Fees for Trading Warrants and Structured Products on Euronext
Euronext's fee thresholds on structured products and how it impacts clients' trading, for both fixed and tiered commission models
Clients that place orders and trade for more than EUR 6'000 in Warrants and Structured Products will be charged a 2.5 basis points fee with a maximum of EUR 20.
The table below displays the exchange fees for warrants and structured products when trading on Euronext:
|
Product Group |
Fee |
Minimum per Trade |
Maximum per Trade |
|
Warrants & Structured Products – trade value up to EUR 6’000 |
0.00 |
N/A |
N/A |
|
Warrants & Structured Products – trade value more than EUR 6’000 |
2.50 bps |
N/A |
EUR 20 per Trade |
Calculations:
For Cost Plus (Tiered) Clients:
Example: Client wishes to trade structured products on Euronext for a total trade value of EUR 10’000.
Scenario A:
Trade value = EUR 10’000
Fee = 2.5 Bps
As the trade value is above EUR 6’000, the fee of 2.50 bps applies and therefore an additional EUR 2.50 will have to be paid for the trade.
Scenario B:
Order 1:
Trade Value = EUR 5’000
Fee = 0.00
Order 2:
Trade Value = EUR 5’000
Fee = 0.00
As the trade value of each trade is below EUR 6’000, no additional fees apply.
Note: This calculation does not impact clients on the Fixed commission schedule.
L’éventualité de la réception d’alertes en cours d’installation ou de mise à jour de TWS
La plateforme Trader Workstation (TWS) d’IBKR est un dispositif de trading qui, à l’échelle mondiale, permet à sa clientèle d’employer une suite d’instruments de trading électronique. On peut installer TWS sur Windows, Mac OS X et Linux, mais son installation nécessite la présence de l'environnement d’exécution Java (JRE). Par conséquent, lors de l'installation de TWS, le téléchargement des fichiers Java nécessaires à l’exécution de l’usage de la machine virtuelle Java (JVM) s’effectue également.
Il arrive qu’en cours d’installation ou de mise à jour de TWS, un logiciel tel qu’un antivirus fasse apparaître une alerte, ce qui a pour effet de bloquer le processus. Dans ce cas, vous pouvez ignorer tout avertissement ou message de cette nature et terminer l’installation de la plateforme de trading en question.
Table des matières
Téléchargement du programme d’installation de TWS et des correctifs de mise à jour
Les programmes d’installation de TWS qui sont disponibles dans les zones de téléchargement sur ibkr.com et les sites Web régionaux d’IBKR sont scellés et numériquement signés suivant tous les procédés de sécurités qu’il faut obligatoirement employer dans ce domaine et ils ne contiennent aucun code ou programme malveillant. C’est tout en faisant preuve de la même rigueur que les correctifs de mise à jour de TWS sont conçus, lesquels se téléchargent et s’installent automatiquement lors de l’exécution de TWS (uniquement si, à ce moment-là, il y a une mise à jour de disponible). Toutefois, si vous recevez un message d’alerte, nous vous recommandons de faire preuve de prudence. Si vous avez l’intention de conserver le fichier du programme d’installation de TWS dans votre appareil pour vous en servir de nouveau plus tard, nous vous conseillons de veiller à y appliquer les mêmes précautions que dans le cas de la protection des données contre les virus informatiques et les logiciels malveillants.
Comment se fait-il que je reçoive un avertissement lors de l'installation de TWS ou de l’exécution d’une mise à jour automatique de TWS ?
Si jamais vous voyez une alerte (comme, entre autres possibilités, celle de l’image 1) , le dispositif de sécurité de votre ordinateur attendra que vous donniez votre avis relativement à ce qu’il s’agit de faire de ce fichier suspect. En général, dans ces cas-là, on a la possibilité de mettre ce fichier en quarantaine, de le supprimer, de l'ignorer pour l’instant ou d’en faire une exception à titre permanent.
Veuillez noter qu’il se peut que sans vous en demander la moindre confirmation, votre antivirus mette en quarantaine ou supprime le fichier du programme d’installation de TWS ou certaines de ses composantes. Or, cela ne se produira que si, au préalable, vous avez réglé votre antivirus de façon à ce qu’il réagisse de la sorte.
Image 1
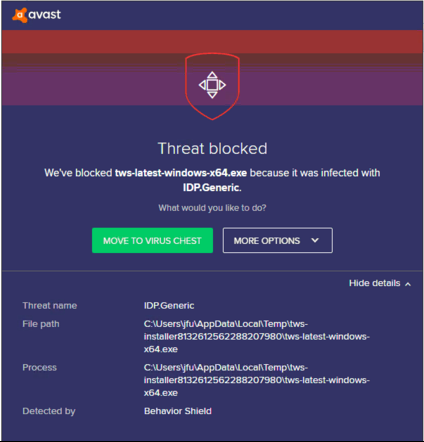
Si je reçois un avertissement, que dois-je faire ?
Si jamais, en cours d’installation ou de mise à jour de TWS, vous recevez un avertissement, voici ce que nous vous recommandons de faire :
1) Supprimer le programme d’installation de TWS et vous rendre sur le site Web principal d’IBKR ou l’un de ses sites Web régionaux pour télécharger de nouveau le programme en question
a) Supprimer le fichier du programme d’installation qui se trouve déjà dans votre ordinateur et, ensuite, le faire également disparaître de la corbeille (en la vidant)
b) Dans le tableau ci-dessous, pour télécharger de nouveau le programme d’installation de TWS, cliquer sur l’hyperlien correspondant à la région où vous vous trouvez dans le monde
| Région | Lien à ouvrir pour télécharger TWS |
| États-Unis | https://www.ibkr.com |
| Asie et Océanie | https://www.interactivebrokers.com.hk |
| Inde | https://www.interactivebrokers.co.in |
| Europe | https://www.interactivebrokers.co.uk https://www.interactivebrokers.eu |
c) Vérifier le certificat d’authentification du site Web → *La plupart des navigateurs Internet sont conçus pour vous avertir immédiatement s’il s’avère que le certificat d’authentification d’un certain site Web n’est pas valable, est piraté ou a expiré. Toutefois, si vous souhaitez vérifier vous-même le caractère valable du certificat en question, il s’agit de cliquer sur l’icône représentant un cadenas à côté de l’adresse Web (URL) pour vous assurer que la connexion est déclarée sécurisée et qu’aucun avertissement relativement à sa sécurité n’y figure (voir l’image 2 ci-dessous).
