手机收不到IBKR的短信(SMS)
在客户端中验证了手机号之后,您应该马上就能收到IBKR向您手机发送的短信(SMS)。本文阐述了在无法收到短信的情况下您可以采取的解决方法。
1. 激活移动IBKR验证(IB Key)作为双因素验证设备
为免受无线/手机运营商相关问题影响、稳定接收所有IBKR消息,我们建议您在手机上激活移动IBKR验证(IB Key)。
我们的手机验证以移动IBKR程序自带的IB Key作为双因素安全设备,因此在登录IBKR账户时无需通过SMS获取验证码。
移动IBKR程序目前支持在Android和iOS手机上使用。下方为安装、激活和操作说明:
2. 重启手机:
关机然后再重新开机。通常这样就能收到短信。
请注意,某些情况下,如漫游出运营商服务的范围时(在国外),您可能无法收到所有消息。
3. 使用语音回呼
如果重启手机后还是没能收到登录验证码,请可以选择“语音”。然后您会接到自动的语音回呼,告知您登录验证码。有关如何使用语音回呼的详细说明,请参见IBKB 3396。
4. 检查看是否您的手机运营商阻断了来自IBKR的SMS
某些手机运营商误将IBKR的短信识别为垃圾短信或不良内容,会自动对其进行阻断。您可以联系相应地区的相应部门检查您的手机号码是否有短信过滤:
美国:
- 所有运营商:Federal Trade Commission Registry
- T-Mobile:消息阻断设置请参见T-Mobile网站或直接在T-Mobile应用程序中查看
印度:
中国:
- 直接致电运营商询问其是否在阻断IBKR的消息
参考文章:
如何使用语音回呼接收登录验证代码
如果启用了短信验证作为双因素验证方式,您可使用语音回呼来接收登录验证代码。本文详述了登录平台时使用语音回呼的具体步骤。
客户端
2. 从两个选项中选择"语音"然后等待回呼。
3. 选择语音后,您会在一分钟内接到回呼。请等待回呼,准备好记下回呼将提供给您的代码。
TWS

2. 从两个选项中选择"语音"然后点击确定,等待回呼。
3. 选择语音后,您会在一分钟内接到回呼。请等待回呼,准备好记下回呼将提供给您的代码。
注:TWS的语音回呼功能只适用于最新版和BETA版。
移动IBKR - iOS版
2. 从两个选项中选择"语音"然后等待回呼。
3. 选择语音后,您会在一分钟内接到回呼。请等待回呼,准备好记下回呼将提供给您的代码。
移动IBKR - 安卓版
2. 从两个选项中选择"语音"然后等待回呼。
3. 选择语音后,您会在一分钟内接到回呼。请等待回呼,准备好记下回呼将提供给您的代码。
参考:
How to generate a ".har" file
When troubleshooting a non-trivial website issue, it is sometimes necessary for our Client Services team to obtain additional information about your browser communication. You may be asked record and provide a .har file. This file contains additional information about the network requests that are sent and received by your browser. Your browser can generate such file by recording content, timeline and status of HTTP/HTTPS requests and responses while the issue occurs.
In this article we explain how to generate a .har file. Please click on the browser that you use in the list below:
To generate the HAR file for Google Chrome:
1. Open Google Chrome and go to the page where the issue is occurring.
2. Press CRTL +SHIFT + I on your keyboard. Alternatively, click on the Chrome menu icon (three vertical dots at the top-right of your browser window) and select More Tools > Developer Tools
3. The Developers Tools opens as a docked panel at the side or bottom of Chrome. Select the tab Network (Figure 1.)
Figure 1.
.png)
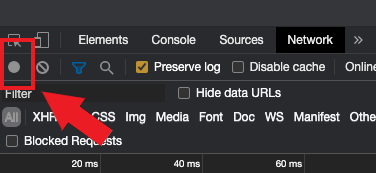
4. Look for a round Record button in the upper left corner of the Developer Tools toolbar and make sure it is red. If it is grey, click it once to start recording or just press CTRL+E (Figure 2.)
Figure 2.
5. Activate the checkbox Preserve log (Figure 3.)
Figure 3.
.png)
6. Click the Clear button to clear out any existing logs. The Clear button has a stop icon and is located on the right of the Record button (Figure 4.)
Figure 4.
7. Reproduce the issue you are experiencing while the network requests are being recorded.
8. Once you have reproduced the issue, right-click anywhere on the list of recorded network requests, select Save all as HAR with Content, and save the file to a location of your preference on your computer (e.g. on your Desktop).
9. From the IBKR Client Portal, go to the Message Center and create a new Web Ticket (or use an existing one when applicable)
10. Within the Web Ticket, attach the .har file previously generated. In case the IBKR Client Services has provided you with a reference ticker number or representative name, please add this information to the ticket body.
11. Submit the Web Ticket
To generate the HAR file for Firefox:
1. Open Firefox and go to the page where the issue is occurring
2. Press F12 on your keyboard. Alternatively click the Firefox menu icon (three horizontal parallel lines at the top-right of your browser window), then select Web Developer > Network
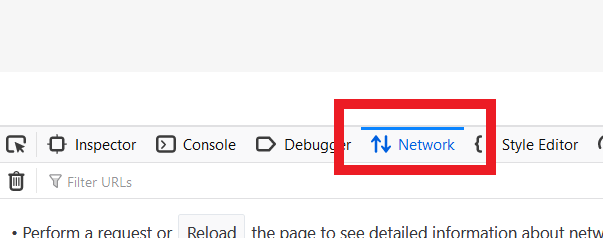
3. The Developers Network Tools opens as a docked panel at the side or bottom of Firefox. Select the tab Network (Figure 5.)
Figure 5.
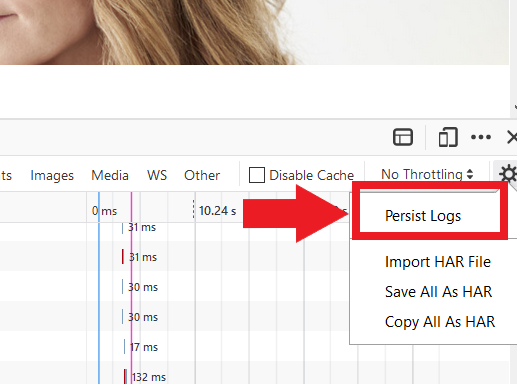
4. Activate the checkbox Persists logs (Figure 6.)
Figure 6.
5. Reproduce the issue you are experiencing. The recording of the network request starts automatically.
6. Once you have reproduced the issue, right-click anywhere on the list of recorded requests and select Save All As HAR
7. Save the file to a location of your preference on your computer (e.g. on your Desktop)
8. From the IBKR Client Portal, go to the Message Center and create a Web Ticket (or use an existing one when applicable)
9. Within the Web Ticket, attach the .har file previously generated. In case the IBKR Client Services has provided you with a reference ticker number or representative name, please add this information to the ticket body
10. Submit the Web Ticket
To generate the HAR file for Microsoft Edge:
1. Open Edge and go to the page where the issue is occurring.
2. Press F12 on your keyboard. Alternatively click the Edge menu icon (three horizontal dots at the top-right of your browser window), then select More Tools > Developers Tools
3. Click the Network tab (Figure 10.)
Figure 10.
