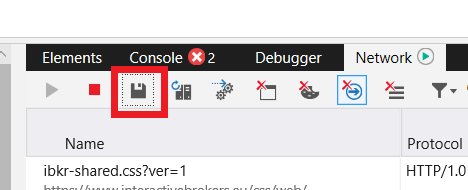
6. 為文件命名並將文件保存在您計算機上的任意位置(如桌面)。然後點擊 “保存” 按鈕
7. 在IBKR客戶端中,前往消息中心並創建一個新的網絡諮詢單(或使用已有的諮詢單)
8. 在網絡諮詢單內,將之前生成的.har文件作為附件添加。 如果IBKR客服向您提供過諮詢單號或客服代表的名字,請在諮詢單中加上這些信息。
9. 提交網絡諮詢單
注:在生成HAR文件前,請確保您可在Safari中看到 “開發者” 菜單。如果您看不到這個菜單,請點擊Safari瀏覽器,選擇 “偏好設置”, 前往 “高級” 選項卡並激活菜單欄 “顯示開發”菜單旁的選項框。
1. 打開 “開發” 菜單並選擇 “顯示網頁檢查器” 或點擊 CMD+ALT+I
2. 點擊 “網絡” 選項卡 (如圖12)
圖12
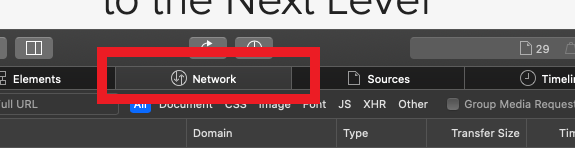
3. 激活 “保留日誌”選項卡(圖13)
圖13
.png)
4. 點擊 “導出” 圖標(或按CMD+S), 為文件命名並將其保存在計算機上的任意位置(如桌面)並保存.har文件
5. 在IBKR客戶端中,前往消息中心並創建一個新的網絡諮詢單(或使用已有的諮詢單)
6. 在網絡諮詢單內,將之前生成的.har文件作為附件添加。 如果IBKR客服向您提供過諮詢單號或客服代表的名字,請在諮詢單中加上這些信息。
7. 提交網絡諮詢單
Generate RSA Key Pair on Windows
These instructions apply to users who are receiving their statements via sFTP. If you elected to receive your statements via sFTP, you would first need to generate an RSA Key pair.
To generate an RSA Key pair:
2. Run the installer and make sure to check PuTTYgen (key generator) as one of the components to install.
3. Start WinSCP and from the button Tools select Run PuTTYgen.
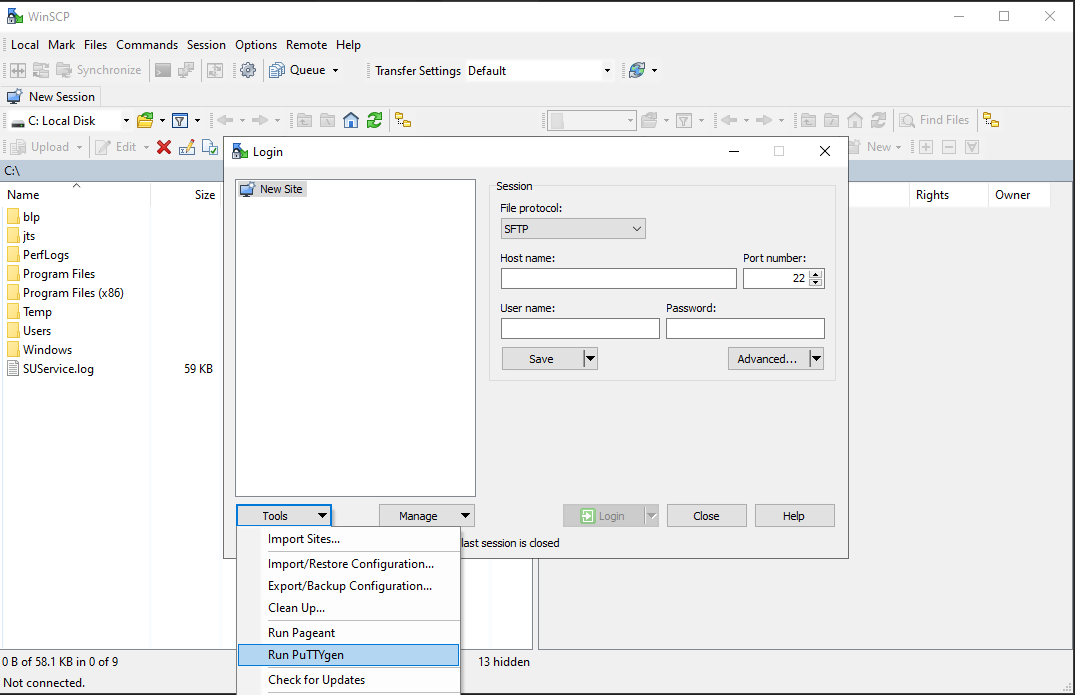
4. Once the tool PuTTYgen has been launched, click Generate. Select RSA as Type of key to generate, 2048 as Number of bits in generated key and click on the button Generate.
5. Click "Save private key" and give the file a name (like private). Leave the extension as .ppk ('ale.ppk', in the picture below is an example filename).
Important Note: do NOT save your public key yet. Save only your private one.