Image 2
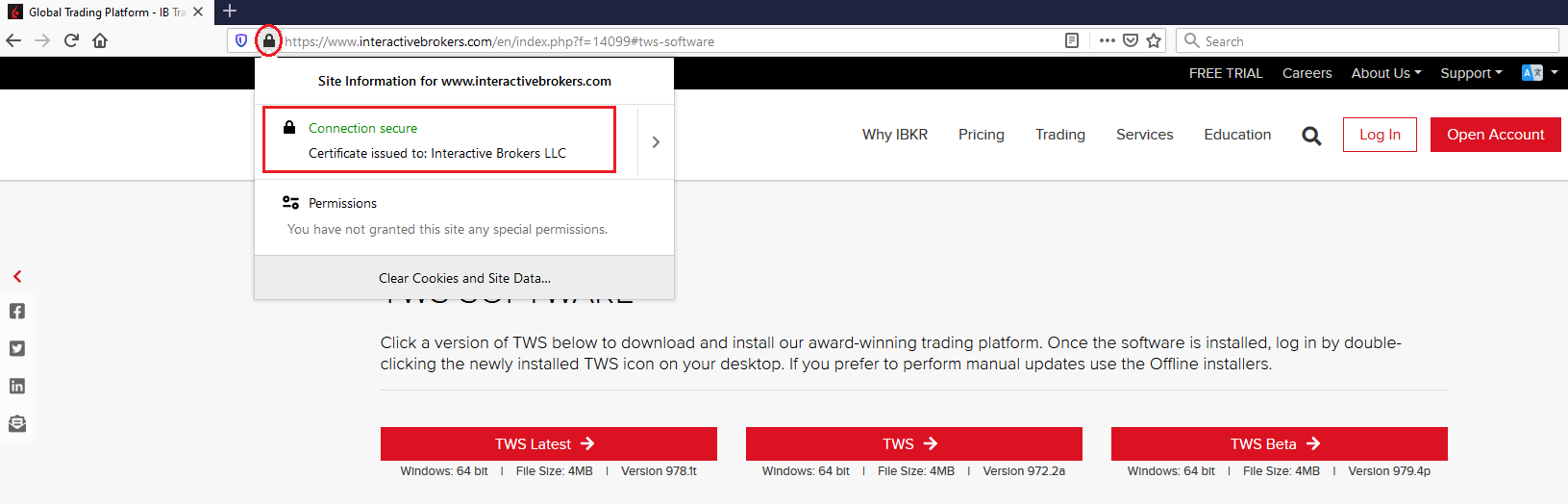
d) Cliquer sur le bouton marqué de la version de TWS dont vous désirez vous servir et télécharger son programme d’installation
2) Vérifier la signature numérique du fichier du programme d’installation de TWS que vous venez de télécharger
En principe, s’il s’avère que la signature numérique du fichier que vous cherchez à télécharger est piratée, vous devriez recevoir immédiatement un avertissement de sécurité. Toutefois, si vous souhaitez néanmoins effectuez vous-même cette vérification, prière, selon le système d’exploitation de votre ordinateur, de vous y prendre à cette fin comme suit :
Sur Windows
a) En passant par l’explorateur de fichiers Windows, entrer dans le dossier des téléchargements ou dans celui où vous avez enregistrer le programme d’installation de TWS
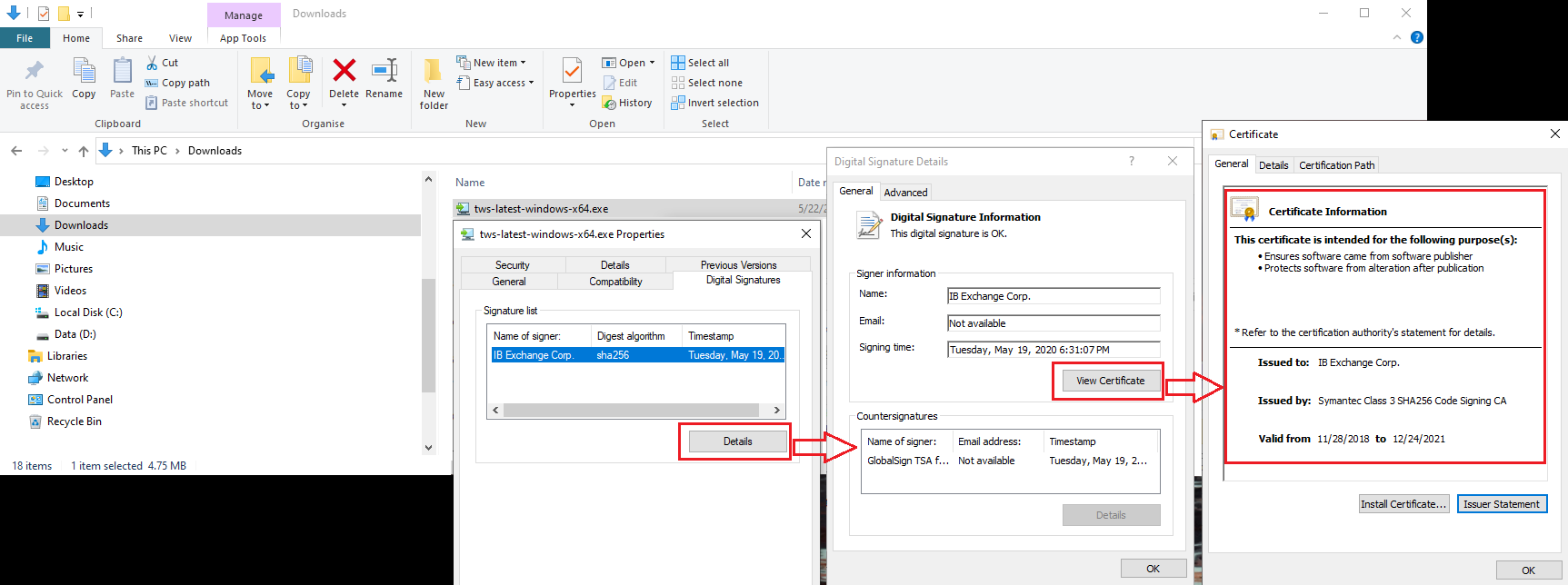
b) Faire un clic droit sur le fichier du programme d’installation de TWS, choisir Propriétés puis cliquer sur l’onglet Signatures numériques
c) Cliquer d’abord sur Détails et, ensuite, sur Voir le certificat pour vérifier la qualité du certificat d’authentification et l’identité de son signataire → *Dans le présent cas, le signataire légitime est IB Exchange Corp. (voir l’image 3 ci-dessous).