.png)
4. Reproduce the issue that you were experiencing before, while the network requests are being recorded.
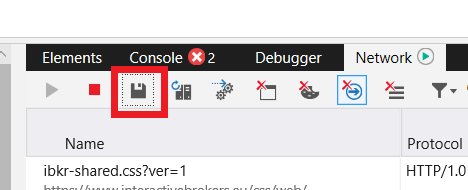
5. Once done click the floppy disk icon (Export as HAR) or press CTRL+S (Figure 11.)
Figure 11.
6. Provide a filename and a location of your preference on your computer (e.g. on the Desktop). Then click the Save button
7. From the IBKR Client Portal, go to the "Message Center" and create a Web Ticket (or use an existing one when applicable)
8. Within the Web Ticket, attach the .har file previously generated. In case the IBKR Client Services has provided you with a reference ticker number or representative name, please add this information to the ticket body.
9. Submit the Web Ticket
To generate the HAR file for Safari:
Note: Before generating the HAR file, make sure you can see the Develop menu in Safari. If you do not see this menu, click on the menu Safari, choose Preferences, go to the tab Advanced and activate the checkbox next to Show Develop menu in menu bar
1. Open the Develop menu and select Show Web Inspector or press CMD+ALT+I
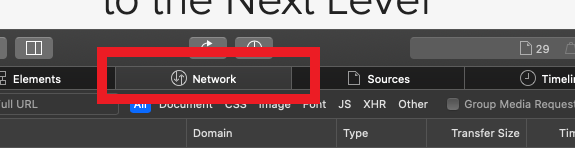
2. Click the Network tab (Figure 12.)
Figure 12.
3. Activate the checkbox Preserve log (Figure 13.)
Figure 13.
.png)
4. Click on the icon Export (or press CMD+S), provide a filename and a location of your preference on your computer (e.g. on the Desktop) and save the .har file
5. From the IBKR Client Portal, go to the "Message Center" and create a Web Ticket (or use an existing one when applicable)
6. Within the Web Ticket, attach the web archive file previously generated. In case the IBKR Client Services has provided you with a reference ticker number or representative name, please add this information to the ticket body.
7. Submit the Web Ticket
How to use Voice callback for receiving login authentication codes
If you have SMS enabled as two-factor authentication method, you may use Voice callback to receive your login authentication codes. This article will provide you steps on how to select voice callback when logging in to our platforms.
Client Portal
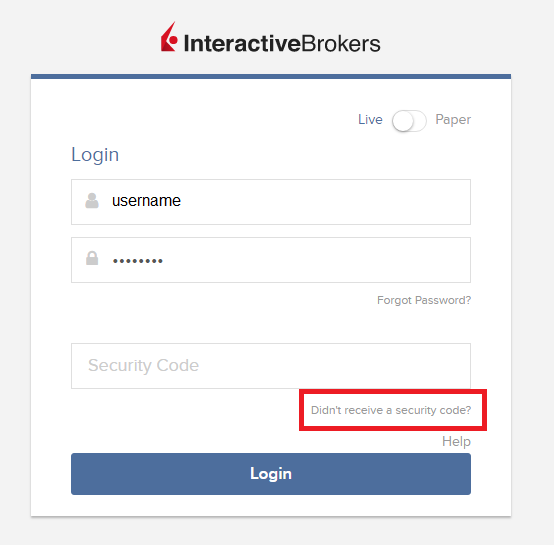
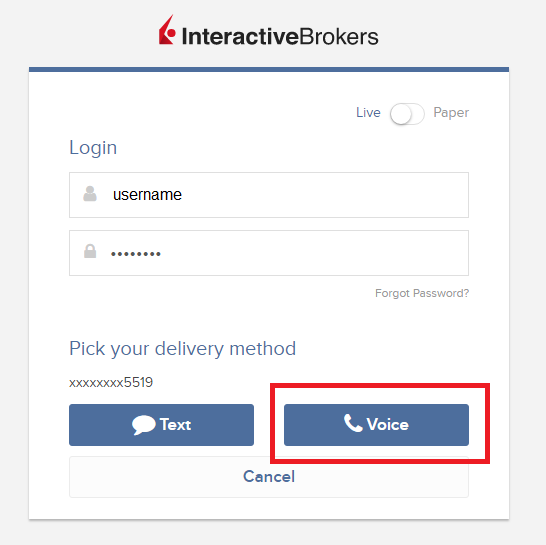
1. Click on "Didn't receive a security code?"

2. From the two options, select "Voice" and wait for the callback.

3. After selecting Voice, you should receive the callback within a minute. Please wait for the callback and be ready to write down the code that will be provided over the callback.
TWS
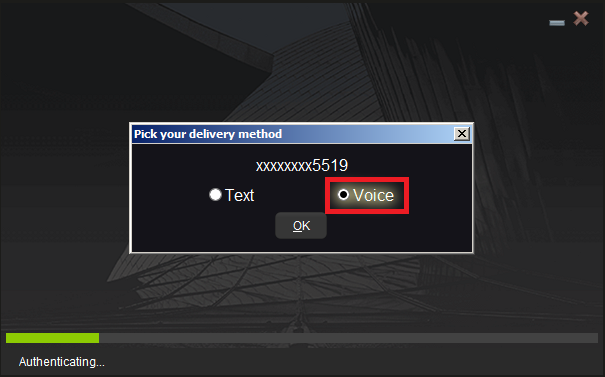
1. Click on "Request new Security Code"

2. From the two options, select "Voice" and click on OK. Then wait for the callback.

3. After selecting Voice, you should receive the callback within a minute. Please wait for the callback and be ready to write down the code that will be provided over the callback.
Note: Voice callback for the TWS is only available in the LATEST and BETA version.