.png)
6. Open WinSCP, create a new connection and:
- Select SFTP as File protocol.
- Enter xfer.interactivebrokers.com in the Host name field.
- Enter 32 in the Port number field.
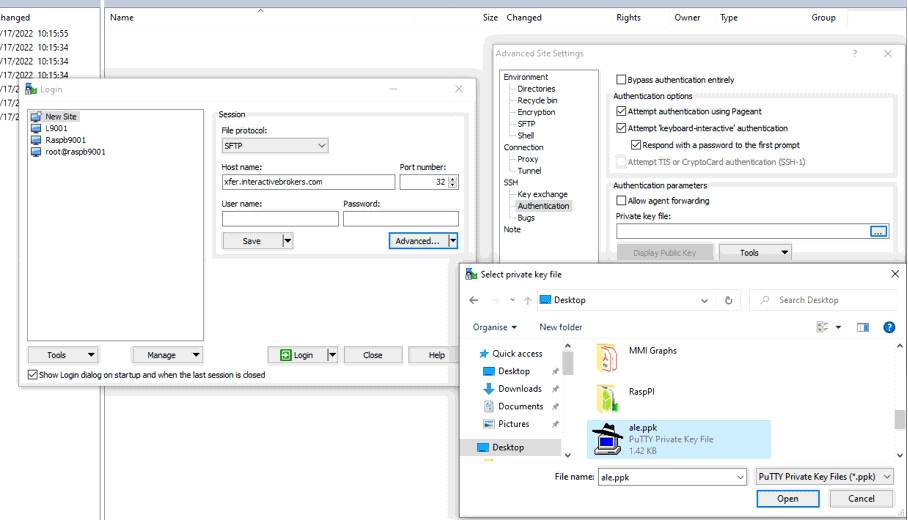
8. In the Advanced Site Settings screen, left side menu, expand SSH and select Authentication. Click on the button ... at the end of the field Private Key file and open the private key you previously saved at point 5):
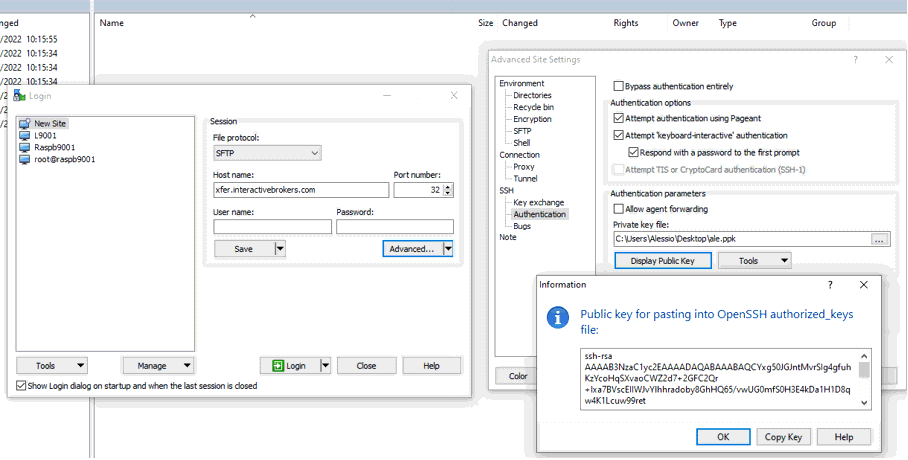
9. Click on the button Display public key:
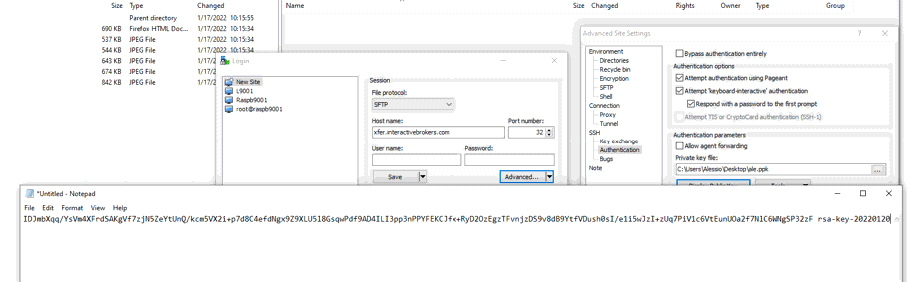
11. Open Notepad, press CTRL+V to paste the key string (which is one string of characters without spaces) and then save the file with the name public.key in a folder of your preference:
12. Send the file you saved at the previous step to us via Message Center ticket or email as per instructions on IBKB3842
KB3842 - Using GPG/RSA encryption keys to guarantee the privacy and security of your Reports
KB3968 - Generate a key pair using GPG for Windows
KB4205 - Generate a key pair using GPG Suite on macOS
KB4108 - Decrypt your Reports using GPG for Windows
KB4210 - Decrypting Reports using your PGP Key pair on macOS
Transferring your Key Pair From One Computer To Another
If you need to decrypt files that were encrypted with your private Key on an additional computer, you need to copy both your private and public keys (the entire Key pair) to that computer.
Note: this tutorial assumes you have already set up a Key pair. If you need guidance to set up the Key pair please refer to this article, which is a prerequisite to the instructions below.