Image 3
Sur Mac OS X
a) Cliquer sur l’icône représentant une loupe (recherche), en haut à droite de l’écran de l’ordinateur, et taper Terminal → *En vous aidant des résultats de la recherche, exécuter l’appli Terminal.
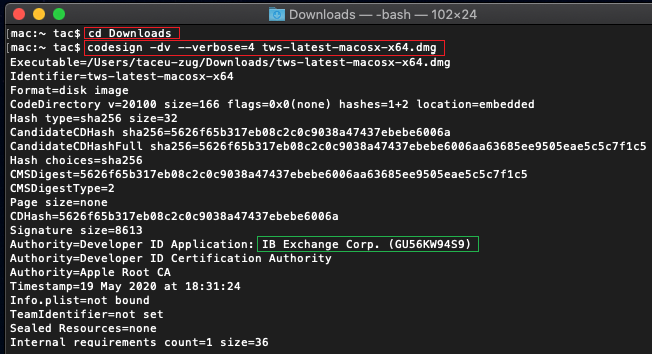
b) Saisir cd Downloads et appuyer sur Entrée
c) Saisir codesign -dv --verbose=4 tws-latest-macosx-x64.dmg et appuyer sur Entrée. Veuillez noter que le nom du fichier (tws-latest-macosx-x64.dmg) peut être différent différent car il dépend de la version de TWS que vous avez téléchargé. Donc, s’il le faut, veuillez remplacer alors le nom du fichier par le bon dans la commande.
d) Vérifier la sortie de commande et vous assurer qu’à titre d’application de l’identité du développeur, c’est bien le nom d’IB Exchange Corp. qui figure (voir l'image 4 ci-dessous)
Image 4
3) Exécuter le fichier du programme d’installation de TWS que vous venez de télécharger
Dès que vous aurez téléchargé une seconde fois le programme d’installation de TWS, il faudra d’abord vous assurer que c’est bien d’une version authentique du fichier que vous disposez désormais (voir les points 1 et 2 ci-dessus), vous pourrez ensuite effectuer cette installation. Si jamais votre antivirus vous envoie un avertissement, vous pourrez le considérer comme un faux positif et l'ignorer. Si vous avez besoin de plus d'informations sur cette étape, veuillez passer directement à la prochaine section.
Comment dois-je m’y prendre pour informer le système qu’une certaine alerte est un faux positif ?
Tous les dispositifs de sécurité modernes permettent de faire des exceptions, ce qui permet de traiter les cas de faux positifs. Dans le présent contexte, toute exception est un programme qui empêche l’antivirus d’analyser un fichier ou procédé précis. Ainsi, le fichier ou procédé en question est jugé exempt de risque et ne peut plus donner lieu à la moindre alerte.
Suivant le logiciel de sécurité informatique employé, le procédé de création des exceptions peut varier. En effet, il se peut que vous ayez la possibilité de créer une exception à titre temporaire ou définitif en allant directement travailler à la fenêtre d’alerte ou, autrement, que vous deviez faire tout le travail vous-même en commençant par vous rendre à une section précise du panneau principal de configuration de l’ordinateur.
Si vous n'êtes pas sûr de la procédure, nous vous recommandons de consulter la documentation qui se rapporte à votre antivirus.
Dès que vous aurez ainsi établi une exception pour le fichier du programme d’installation de TWS ou pour le processus de mise à jour de cette plateforme de trading, il n’y aura plus là le moindre blocage et tout se passera normalement jusqu’au bout.
En cas de doute ou de fonctionnement anormal du système, que puis-je faire d’autre ?
Si vous avez des raisons de croire que votre appareil soit piraté ou infecté, nous vous recommandons de tout faire analyser dans l’ordinateur. Pour ce faire, il suffit généralement de cliquer sur l’icône de l’antivirus, qui se trouve dans la barre des tâches, en bas de l’écran (sur Windows) ou en haut de celui-ci (sur Mac OS), afin d’avoir la possibilité de faire exécuter une analyse générale du système de votre appareil. Vous pouvez également entreprendre cette tâche en passant par la fenêtre principale de l’antivirus. Si vous n'êtes pas sûr de la procédure, nous vous recommandons de consulter la documentation qui se rapporte à votre antivirus.
Contexte sur le plan technique
Par quels procédés le dispositif de sécurité de mon ordinateur analyse-t-il les fichiers que je télécharge depuis Internet ?
Les antivirus et les antimaliciels modernes sont conçus pour reconnaître les menaces éventuelles selon des signes d’ordres variés.
L’analyse se fondant sur la signature : le scanneur de l’antivirus recherche une disposition d’octets précise qui a déjà été catégorisée comme fichiers ou programmes malveillants ou, au moins, suspects. Il se peut également que l’antivirus effectue la vérification de la signature (qu’on appelle un algorithme de hachage ou un condensé numérique) en interrogeant une base de données où figurent les noms des menaces connues (c’est-à-dire des définitions de virus).