IBKR Mobile - iOS
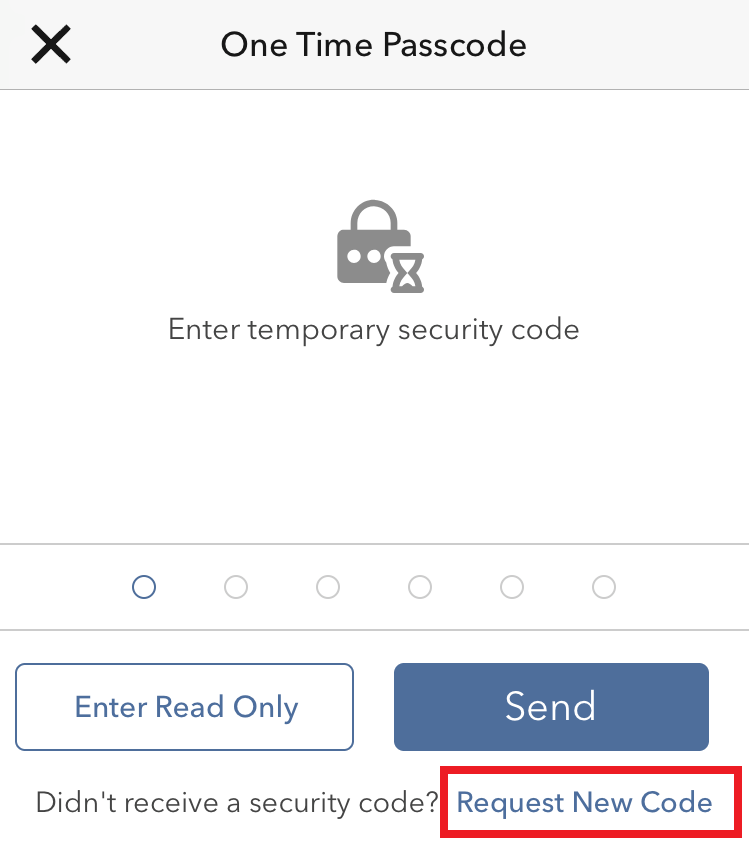
1. Click on "Request New Code"

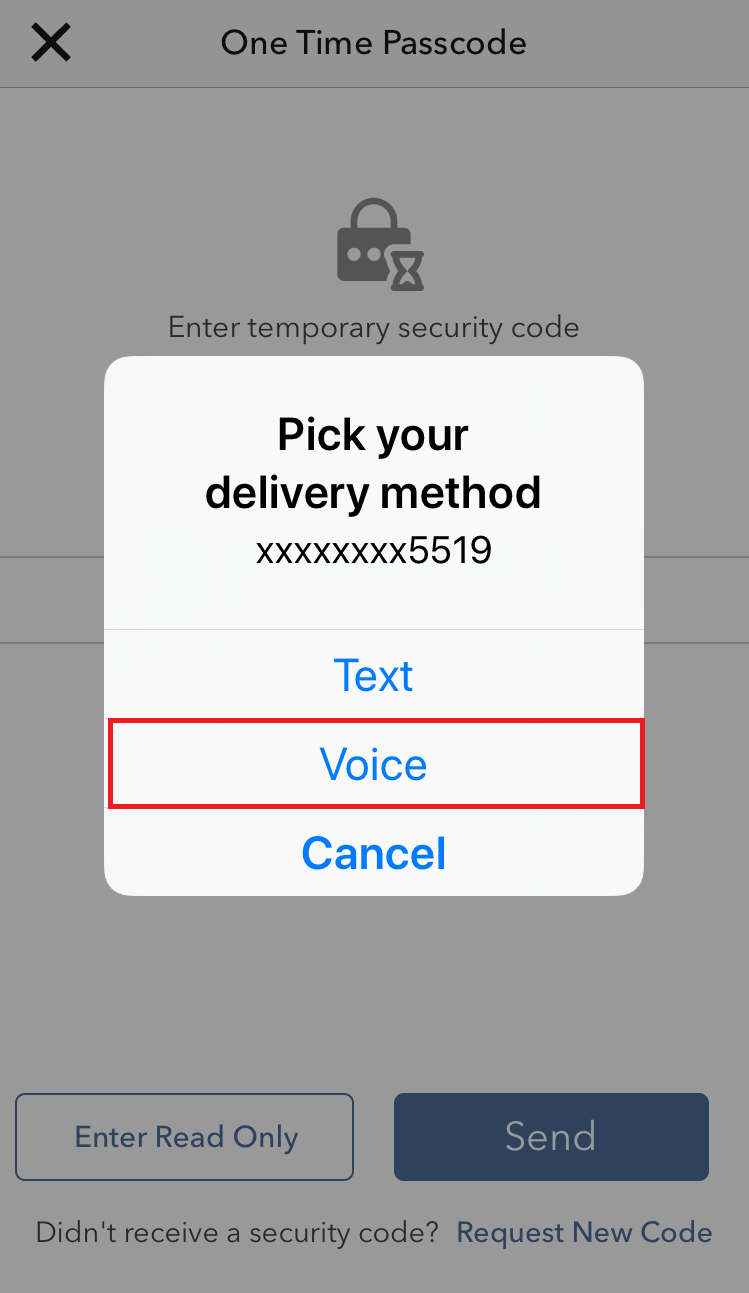
2. From the two options, select "Voice" and wait for the callback.

3. After selecting Voice, you should receive the callback within a minute. Please wait for the callback and be ready to write down the code that will be provided over the callback.
IBKR Mobile - Android
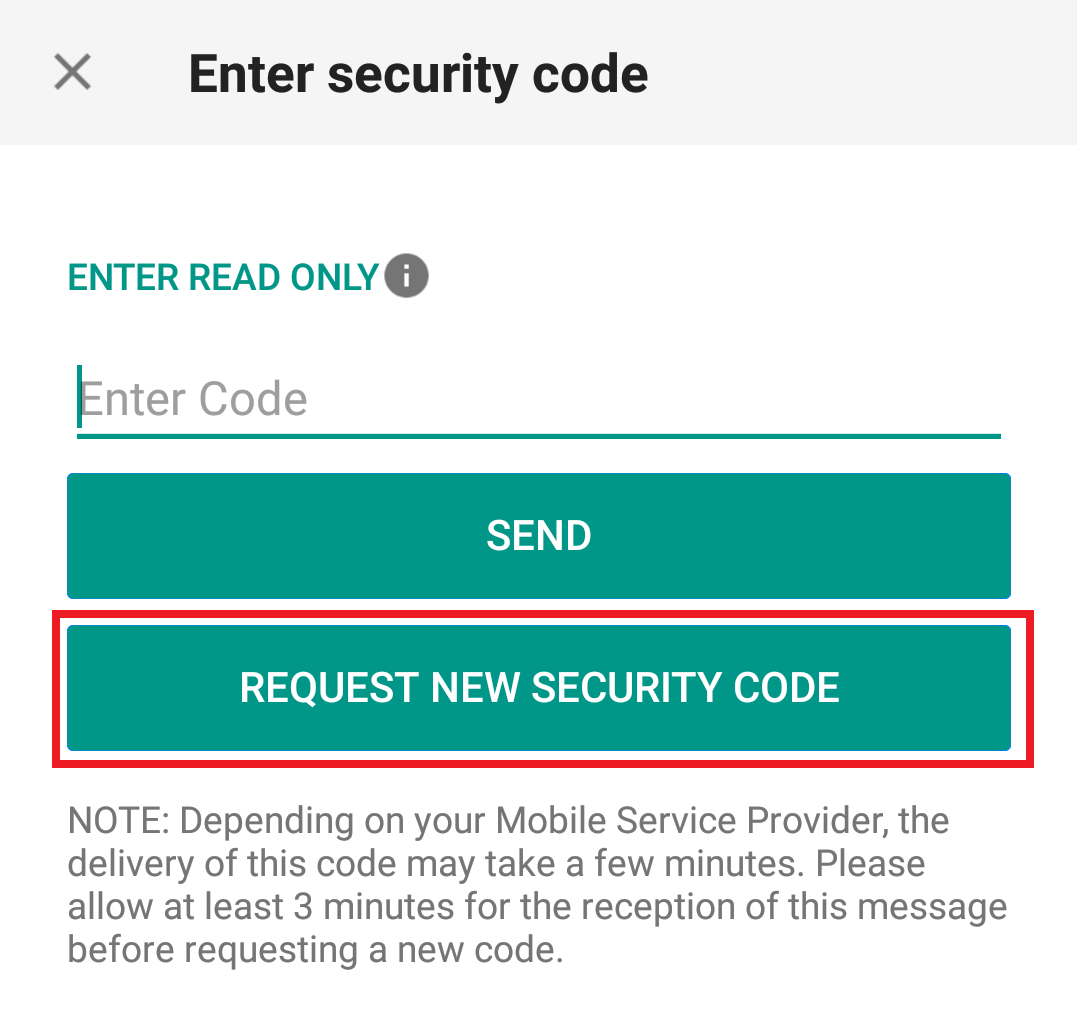
1. Click on "Request New Security Code"

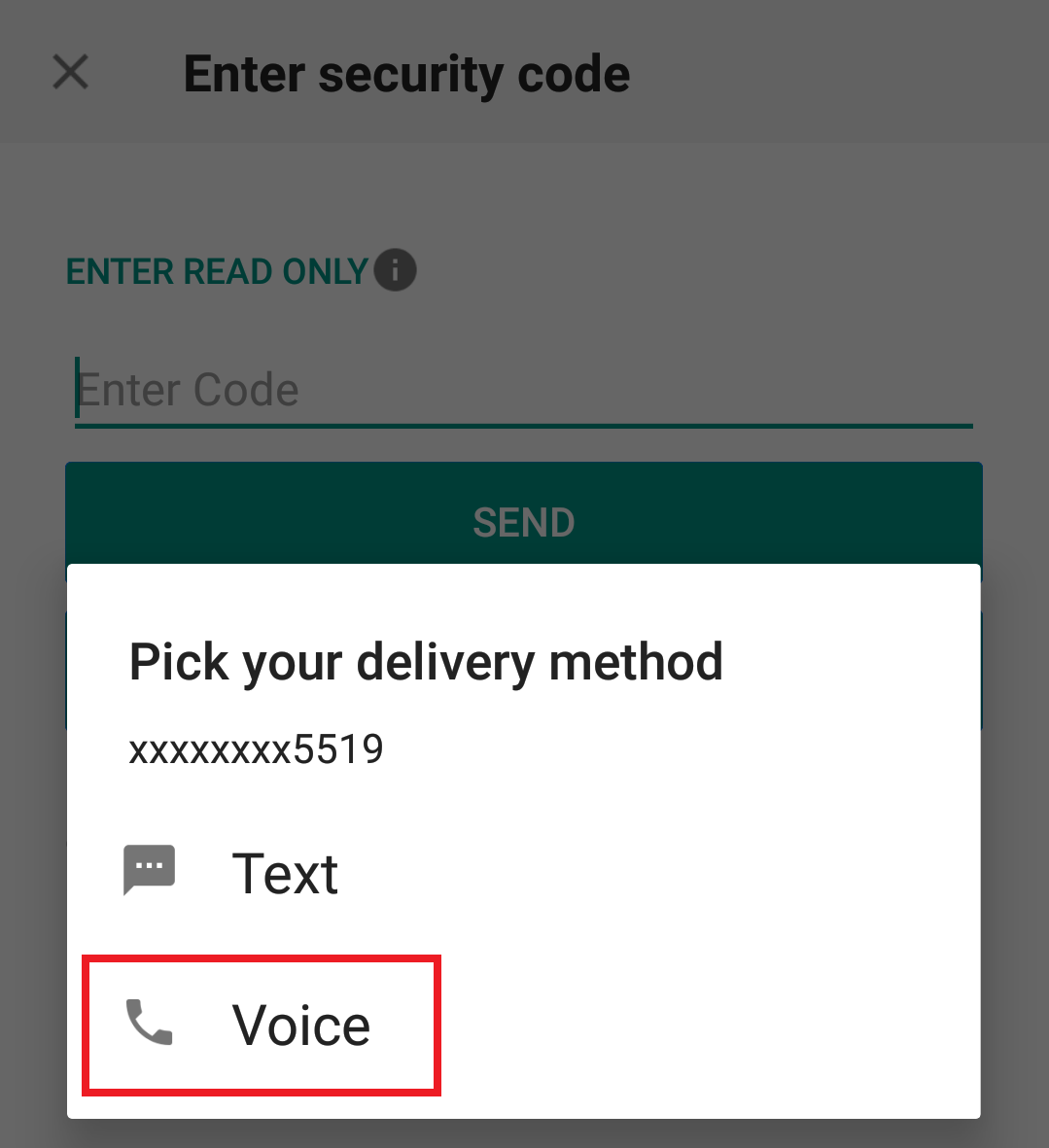
2. From the two options, select "Voice" and wait for the callback.

3. After selecting Voice, you should receive the callback within a minute. Please wait for the callback and be ready to write down the code that will be provided over the callback.
References:
- How to login using SMS authentication
- Overview of Secure Login System
- Information and procedures related to Security Devices
- IBKR Mobile Authentication
IBKR Mobile Authentication (IB Key) Use Without Notifications
In case your smartphone is unable to receive IBKR Mobile notifications, you can still complete the login process using the IBKR Mobile Authentication (IB Key) Challenge/Response method, described on the following pages (according to your device operating system):
The same information applies to you if your phone has no Internet connectivity (you are in roaming, out of coverage, without an active mobile data plan, etc.)
If your smartphone is unable to receive IBKR Mobile notifications despite having Internet connectivity, we recommend you to perform the steps outlined in the IBKR Knowledge Base.
TWS / IB Gateway and their interaction with Proxy servers
Table of contents
Configuration instructions
- Can the TWS / IB Gateway operate through a Proxy server, and how?
- If I use a SOCKS Proxy server, do I need to configure the TWS / IB Gateway?
- If I use a SOCKS Proxy server, do I need to configure the client machines where TWS / IB Gateway runs?
- If I use a Web (HTTP) Proxy server, do I need to configure the TWS / IB Gateway?
- What alternatives do I have in case I cannot implement a proxy solution on my network?