How to transfer your Key pair:
Please select one of the below links, according to your Operating System:
Windows
1. On the machine where the encryption keys are stored, connect a USB drive to a free USB port.
2. Launch the Kleopatra application and select the encryption key you want to transfer. Then right-click on the selection and choose Backup Secret Keys...
Note: Do NOT use Export..., as this will only export the public part of the Key while you need to have a backup of both public and private parts.
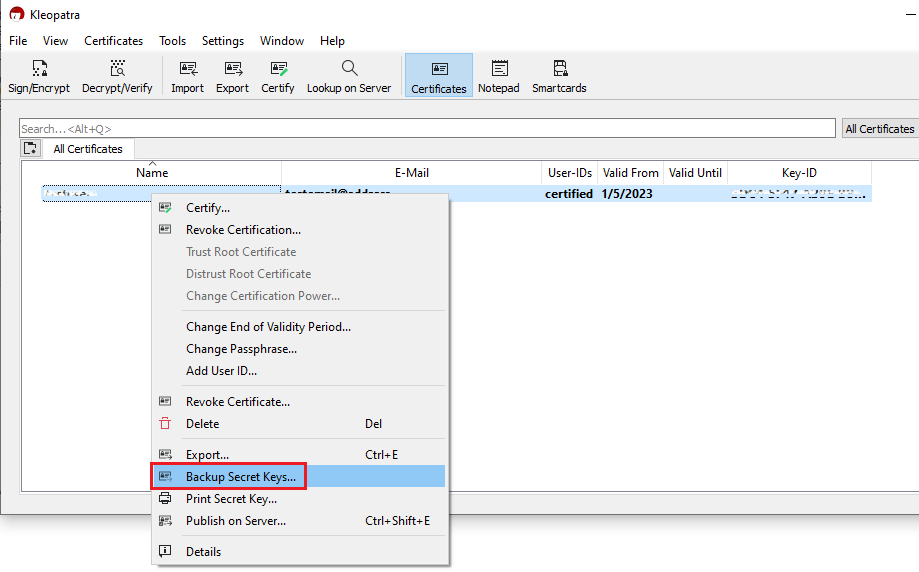
3. Select your USB drive as destination and a filename of your preference (e.g. secret-key-KEYID.asc) for your backup copy. Then click Save.
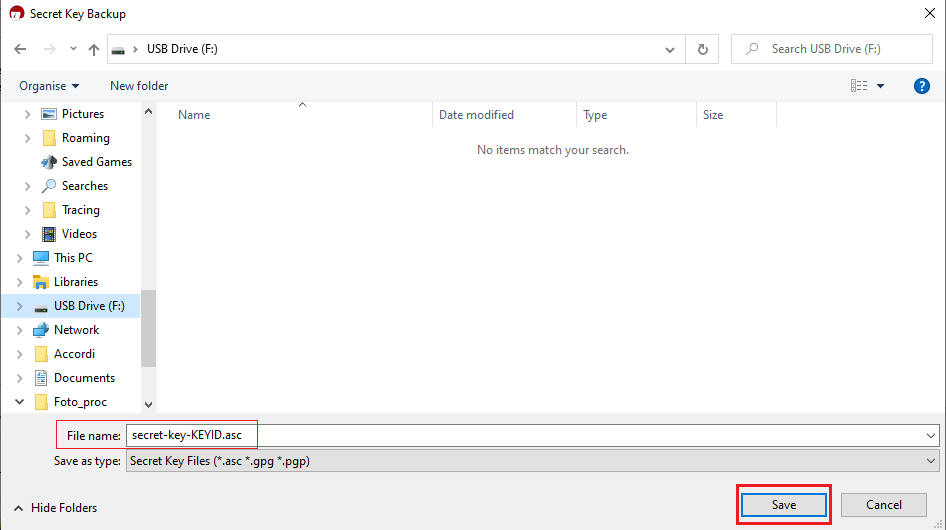
4. Enter the passphrase you have set when you created the Key and click OK.
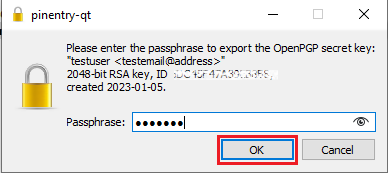
5. A pop-up will confirm the backup has been successfully created. Click OK.
6. Eject your USB drive safely through the Windows interface to prevent data loss and connect it to a free USB port on the other computer (the one you want to transfer the key to). All the next steps have to be executed on that machine.
7. Make sure the the GPA software is installed, otherwise please install it. Make sure that the component Kleopatra is selected as one of the sub components to include in the installation.