L’analyse de l’activité : l’antivirus détecte des éléments d’activité qui, individuellement, ne représentent pas une menace, mais qui, tous ensemble, présenteraient l’aspect habituel d’un maliciel (ex. : la capacité d’un certain code à se reproduire, à se cacher, à télécharger des fichiers supplémentaires qu’il trouve sur Internet, à communiquer avec un hébergeur externe ou bien à modifier le registre du système d’exploitation). Cette analyse a pour but de détecter des menaces éventuelles qui ne sont pas encore connues.
La détection heuristique : le scanneur décompile le code ou en effectue l’exécution dans un cadre virtuel et restreint. Puis, il en détermine la catégorie et analyse son activité en interrogeant un ensemble de règles précises se rapportant aux éléments d’activité des codes en général.
La protection assurée au moyen d’un cloud et l’apprentissage de la machine : il s’agit là de méthodes qui demeurent plutôt nouvelles. Le fichier à analyser est expédié sur le cloud de distribution de l’antivirus ou celui du dispositif de sécurité pour y subir une analyse en profondeur du code d’authentification et de l’activité effectuée par des algorithmes perfectionnés.
Ces procédés d’analyse sont-ils infaillibles ?
De nos jours, les menaces virales touchant les ordinateurs sont très complexes et, à l’instar de celles qui sont de nature biologique, elles sont capables de changer leur code et leur signature. D’ailleurs, de nouveaux maliciels et exploits ne cessent d’apparaître pour se répandre rapidement sur Internet. Les procédés d’identification des menaces dont il est fait mention ci-dessus ne sont donc pas infaillibles, mais ils permettent néanmoins la détection en étant employés ensemble.
Les procédés se fondant sur la signature des codes sont très efficaces quand il s’agit d’identifier les menaces connues et risquent relativement peu de donner des faux positifs ; or, ils ne sont guère capables de repérer ni les menaces inconnues ni celles qui ont déjà été identifiées, mais qui, ensuite, ont subi une mutation. Sur ce plan, les procédés de détection relevant de l’analyse de l’activité ou, selon le cas, de l’heuristique sont autrement efficaces que ceux des deux premières catégories, mais, leur tâche consistant à effectuer une interprétation des signes jusqu’à un certain point, ce qui, évidemment, ne donne pas une grande certitude, au lieu de reposer sur une simple comparaison des codes, ils présentent un risque accru de faux positif.
On emploie le terme faux positif quand un certain dispositif de sécurité catégorise un fichier ou procédé inoffensif comme maliciel.
Référence :
Exchange name change
Overview:
Interactive Brokers is completing an effort to update and consolidate exchange names where appropriate. When this effort is complete, the following updates will be in effect:
- GLOBEX and CMECRYPTO will be consolidated to a single exchange, ‘CME’
- ECBOT will be updated to ‘CBOT’
- COMEX listed metals (previously reflected as NYMEX) will be updated to exchange ‘COMEX’
- NYMEX, no change
Given the breadth of products involved, we are migrating in four waves based on underlying products:
| Key | Effective Trade Date | Products |
| Wave 1 | October 30, 2022 | GLOBEX: ZAR, LB, DA, IXE |
| Wave 2 | November 6, 2022 | GLOBEX: EMD, BRE, CHF, SOFR3, E7, NKD CMECRYPTO: BTCEURRR, ETHEURRR, MET |
| Wave 3 | November 13, 2022 | GLOBEX: All remaining products CMECRYPTO: All remaining products ECBOT: ZO, ZR, 2YY, 30Y NYMEX: ALI, QI, QC |
| Wave 4 | December 4, 2022 | ECBOT: All remaining products NYMEX: All remaining "Metal" products |
I am trading via API, how does this impact me?
For API clients the only requirement would be to provide a new exchange name, for example: exchange=”CME”, for existing contracts for the affected exchanges.
Old exchanges names will no longer be available after the change.
More details can be found within our FAQs through the following link: Upcoming Exchange name Changes
Note: If you are using a third party software connected to TWS or IB Gateway and that software does not recognize the new contract definitions, please contact the third party vendor directly.
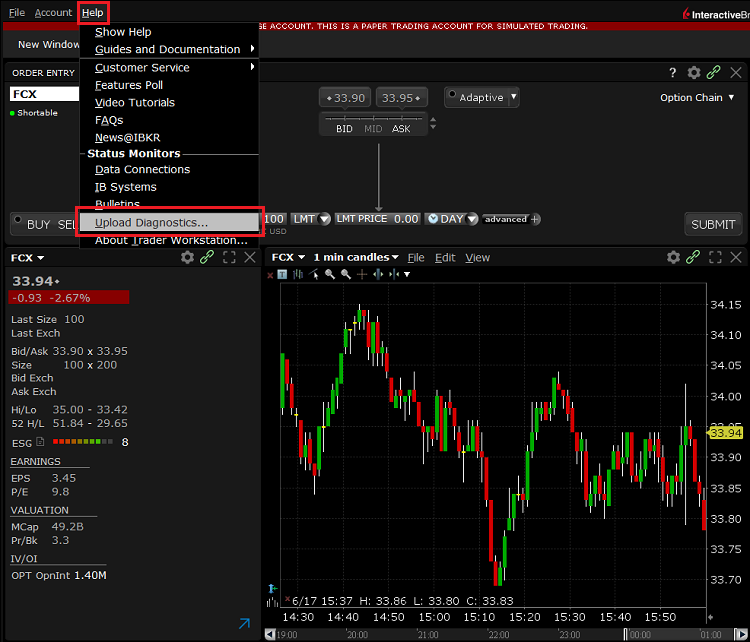
Comment télécharger des diagnostics depuis une plateforme IBKR
Certains problèmes liés au support nécessitent le téléchargement de fichiers de diagnostic et de journaux avec des captures d’écran. Les informations aideront nos équipes à étudier et à résoudre le problème rencontré.