Common issues
Technical Background
Configuration instructions
1. Can the TWS / IB Gateway operate through a Proxy?
Upon start-up and during the run-time, the TWS / IB Gateway must establish and maintain direct network connections to our gateways and market data servers1. Such connections are created from random local TCP ports (above 1024) and are directed to TCP ports 4000 and TCP 4001. Since those are not HTTP connections, they cannot be serviced by a Web (HTTP) Proxy. They can only be serviced by a SOCKS Proxy.
From within the TWS interface, you can access several external services, such as IBKR Client Portal, Statements, Contract details, Bond Search, etc. Those services, being web-based, can be accessed through a Web (HTTP) Proxy (see section 6 for details and configuration) or through a SOCKS Proxy (see sections 4. and 5. for details and configuration).
2. If I use a SOCKS Proxy server, do I need to configure the TWS / IB Gateway?
The TWS / IB Gateway does not contemplate an option for SOCKS proxy forwarding. Therefore, it does not have a place where an explicit SOCKS Proxy host/port can be configured. This does not mean that the TWS / IB Gateway cannot work with a Proxy. It simply means that the TWS / IB Gateway is unaware of the underlying SOCKS proxy setup (proxy-agnostic).
Important Note: While it is impossible for us to determine whether a Proxy is enabled on your network, we assure you that all IBKR platforms, including the TWS, do not impact nor influence your network configuration.
3. If I use a SOCKS Proxy server, do I need to configure the client machines where TWS / IB Gateway runs?
The connections started by the TWS / IB Gateway can be redirected to a SOCKS (Application) Proxy through a specific client machine setup. We mention some of them below. Please note that the final decision is yours and none of the below suggestions can be recommended by us as best adapted to your setup and requirements.
3a. Using a Proxy Client software installed on the client machine where TWS / IB Gateway is running
With this setup, the Proxy client will intercept the connections (not only HTTP but for other ports as well) initiated by the TWS / IB Gateway and redirect them to a SOCKS proxy server. The typical benefits of a transparent proxy include a standard enterprise configuration where all clients routed to the Internet will always be filtered and protected no matter what the end users do, or change, on their machines and the added benefit of reduction in typical user’s client-proxy configuration troubleshooting.
3b. Using a so-called Proxifier
This configuration is very similar to the one at point 5a with the only difference that the Proxifier software can be set to redirect to a Proxy all the requests started by a specific process (e.g., C:\Jts\tws.exe; C:\JTS\ibgateway\XYZ\ibgateway.exe), hence instating a process level packet forwarding instead of a port level forwarding. This setup allows handling environments where different proxy servers are used for different applications or where you would like to address a specific application requirement without modifying/disrupting the connectivity schema for other software installed. The advantage of this solution is minimal maintenance since the connectivity schema is bound to the process and not to the hosts/ports.
3c. Using specific network routing on a client machine
With this setup, you can modify the client machine standard network routes, adding new ones in order to forward packets with specific destinations (e.g., Order routing and Market Data servers1) to a different gateway.
This gateway will then be in charge of routing those requests to the destination hosts. This solution has as well the benefit of not modifying/disrupting the connectivity schema for other software installed but usually requires more maintenance on the gateway and on the client machine in case the IP of the destination servers are changed or in case new servers are added.
4. If I use a Web (HTTP) Proxy server, do I need to configure the TWS / IB Gateway?
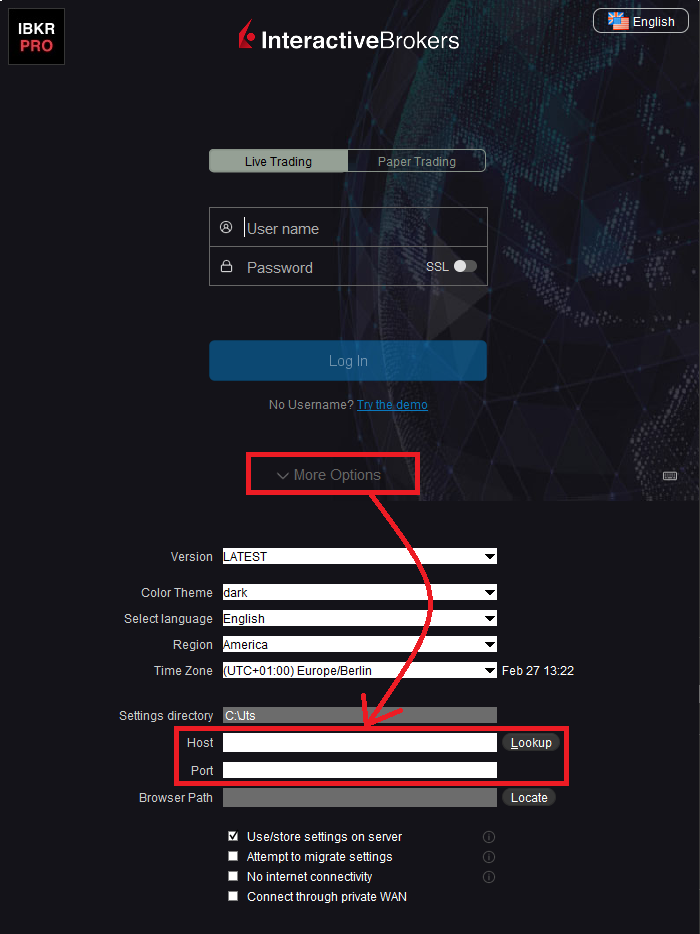
If the Workstations on your local network access the Web content through a Web (HTTP) Proxy, you need to specify the Web Proxy IP Address and port. To do this, click More Options at the bottom of the TWS Login Screen, and enter your Proxy server details in the fields Host and Port (see Figure 1 below). The same fields are present in the IB Gateway Login Screen.
Figure 1.
The Web Proxy you set there will ONLY be used to fetch the web content accessible from within the TWS (e.g., Client Portal, Statements, Product Details, etc.)
5. What alternatives do I have in case I cannot implement a proxy solution on my network?
In this case, you might orient yourself towards a different type of access to the IBKR infrastructure, which includes a special connection type and a FIX/CTCI engine setup. This setup would, on the other hand, have different requirements in terms of commissions2.
Common Issues
6. What happens if the proxy configuration on your computer is wrong or outdated?
Occasionally, third-party software, even if already uninstalled, may leave behind a SOCKS proxy configuration on your computer. This may also happen if your computer has been infected with malware. In such cases, the proxy server, although configured, is non-existent or not accessible on the network. In such scenarios, the TWS will show an error message (e.g., No Internet Connectivity) and/or start the "Connection attempt #" loop upon login. The same will happen if the Proxy server exists, but has not been correctly configured on the client machines.
6a. How can I correct the proxy configuration if wrong?
When applicable, we recommend you always consult the IT / Networking team of your company first and ask for guidance.