8. Launch the Kleopatra application and click on the top menu File and select Import...
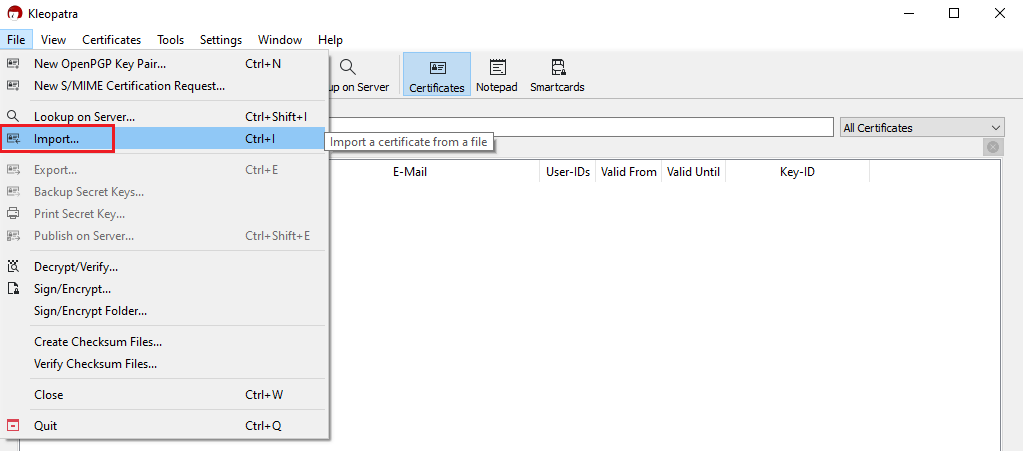
9. Click on the letter correspondent to your USB drive and select the file you have previously saved (e.g. secret-key-KEYID.asc). Then click Open.
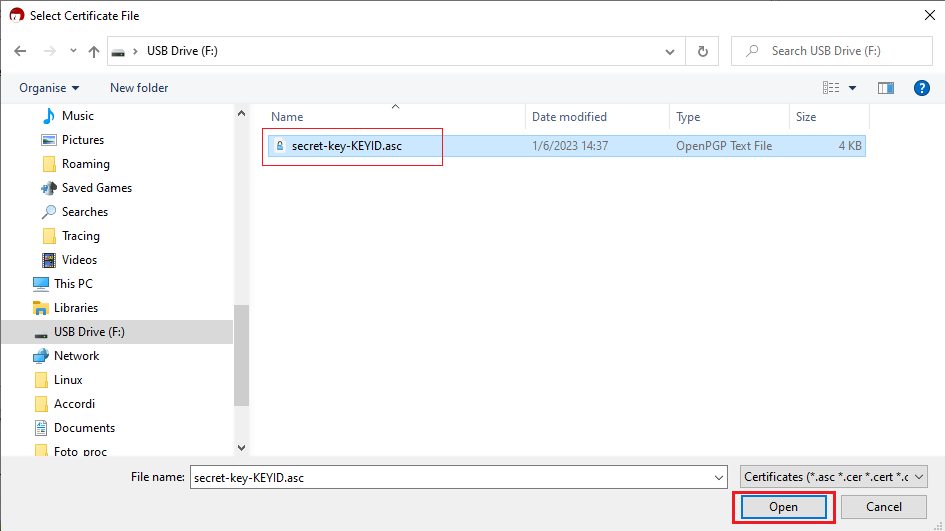
10. Click on Yes, It's Mine.
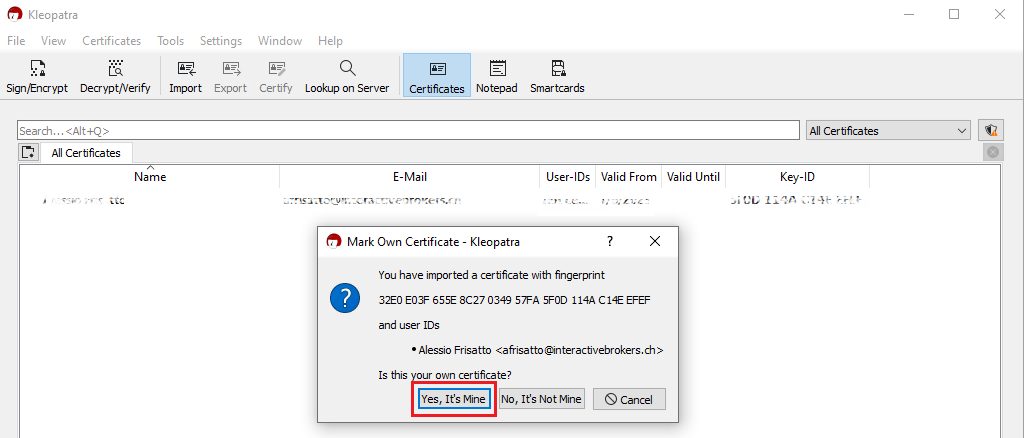
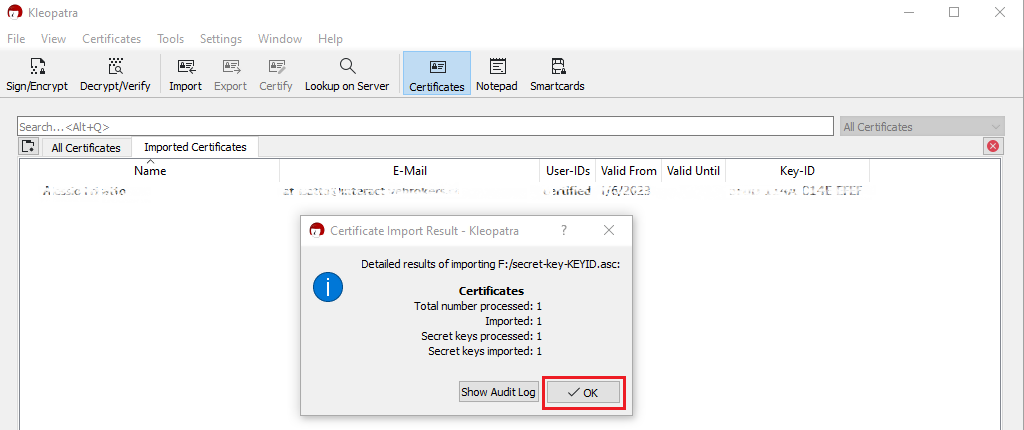
11. A pop-up will confirm the Key has been successfully imported. Click OK. You may now want to delete the key file from the USB drive and empty the Trash.
macOS
1. On the machine where the encryption keys are stored, connect a USB drive to a free USB port.
2. Launch the GPG Keychain application and select the encryption key you want to transfer. Please make sure that you see the text Type: Secrete and public key, in the Type column.