Cet article vous fournira des étapes détaillées sur la façon de télécharger des fichiers de diagnostic et des journaux à partir des diverses plateformes de trading d’Interactive Brokers.
Remarque : IBKR ne surveille pas le référentiel de diagnostics pendant la journée. Si vous décidez de télécharger des diagnostics sans qu’Interactive Brokers ne vous le demande, veuillez en informer notre Service clientèle via un ticket dans le Centre messagerie ou par téléphone, sinon votre rapport d’erreur passera inaperçu.
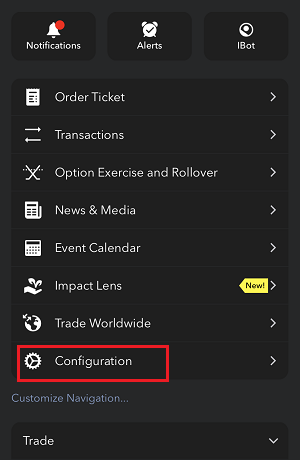
Veuillez cliquer sur un des liens ci-dessous, selon la plateforme que vous utilisez :
-
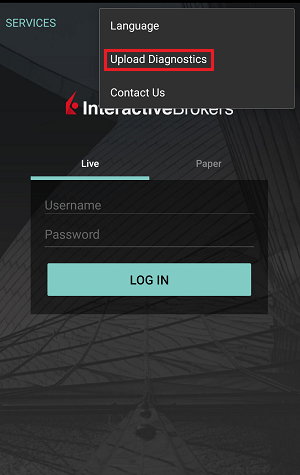
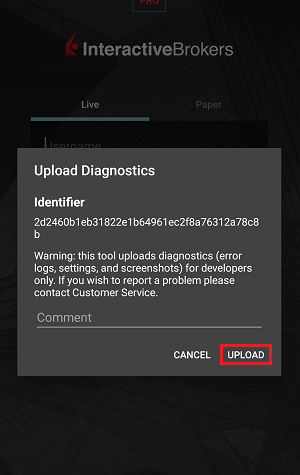
IBKR Mobile (Android)
-
IBKR Mobile (iOS)
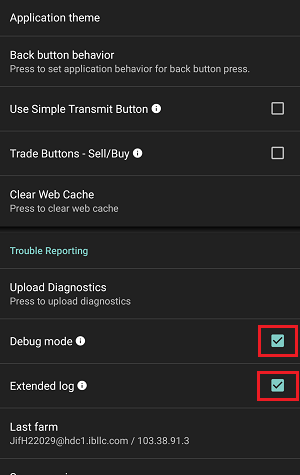
- Pour les systèmes d'exploitation Windows ou Linux : Appuyez sur Ctrl+Alt+Q
- Pour Mac : Appuyez sur Cmd+Option+H
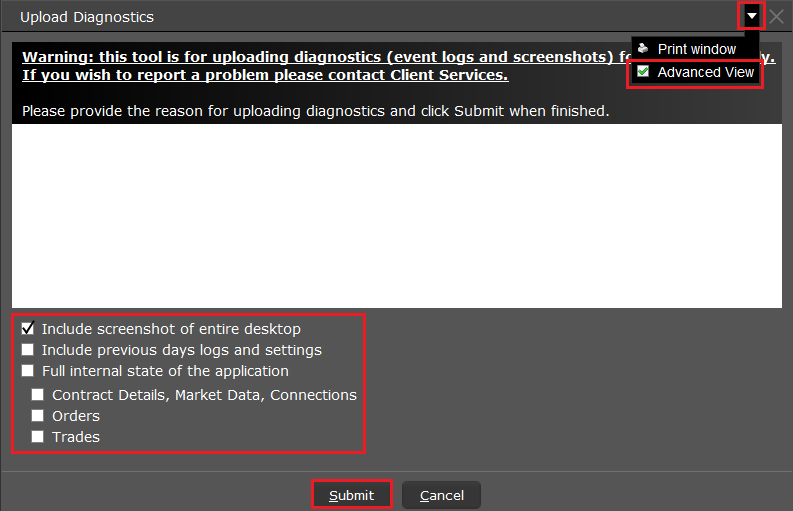
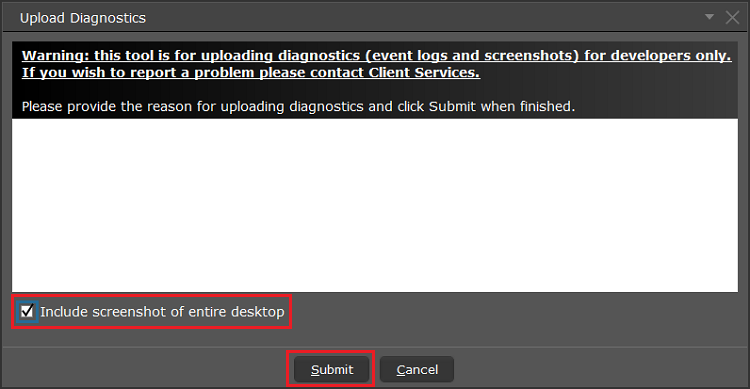
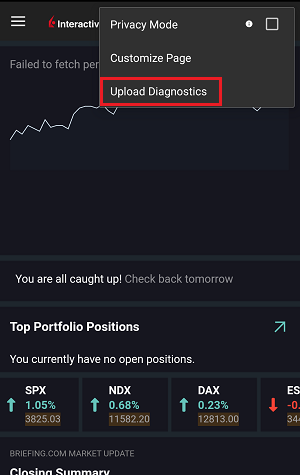
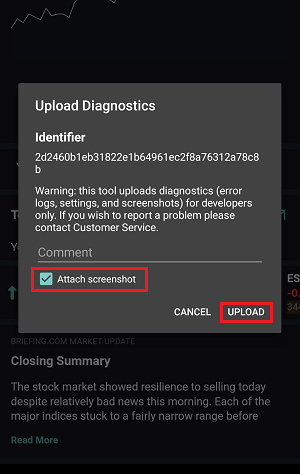

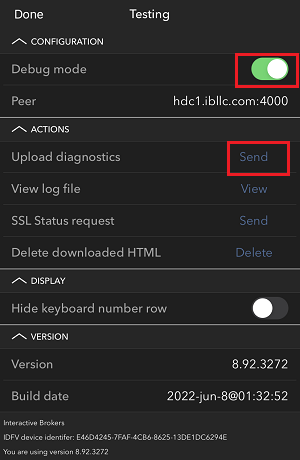