If you are autonomously managing your network, please follow the instructions below according to the Operating System of your machine/s:
Windows
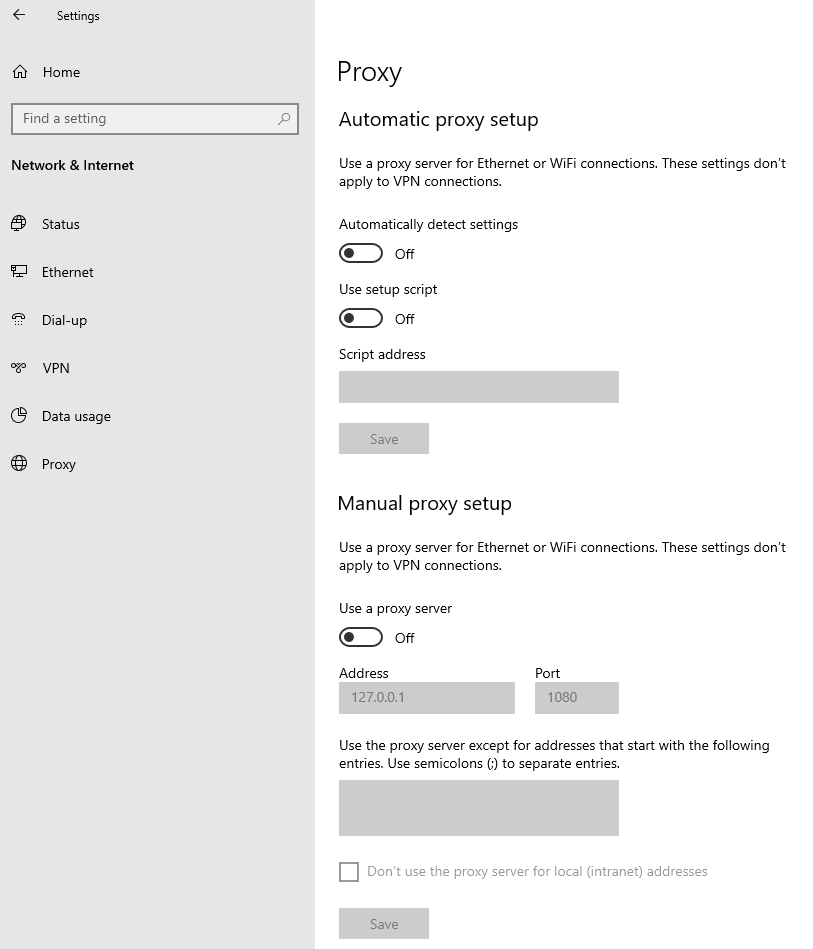
W.1 Press CTRL+S to open the Windows search
W.2 Type Proxy Settings and press Enter
W.3 If no Proxy is present on your network, make sure the switch "Use a proxy server" is deactivated (see Figure 2 below). If a Proxy server is active on your network, make sure the Address (or hostname) and Port are correctly defined.
Figure 2.
Mac
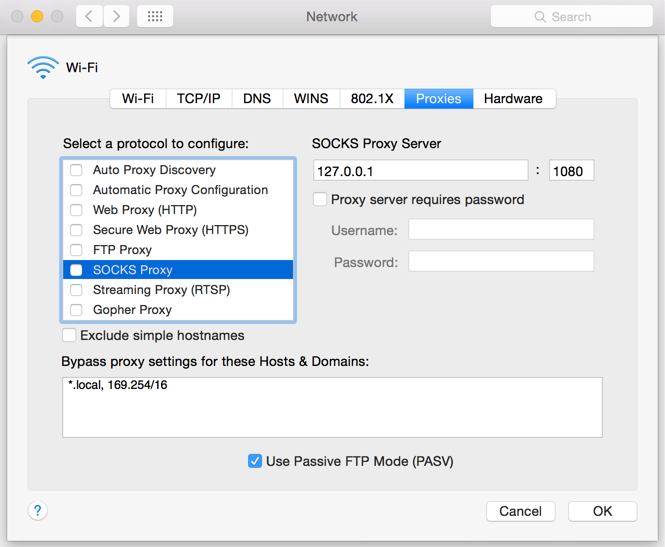
M.1 Click on the Apple icon at the top left corner of the screen and select System Preferences
M.2 Click on Network
M.3 Select the Network connection you are using to access the Internet (e.g. Wi-Fi) and click on it
M.4 Click on the Advanced button and then on the Proxies tab
5. If no proxy is present on your network, make sure all the checkboxes (SOCKS Proxy, Web Proxy, Secure Web Proxy) are deactivated (see Figure 3 below). If a Proxy is present on your network, ensure the Protocol, Address (or hostname) and Port are correct.
Figure 3.
7. You are using Public proxies and proxy chains to hide your presence or identity
There are public proxy and proxy chain services purposed to disguise or hide the identity and the activity of the subscriber or to bypass regional restrictions. One of the most famous services is the "Tor" network.
While those services may not necessarily be used for criminal purposes, they render subscriber traceability very difficult when not impossible. Since IBKR is obliged by the financial industry regulators to maintain records of trading activities and trade initiators, we do not allow our clients to reach our systems while using an anonymizing service. If you are using such a service, your TWS connection attempts will be automatically rejected by our gateways.
Technical Background
A proxy server usually acts as a gateway and as a barrier between your local network and the Internet. The proxy listens for outgoing connection requests from the internal workstation/s and forwards them to the desired target host or service on the Internet. When the target replies to such requests, the proxy routes the incoming responses back to the internal workstation/s that initiated the process.
Being the proxy, the only machine of your network actually accessing the Internet, it prevents the other machines and the internal segment of your network (LAN) from being accessible by external actors and hence from being exposed to threats and intrusion attempts.
Additionally, a proxy server can offer a variety of other services, such as web content caching and filtering.
9. Which types of Proxy servers are commonly used and where?
Proxy servers are commonly found within enterprise-grade networks. In the vast majority of cases, proxies are not used by individuals since private broadband connections are established through consumer-grade routers that already offer built-in proxy/firewall solutions. An exception is represented by public proxy or proxy chains discussed in detail in the section You are using Public proxies and proxy chains to hide your presence or identity
There are two main types of Proxy servers:
The HTTP (Hypertext Transfer Protocol) defines the rules and the standards for fetching Web content from a Web server and rendering such content on your Web Browser.
A Web Proxy handles only the routing of HTTP requests and HTTP responses. Those requests are transparently generated and sent by your browser whenever you access a Web page. Such requests are normally sent using specific ports (TCP 80 and TCP 443). Hence a Web Proxy usually listens for outgoing HTTP requests coming from your internal network (LAN) only on the TCP ports mentioned above.
SOCKS (Socket Secure) Proxies are designed to handle any type of traffic (not only HTTP/S traffic), generated by any protocol or program (including Trader Workstation).