.png)
3. With the desired encryption key highlighted, click Export. Please make sure to check the box for the option Include secret key in exported file, as illustrated in the above screenshot. Save the key pair to the USB drive.
4. Eject the USB drive and connect it to a free USB port on the other computer (the one you want to transfer the key to). All the next steps have to be executed on that machine.
5. Make sure the GPG Tools suite is installed, otherwise please install it.
6. Launch the GPG Keychain application and click the icon Import on the top toolbar.
(1).png)
7. Click the USB Drive and select the previously saved .ASC file that contains the Public and Private key. Then click Open.
8. The confirmation should read Import successful.
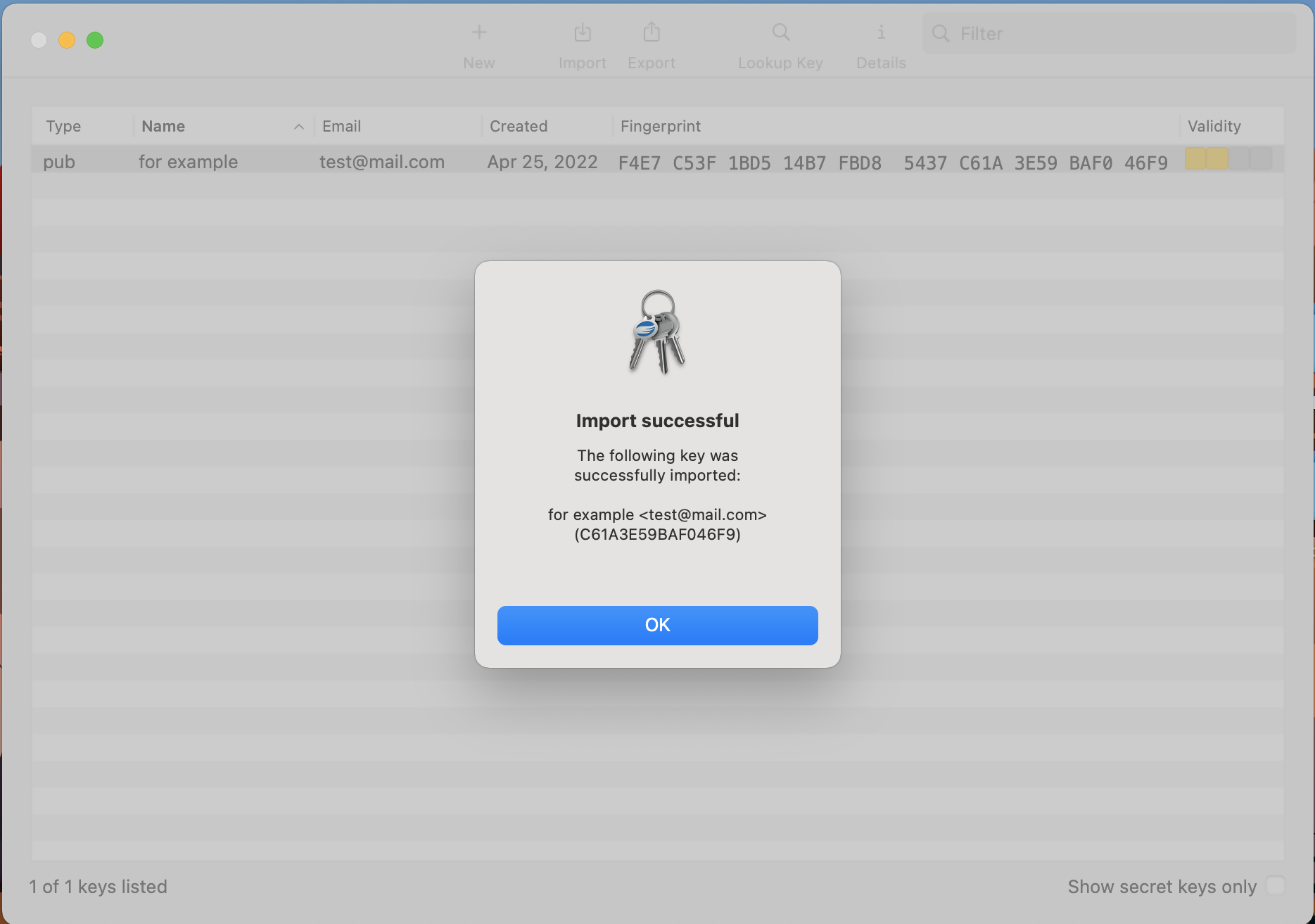
9. Once the key has been successfully imported, delete the key file from the USB drive and empty the Trash.
KB3842 - Using GPG/RSA encryption keys to guarantee the privacy and security of your Reports
KB3968 - Generate a key pair using GPG for Windows
KB4205 - Generate a key pair using GPG Suite on macOS
KB4108 - Decrypt your Reports using GPG for Windows
KB4210 - Decrypting Reports using your PGP Key pair on macOS
KB4407 - Generate RSA Key Pair on Windows
Decrypting Reports Using Your PGP Key Pair on macOS
Note: This tutorial assumes you received reports via email or via FTP that were encrypted with the public key you sent to IBKR . If you need guidance to set up the encrypted statement delivery, please refer to this article, which is a prerequisite to the instructions below.