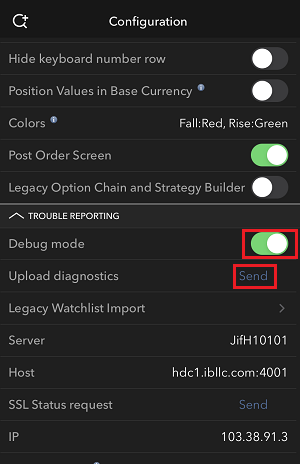
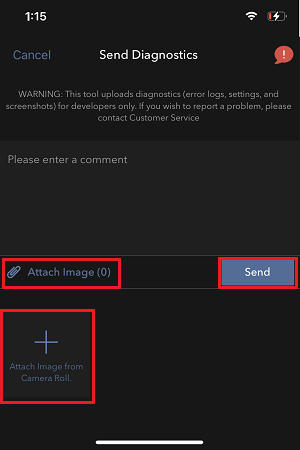
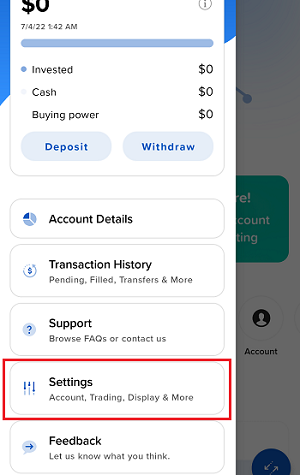
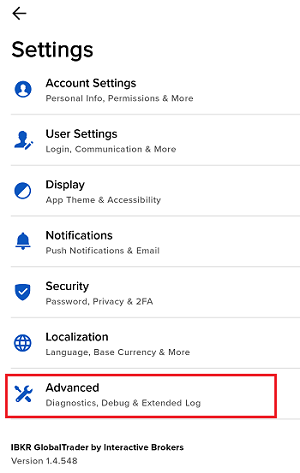
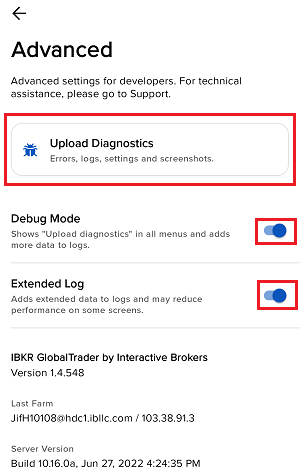
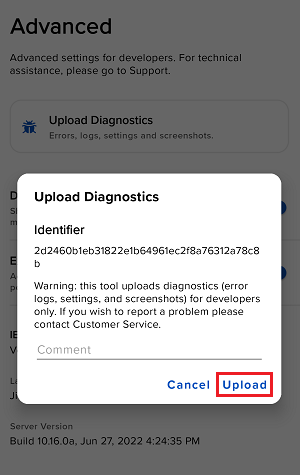
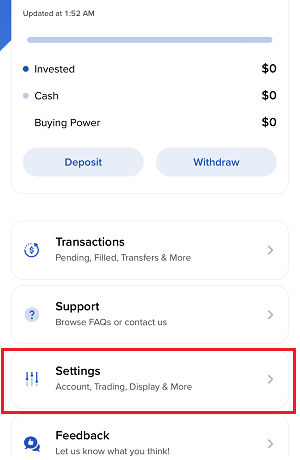
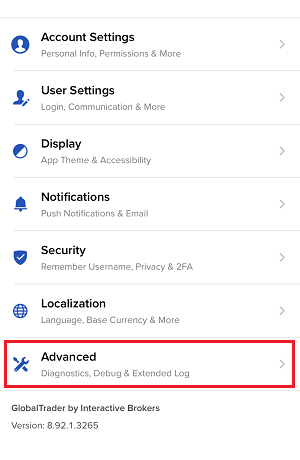
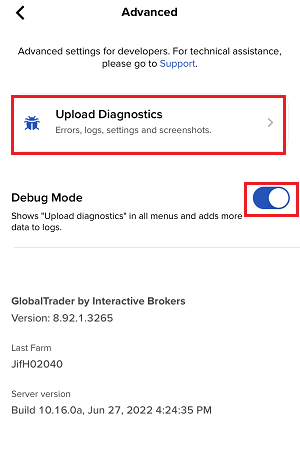
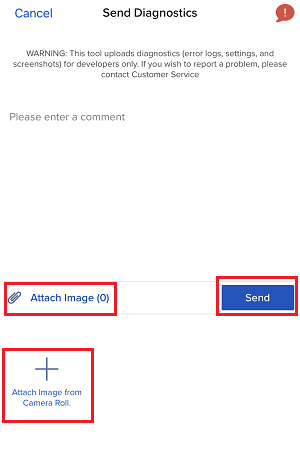
7. Saisissez vos commentaires dans le champ et appuyez sur « Joindre une image » pour joindre les captures d'écran que vous avez enregistrées dans votre galerie
Les détails des diagnostics pour le Portail Client sont expliqués dans l'article IBKB3512
Alternative Streaming Quotes for European Equities
Alternative Streaming Quotes for EU Equities
On August 1st, 2022, clients with non-professional or non-commercial market data subscriber status will receive complimentary real-time streaming Best Bid and Offer and last sale quotes on European Equities. These quotes will be aggregated from exchanges such as Cboe Europe, Gettex, Tradegate and Turquoise. The data will display in the SMART quote line and can be used to generate a chart as well.