Notes
1. More information about the servers accessed by the TWS is available in IBKB2816.
2. For an overview of the different special connection options and related requirements, please click here.
For an overview of the FIX infrastructure, please click here.
How to fix the "Cannot create ... file" error during TWS installation on MacOS
The filesystem permissions are controlled by your machines operating system. One of their functions is to secure your files, preventing unauthorized access or undesired modifications to the system and to your personal data.
Some software on your computer may modify or override the permissions assigned by the operating system. Under certain circumstances, this prevents the TWS installer from accessing the folder where the application core files have to be created (/users/youruser/home/Applications). In such cases, the TWS installation usually displays the error "Cannot create ... file. Shall I try again?"
Procedure:

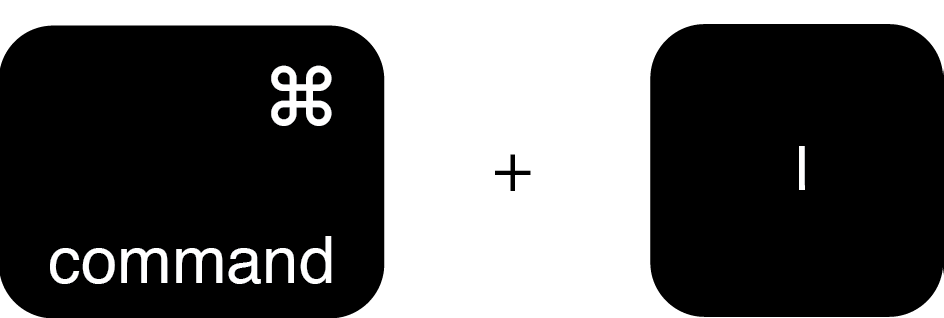
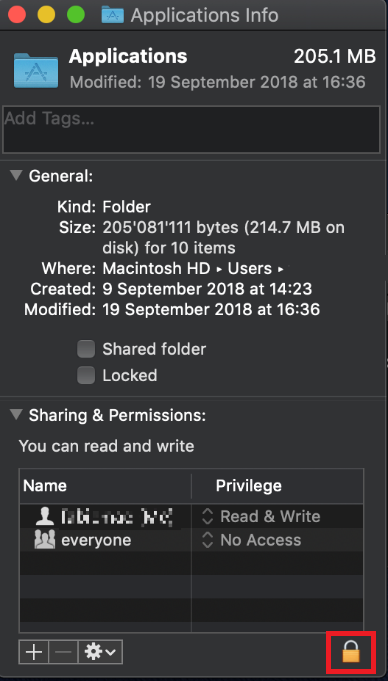
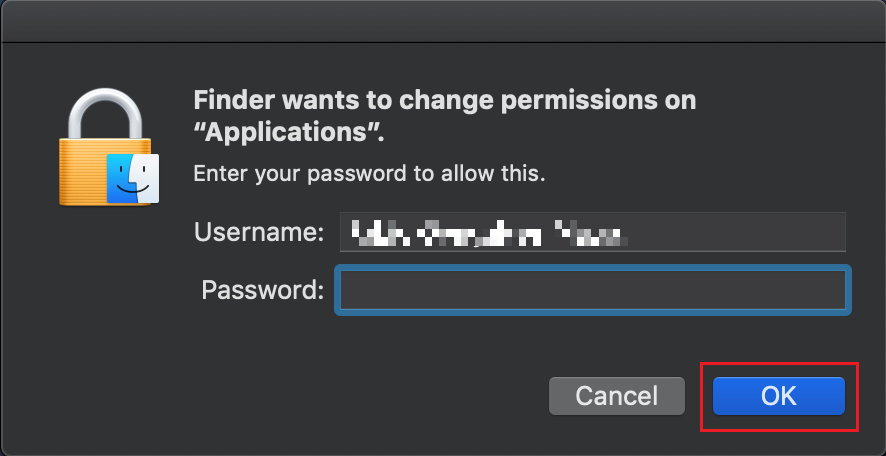
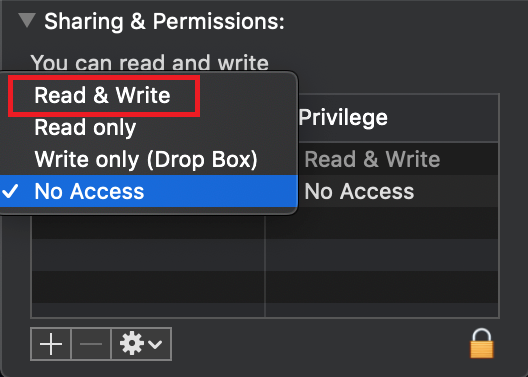
.png)
.png)
.png)
7. Once the installation has completed successfully, repeat the previous steps from 1. to 5. setting back the permissions of “everyone” to “Read Only” to revert your changes to the initial status
I am not receiving text messages (SMS) from IBKR on my mobile phone
Once your mobile phone number has been verified in the Client Portal, you should immediately be able to receive text messages (SMS) from IBKR directly to your mobile phone. This article will provide you with basic troubleshooting steps in case you are unable to receive such messages.
1. Activate the IBKR Mobile Authentication (IB Key) as 2-Factor security device
In order to be independent of wireless/phone carrier-related issues and have a steady delivery of all IBKR messages we recommend to activate the IBKR Mobile Authentication (IB Key) on your smartphone.
The smartphone authentication with IB Key provided by our IBKR Mobile app serves as a 2-Factor security device, thereby eliminating the need to receive authentication codes via SMS when logging in to your IBKR account.
Our IBKR Mobile app is currently supported on smartphones running either Android or iOS operating system. The installation, activation, and operating instructions can be found here:
2. Restart your phone:
Power your device down completely and turn it back on. Usually this should be sufficient for text messages to start coming through.
Please note that in some cases, such as roaming outside of your carrier's coverage (when abroad) you might not receive all messages.
3. Use Voice callback
If you do not receive your login authentication code after restarting your phone, you may select 'Voice' instead. You will then receive your login authentication code via an automated callback. Further instructions on how to use Voice callback can be found in IBKB 3396.