1. Open Finder
2. Right click on the .gpg file you want to decrypt
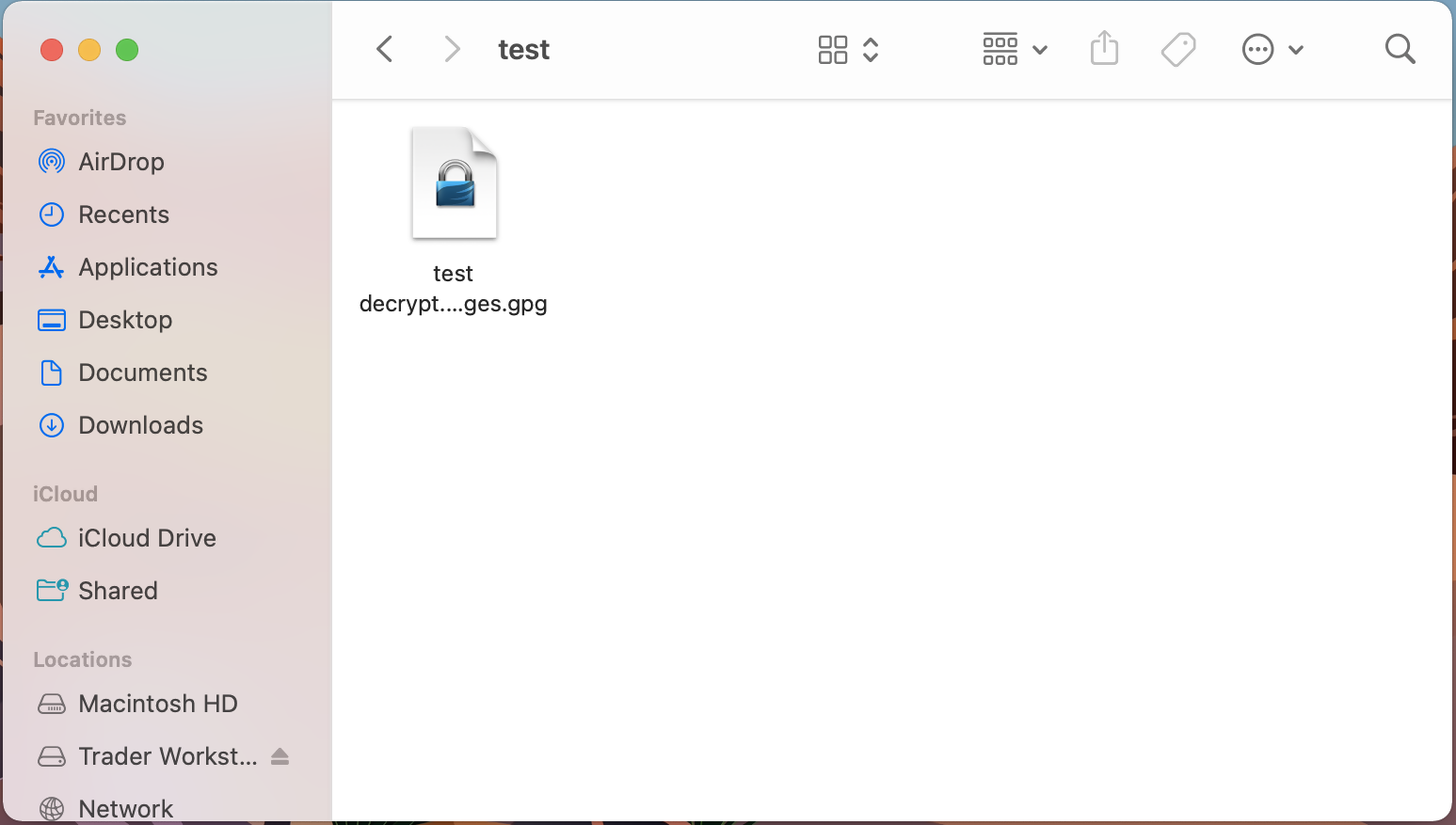
3. Select Services > OpenPGP: Decrypt File
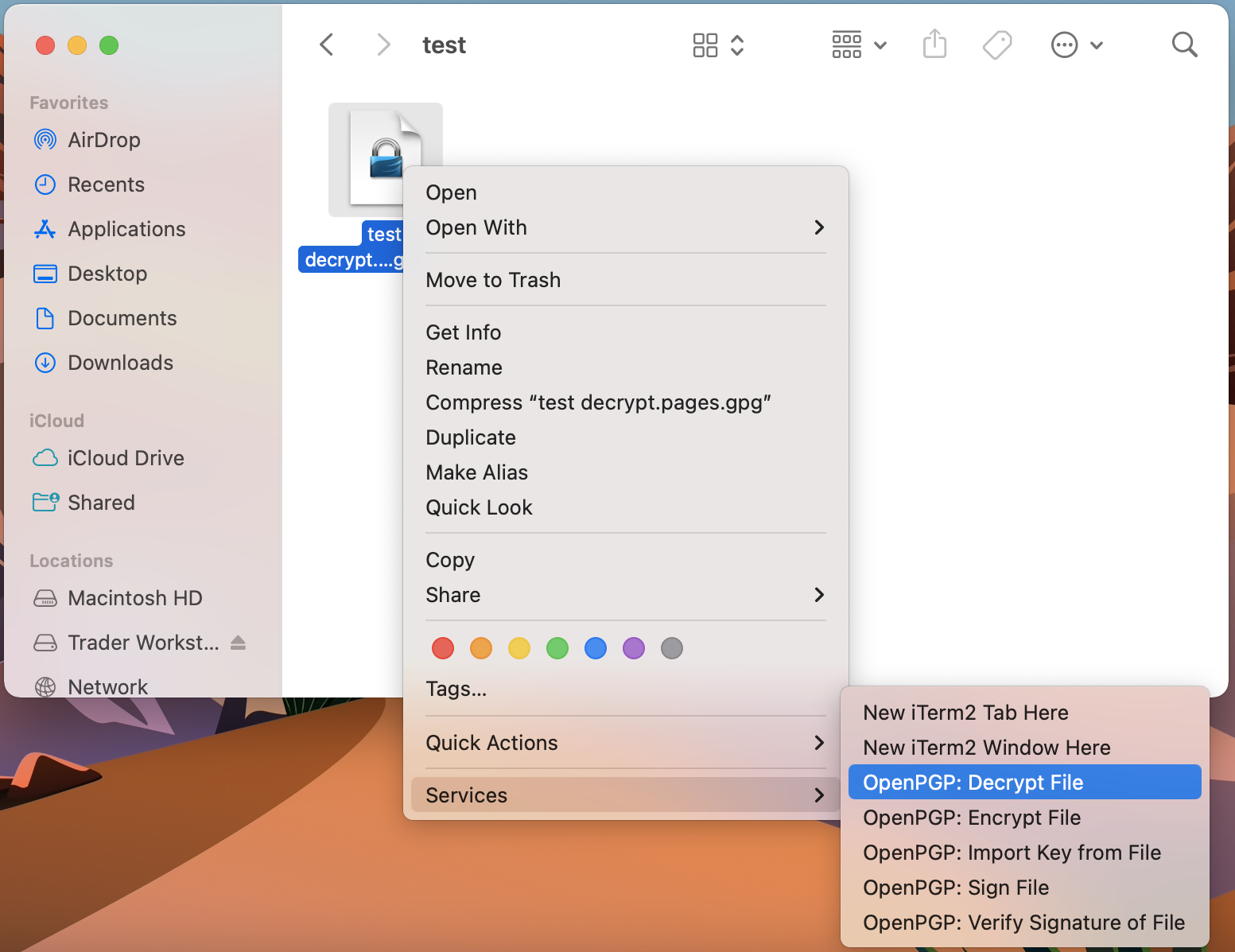
Common Issues/Questions
- Decryption failed with error 'No Secret Key'
This is commonly caused when the wrong encryption key is used to decrypt the file. If decryption is being done on a computer other than the original computer used to create the public/private keys, the keys would have to be transferred from the original computer to the new computer.
If the above does not help, then a new public/private key pair needs to be created and sent to us.
KB3842 - Using GPG/RSA encryption keys to guarantee the privacy and security of your Reports
KB3968 - Generate a key pair using GPG for Windows
KB4205 - Generate a key pair using GPG Suite on macOS
KB4108 - Decrypt your Reports using GPG for Windows
KB4407 - Generate RSA Key Pair on Windows
Decrypt Your Reports Using GPG for Windows
Note: This tutorial assumes you received reports via email or via FTP that were encrypted with the public key you sent to IBKR. If you need guidance to set up the encrypted statement delivery, please refer to this article, which is a prerequisite to the instructions below.
How to decrypt files using Kleopatra:
1. Save all the encrypted Reports you received via email or FTP in a folder on your preference (e.g. Desktop)
2. Start the Kleopatra application (included in Gpa4win software). The entry for your Key should be listed in the All Certificates panel. Click the top menu File and select Decrypt/Verify...