Eligible users will see a no charge service called 'Alternative European Equities (L1)' added to their account on or before August 1, 2022. Please note this will be a default Market Data service that cannot be removed.
Users who would like to receive the full EBBO (European Best Bid and Offer) will need to subscribe to the individual exchange subscriptions.
La fenêtre de compte TWS pour les clients de détail d'IBCE et IBIE
Cet article décrit les informations fournies dans la fenêtre de compte de TWS pour les entités de l'Union européenne d'IBKR.
|
Les CFD sont des instruments complexes associés à un risque élevé de perte financière rapide en raison de l'effet de levier. 63,7 % des comptes d'investisseurs de détail perdent de l'argent lorsqu'ils tradent des CFD avec IBKR. Vous devez vous assurer que vous comprenez la manière dont fonctionnent les CFD et que vous pouvez vous permettre de courir un risque élevé de perte de capital. |
Les clients de détail résidents de l'EEE, qui détiennent un compte auprès d'un des courtiers européens d'IBKR, IBIE ou IBCE, sont soumis aux réglementations de l'Union européenne qui introduisent l'effet de levier et autres restrictions applicables aux transactions de CFD.
La réglementation exige l’utilisation de liquidités disponibles pour satisfaire aux exigences de marge CFD et interdit aux clients de détail d’utiliser des titres du compte comme garantie pour emprunter des fonds afin d’initier ou de maintenir une position CFD. Veuillez consulter l’Aperçu de la mise en œuvre des règles CFD de l’ESMA pour les clients de détail chez IBIE et IBCE pour plus de détails.
Les comptes des entités européennes d’IBKR sont des comptes universels dans lesquels les clients peuvent trader toutes les catégories d’actifs disponibles sur la plateforme IBKR, mais contrairement aux entités américaine et britannique d’IBKR, il n’y a pas de segments financés séparément.
Des exemples pratiques de la façon dont cette restriction est appliquée ainsi que des détails sur la façon dont les clients peuvent surveiller les liquidités disponibles pour les transactions CFD sont décrits ci-dessous.
Fenêtre de compte
IBKR applique la restriction relative aux liquidités disponibles en calculant les fonds disponibles pour le trading de CFD en temps réel, en rejetant les nouveaux ordres et en liquidant les positions existantes lorsque les liquidités disponibles sont insuffisantes pour couvrir les exigences de marge initiale et de maintien des CFD.
IBKR offre aux clients la possibilité de surveiller les liquidités disponibles pour les transactions de CFD via une amélioration de la fenêtre de compte TWS qui affiche le niveau de liquidités disponibles sur le compte. Il est important de noter que les fonds indiqués comme disponibles pour le trading de CFD n’impliquent pas que les liquidités soient détenues dans un segment distinct. Cela indique simplement la proportion du total des soldes de compte disponible pour le trading de CFD.
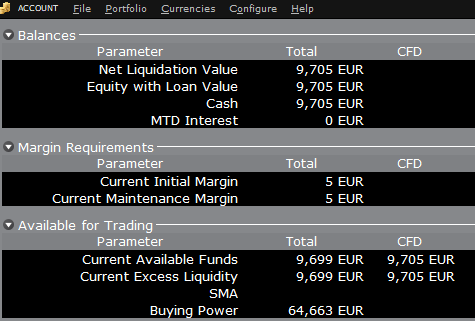
Par exemple, supposons qu'un compte ait 9 705 EUR de liquidités et pas de positions. La totalité des liquidités est disponible pour ouvrir des positions de CFD, ou des positions dans toute autre catégorie d'actifs :
Si le compte achète 10 actions d'AAPL pour une valeur totale de 1 383 USD, les espèces du compte seront
réduites par un montant correspondant en EUR, et les fonds disponibles pour le trading de CFD seront réduits du
même montant :
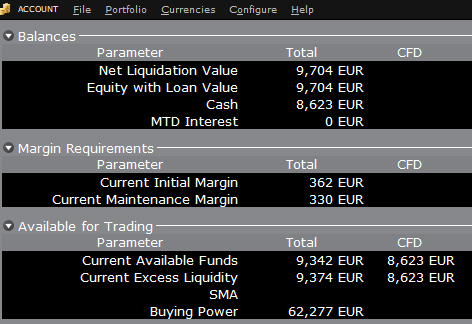
Veuillez noter que les fonds totaux disponibles sont réduits d’un montant inférieur, correspondant à l’exigence de marge d’action.
Si, au lieu d’acheter des actions AAPL, le compte achète 10 CFD AAPL, l’impact sera différent. Comme la transaction implique un contrat dérivé plutôt que l’achat de l’actif sous-jacent lui-même, il n’y a pas de réduction de trésorerie, mais les fonds disponibles pour les CFD sont réduits de l'exigence de marge CFD pour garantir la performance du contrat :
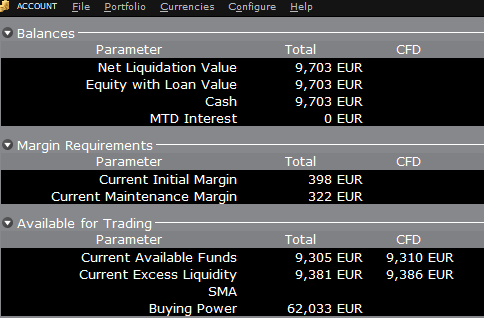
Dans ce cas, le total des fonds disponibles et les fonds disponibles pour CFD sont réduits d’un montant égal ; l’exigence de marge CFD.
Approvisionnement
Comme indiqué ci-dessus, les comptes basés au sein de l’UE n’ont pas de segments et il n’est donc pas nécessaire de procéder à des transferts internes. Les fonds sont disponibles pour les transactions dans toutes les catégories d’actifs dans les montants indiqués dans la fenêtre de compte, sans avoir besoin de sweeps ou de transferts.