4. Check whether your phone carrier is blocking the SMS from IBKR
Some phone carriers automatically block IBKR text messages, as they are wrongly recognized as spam or undesirable content. According to your region, those are the services you can contact to check if a SMS filter is in place for your phone number:
In the US:
- All carriers: Federal Trade Commission Registry
- T-Mobile: Message Blocking settings are available on T-Mobile web site or directly on the T-Mobile app
In India:
- All carriers: Telecom Regulatory Authority of India
In China:
- Call your phone carrier directly to check whether they are blocking IBKR messages
References:
- How to login using SMS authentication
- Overview of Secure Login System
- Information and procedures related to Security Devices
- IBKR Mobile Authentication
IBKR主机与端口文档
如果使用SSL,TWS会通过4000和4001端口连接IBKR的服务器。如果您使用的是代理服务器,则其需同时开放入站端口和出站端口,使其成为透明代理,这样TWS才能正常运行。
下方表格列出了在您使用我方服务的过程中TWS可能会用到的所有网关及对应的目的主机,请允许访问该等主机。
要测试您的连接是否需要特殊设置或者是否已配置妥当,最简便的方法便是使用 IBKR的专用测试页面,其可针对您的网络与我方主交易与数据服务器的连接提供动态测试。如果返回的响应结果为“成功”,则您无需再进行进一步操作。如果响应结果为“失败”,我们建议您在网络配置中为新主机添加例外或检查您的更改。
注:如果您的网络使用的是浏览器代理,测试页面可能会产生错误正值。这种情况下,或者如果您不确定自己的网络设置情况,您可求助于您的网络管理员,网络管理员可对下表所列主机进行ping和telnet测试以确认符合连接要求。
说明:
|
客户端及网站 |
||||
|
地区/产品 |
服务器(主机) |
端口1 |
||
|
IBKR网站 – 美国 |
443 |
|||
|
IBKR网站 – 加拿大 |
443 |
|||
|
IBKR网站– 英国 |
443 |
|||
|
IBKR网站 – 印度2 |
443 |
|||
|
IBKR网站 – 日本2 |
443 |
|||
|
IBKR网站– 香港2 |
www.interactivebrokers.com.hk | 443 | ||
|
IBKR网站 – 中国2 |
www.ibkr.com.cn | 443 | ||
|
IBKR网站 - 澳大利亚 |
www.interactivebrokers.com.au | 443 | ||
|
客户端 – 东部 |
443 |
|||
|
客户端 – 中部 |
443 |
|||
1: 标准通信: TCP端口80| SSL通信: TCP端口443。
2: 本IB服务器主机不支持ping请求。
重要提示:如您通过企业网络访问客户端,且企业网络是通过负载平衡设备提供互联网连接的,则您在登录时或登录后可能会收到会话已过期/无效及/或网页内容丢失等错误信息。负载平衡器会将您的连出请求循环连至两个或以上网络界面以平衡网络负载。由于该机制,您的HTTP请求会通过不同的IP地址达到我们的系统,从而使您的客户端会话无效。在这种情况下,请联系您的网络管理员或IT部门配置您的设备以绕过负载平衡器。这样您的会话将继续有效。
|
桌面端TWS |
|||
|
地区/工具 |
主要/备用 |
服务器(主机) |
端口 |
|
|
主要 |
|
|
|
备用 |
|||
|
|
主要 |
|
|
|
备用 |
|||
|
|
主要 |
|
|
|
备用 |
|||
|
TWS亚洲 |
主要 |
4000 / 4001 |
|
|
备用 |
|||
|
TWS亚洲 - 中国3 |
主要 |
4000 / 4001 |
|
|
备用 |
mcgw1_hb1.ibllc.com.cn | ||
| TWS自动更新 | 主要 | 443 | |
|
风险漫游 |
主要 |
443 |
|
|
TWS云设置 |
主要 |
443 |
|
|
IB CAM |
主要 |
4000 / 4001 |
|
|
诊断报告 |
主要 |
443 |
|
3:网关面向账户被分配至香的服务器、但实际从中国大陆访问的客户。
IBKR Host and Ports Documentation
TWS connects to IBKR servers via port 4000 and 4001, if using SSL, and will not operate on any other port. If you are using a proxy server, it needs to be a transparent with both inbound and outbound ports open so that the TWS can function properly.
Below are listed all the gateways, along with the corresponding destination host that might be used by the TWS when you use our services, please allow access to those hosts.
The easiest way to test whether your connection needs any special setup or has been configured properly is to use IBKR's Dedicated Test page, which will provide a dynamic test of your network’s connection against our main trading and market data servers. If a “Success” response is returned, there is nothing more for you to do. If the response is “Failure”, we recommend adding an exception for the new hosts to your network’s configuration or review your changes.
Note: If your network uses a browser proxy, the test page can produce false positives. In this case, or if you are not sure what your network setup is, turn to your network administrators, who can perform ping and telnet tests to the hosts listed below to confirm compliance with the connectivity requirements.
Specs:
|
CLIENT PORTAL AND WEBSITE |
||||
|
REGION/PRODUCT |
SERVER (HOST) |
PORTS1 |
||
|
IBKR WEBSITE – AMERICA |
443 |
|||
|
IBKR WEBSITE – Canada |
443 |
|||
|
IBKR WEBSITE – UK |
443 |
|||
|
IBKR WEBSITE – INDIA2 |
443 |
|||
|
IBKR WEBSITE – JAPAN2 |
443 |
|||
|
IBKR WEBSITE – HONG KONG2 |
www.interactivebrokers.com.hk | 443 | ||
|
IBKR WEBSITE – CHINA2 |
www.ibkr.com.cn | 443 | ||
|
IBKR WEBSITE - AUSTRALIA |
www.interactivebrokers.com.au | 443 | ||
|
CLIENT PORTAL – EAST |
443 |
|||
|
CLIENT PORTAL – CENTRAL |
443 |
|||
1: Standard Communication: TCP Port 80 | SSL Communication: TCP Port 443.
2: This IB Server host does not support ping request.
Important Note: If you are accessing Client Portal from a corporate network where the Internet access is provided through a load balancing equipment, you may receive error messages about expired/invalid session and/or missing web content upon or after the login phase. The load-balancer cycles your outbound connections over two or more network interfaces to equalize the network workload. Because of this mechanism, your HTTP requests reach our systems from different IP addresses, invalidating your Client Portal session. In this scenario, as a solution, please ask your network administrator or IT group to configure your machine/device for bypassing the load-balancer. This will allow your session to remain valid and alive.
|
DESKTOP TWS |
|||
|
REGION/TOOL |
PRIMARY/BACKUP |
SERVER (HOST) |
PORTS |
|
|
PRIMARY |
|
|
|
BACKUP |
|||
|
|
PRIMARY |
|
|
|
BACKUP |
|||
|
|
PRIMARY |
|
|
|
BACKUP |
|||
|
TWS ASIA |
PRIMARY |
4000 / 4001 |
|
|
BACKUP |
|||
|
TWS ASIA - CHINA3 |
PRIMARY |
4000 / 4001 |
|
|
BACKUP |
mcgw1_hb1.ibllc.com.cn | ||
| TWS AUTO-UPDATE | PRIMARY | 443 | |
|
RISK NAVIGATOR |
PRIMARY |
443 |
|
|
TWS CLOUD SETTINGS |
PRIMARY |
443 |
|
|
IB CAM |
PRIMARY |
4000 / 4001 |
|
|
DIAGNOSTICS REPORTS |
PRIMARY |
443 |
|
3: Gateway dedicated to clients with accounts assigned to the Hong Kong server, but are physically connecting from Mainland China.