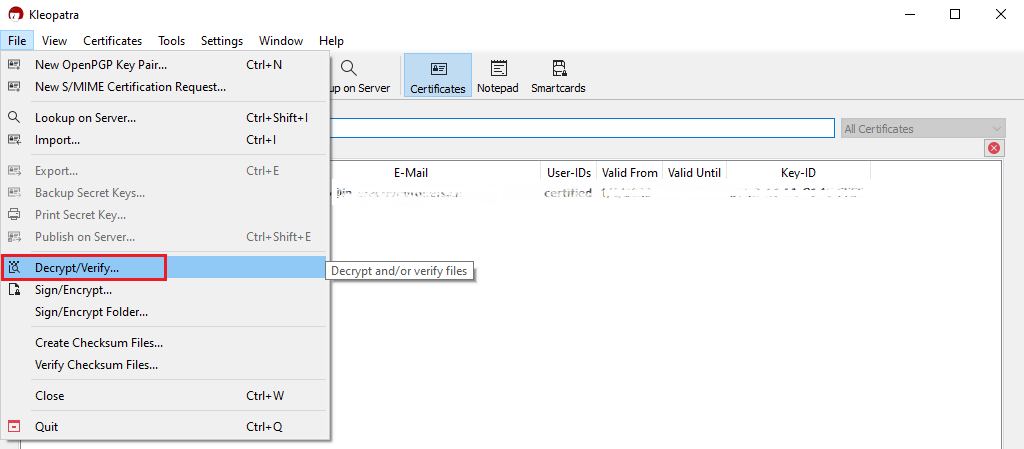
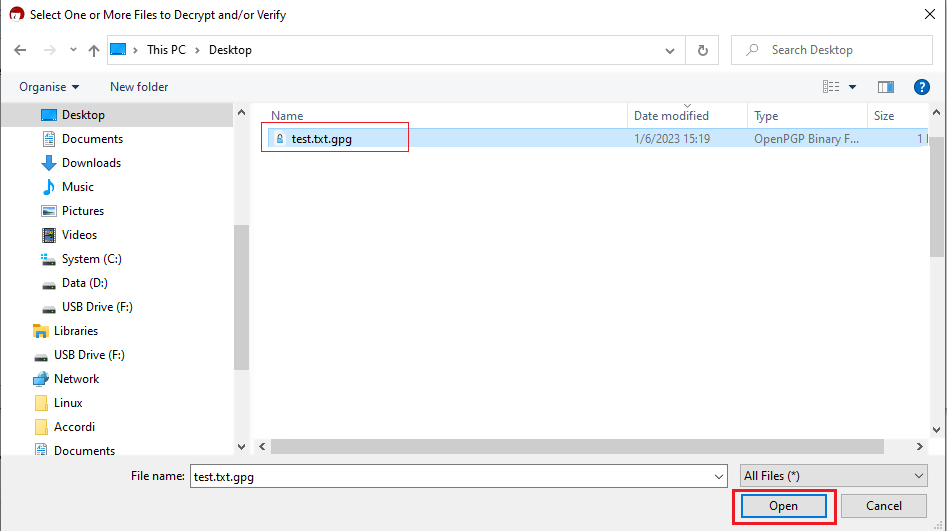
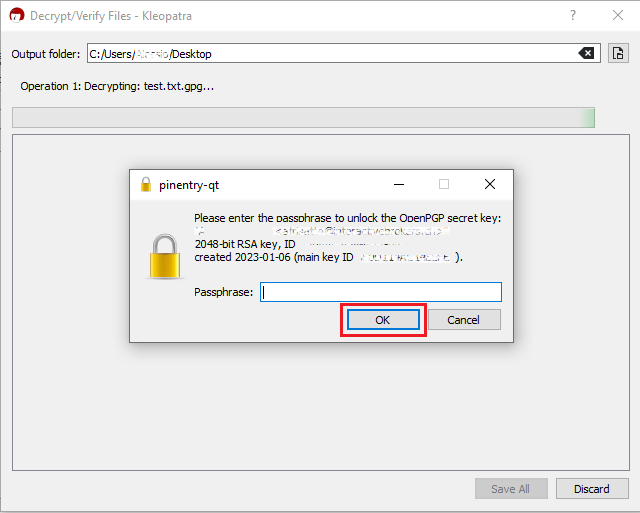
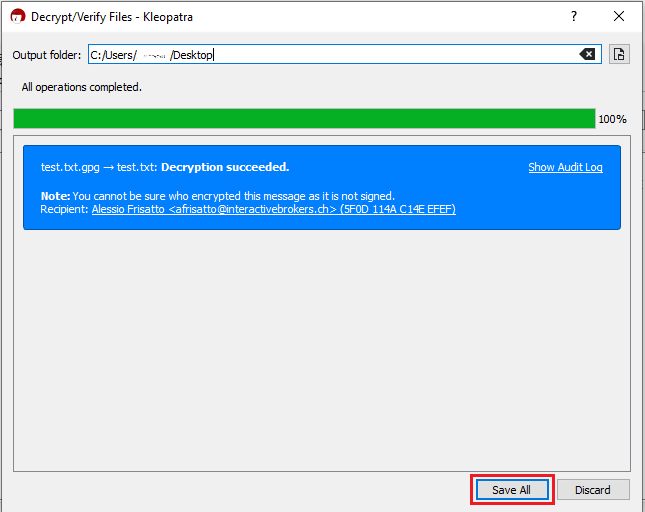

Common Issues/Questions
- Decryption failed with error 'No Secret Key'
This is usually caused by the wrong encryption key being used to decrypt the file. If decryption is being done on a computer other than the original computer used to create the public/private keys, the keys would have to be transferred from the original computer to the new computer.
If the above does not help, then a new public/private key pair needs to be created and sent to us.
KB3842 - Using GPG/RSA encryption keys to guarantee the privacy and security of your Reports
KB3968 - Generate a key pair using GPG for Windows
KB4205 - Generate a key pair using GPG Suite on macOS
KB4210 - Decrypting Reports using your PGP Key pair on macOS
KB4407 - Generate RSA Key Pair on Windows
KB4409 - How to set up sFTP for using Certificate Authentication on Windows
KB4410 - How to set up sFTP for using Certificate Authentication on macOS
KB4411 - How to backup your public/private Key pair
KB4323 - How to transfer your public/private key pair from one computer to another