Veuillez également noter que si un compte a un prêt sur marge, c’est-à-dire des liquidités négatives, il ne sera pas possible d’ouvrir des positions CFD car l’exigence de marge CFD doit être satisfaite par des liquidités disponibles et positives. Si vous avez un prêt sur marge et souhaitez trader des CFD, vous devez d’abord clôturer des positions de marge pour éliminer le prêt, ou ajouter des liquidités au compte d’un montant qui couvre le prêt sur marge et crée une réserve de liquidités suffisante pour la marge CFD nécessaire.
How to Upload a Diagnostic Bundle from an IBKR Platform
Some support related issues require diagnostics files and logs to be uploaded along with screenshots. The information will help our team to investigate and resolve the issue that you are experiencing.
This article will help you with detailed steps on how to upload diagnostics files and logs from various Interactive Brokers’ trading platforms.
Note: IBKR does not monitor the diagnostic bundle repository throughout the day. Should you spontaneously decide to upload a diagnostic bundle, without being instructed by Interactive Brokers, please inform our Client Services via Message Center ticket or phone call otherwise your error report will go unnoticed.
Please click on one of the links below, according to the platform you are using:
-
IBKR Mobile (Android)
-
IBKR Mobile (iOS)
- For Windows and Linux Operating system: Press Ctrl+Alt+Q
- For Mac: Press Cmd+Option+H






















7. Enter your comments in the field and tap ‘Attach Image’ to attach the screenshot/s you previously saved in your camera roll

A diagnostic trace for Client Portal can be captured following the steps on IBKB3512
Veuillez mettre à jour TraderWorkstation (TWS)
Le 9 décembre 2021, une défaillance de sécurité critique dans la bibliothèque logicielle Log4j d’Apache a été révélée (communément appelée « Log4Shell »). Log4j est très largement utilisée dans une grande variété de services grand public et d’entreprise, de sites, d’applications et d’appareils pour enregistrer des informations de sécurité et de performance. Cette défaillance pourrait permettre à un acteur distant non authentifié de prendre le contrôle d’un système affecté et d’y exécuter un code arbitraire. La nature omniprésente de Log4j et la facilité d’exploitation de la défaillance rendent cette menace non seulement critique mais aussi presque universelle.
QUE FAIT IBKR POUR PROTÉGER SES CLIENTS ?
Nous travaillons activement, en priorité, pour atténuer la menace sur plusieurs niveaux :
- Nous avons patché tous nos serveurs accessibles en externe (depuis Internet) avec une version de Log4j qui n’est pas sensible à cette défaillance.
- Nous avons mis à jour le logiciel Trader Workstation (TWS) et les installateurs TWS avec une version de Log4j qui n’est pas sensible à cette défaillance.
- Nous avons mis à jour notre infrastructure de sécurité (y compris les pare-feu réseau, les pare-feu applicatifs, les outils de détection d’intrusion, etc.) avec les dernières mesures de protection qui aident à détecter et à bloquer les cyberattaques qui tentent d’exploiter la défaillance de Log4j.
- Nous poursuivons nos efforts pour identifier et corriger complètement tout système interne impacté (inaccessible depuis Internet).
- Nous continuons de surveiller l’évolution des menaces du secteur et adoptons des mesures d’atténuation supplémentaires au besoin.
ACTION REQUISE
Nous nous engageons à fournir un environnement sécurisé pour vos actifs et vos activités de trading. À cette fin, nous demandons à nos clients de privilégier l’utilisation de la DERNIÈRE version de TWS, qui se mettra à jour automatiquement. Si vous disposez de la version STABLE ou de toute version HORS LIGNE, qui ne se met pas à jour automatiquement, veuillez vous assurer de prendre les mesures nécessaires pour maintenir TWS en conformité avec les derniers correctifs de sécurité.
Please Upgrade TraderWorkstation (TWS)
On December 9, 2021, a critical security vulnerability in Apache's Log4j software library was disclosed, (now commonly referred to as “Log4Shell”). Log4j is very broadly used in a wide variety of consumer and enterprise services, websites, applications, and devices to log security and performance information. The vulnerability allows an unauthenticated remote actor to take control of an affected system and execute arbitrary code on it. The ubiquitous nature of Log4j and the ease of exploitation of the vulnerability makes this threat not only critical but also nearly universal.
WHAT IS IBKR DOING TO PROTECT ITS CLIENTS?
We are actively working, with high priority, to mitigate the threat on several levels:
- We have patched all our servers accessible externally (from the Internet) with a version of Log4j that is not susceptible to this vulnerability.
- We have upgraded our Trader Workstation (TWS) software and our TWS installers with a version of Log4j that is not susceptible to this vulnerability.
- We have updated our security infrastructure (including network firewalls, application firewalls, intrusion detection tools, etc.) with the latest protection measures that help detect and block cyber-attacks that attempt to exploit the Log4j vulnerability.
- We continue our ongoing efforts to fully identify and patch any impacted internal systems (those that are not accessible from the Internet).
- We continue monitoring the evolving industry threats and adopt additional mitigation measures as needed.
ACTION REQUIRED
We are committed to providing a secure environment for your assets and trading activities. To that end, we request that our clients give priority to the use of the LATEST TWS version, which will auto-update. Should you have the STABLE or any OFFLINE version, which does not auto-update, please ensure that you take the necessary steps to keep your TWS in line with the latest security fixes.
Interaction entre TWS et MacOS 12 (Monterey)
Le présent article traite des problèmes de performance de Trader Workstation (TWS) sous MacOS Monterey (version: 12), rencontrés par plusieurs clients. TWS peut subir des interruptions ou s'arrêter inopinément (crash) en fonctionnant sous MacOS 12. Cette erreur peut survenir immédiatement au démarrage de TWS ou plus tard, après quelques minutes/heures.
Mise en place de la correction
Une correction a été publié dans TWS Bêta, disponible au téléchargement ici
Ce processus comprenait de nombreux tests, pour voir quelle plateforme Java est la meilleure option pour Trader Workstation et pour éviter d'introduire de nouveaux problèmes en essayant de résoudre celui-ci.
Nous vous remercions de votre patience.
